The FIFA 2022, Qatar World Cup, hosted by Qatar between November 20 and December 18, attracts the attention of cyber threat actors as well as being the center of attention of millions of sports fans. International sports competitions and similar events are indispensable targets for financially motivated threat actors. This article aims to look at the fraudulent activities and cyber threats carried out within the scope of the 2022 FIFA World Cup.
In all significant sports competitions held in recent years, there has been an increase in domain name registrations according to the names of the events and fake ticket sales. Threats targeting the 2022 FIFA World Cup include tournament-related phishing/social engineering attacks, fake malicious mobile apps that appear to be related to the event and aim to capture user data, fake ticket sales in dark web markets, and ransomware threats.
So, let’s take a look at the details of the threats mentioned.
Dark Web Analysis of Qatar World Cup
As we know, a fanatical fan wants the tickets and merchandise of their favorite teams or the football World Cup. This situation opens a wide door to possible fraudulent activities.
Threat actors on specific Deep Web/Dark Web forums have been found to sell fake tickets for the FIFA World Cup 2022 Qatar. In addition, in the Dark Web analysis, it was observed that the details of the accounts created on the platforms related to the FIFA World Cup 2022 Qatar were put up for sale.
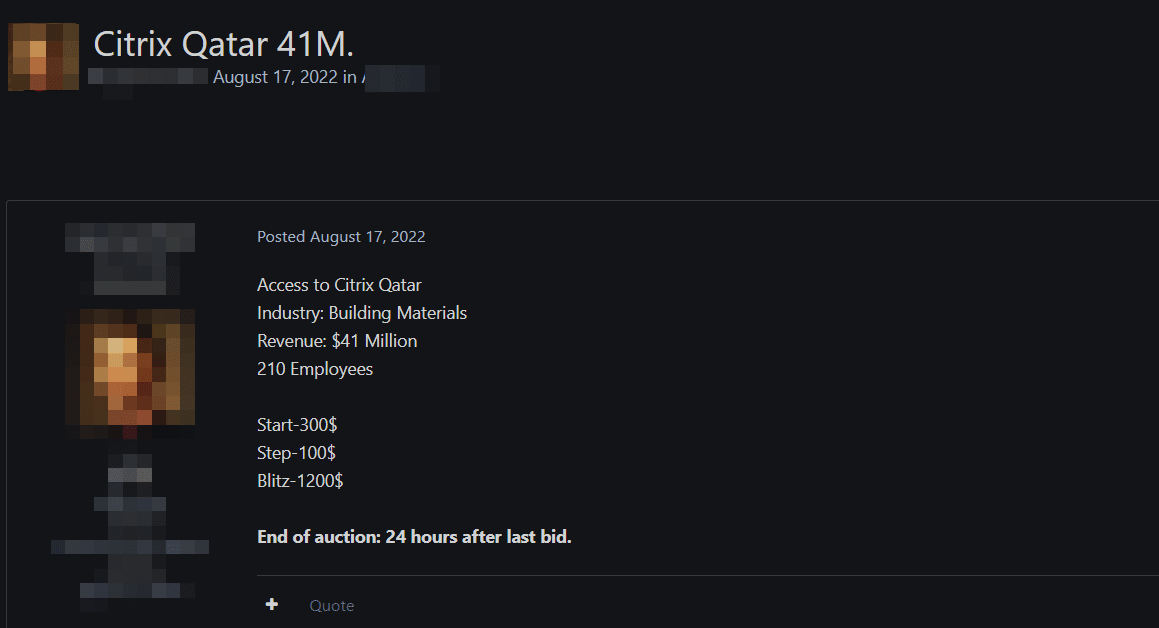
Black Market Sales
In the studies carried out in the Deep Web markets, it has been determined that the accounts of the Hayya platform, which is provided for World Cup participants to enter Qatar and access other services such as tickets and transportation, are put up for sale for a certain fee.
Black markets are the data warehouses of the Dark Web. On these platforms, data such as RDP / SSH access, account login information, IP addresses, cookies, users’ identity information, and stolen credit cards obtained through malicious software infected with victims are offered for sale illegally.

Phishing Domains
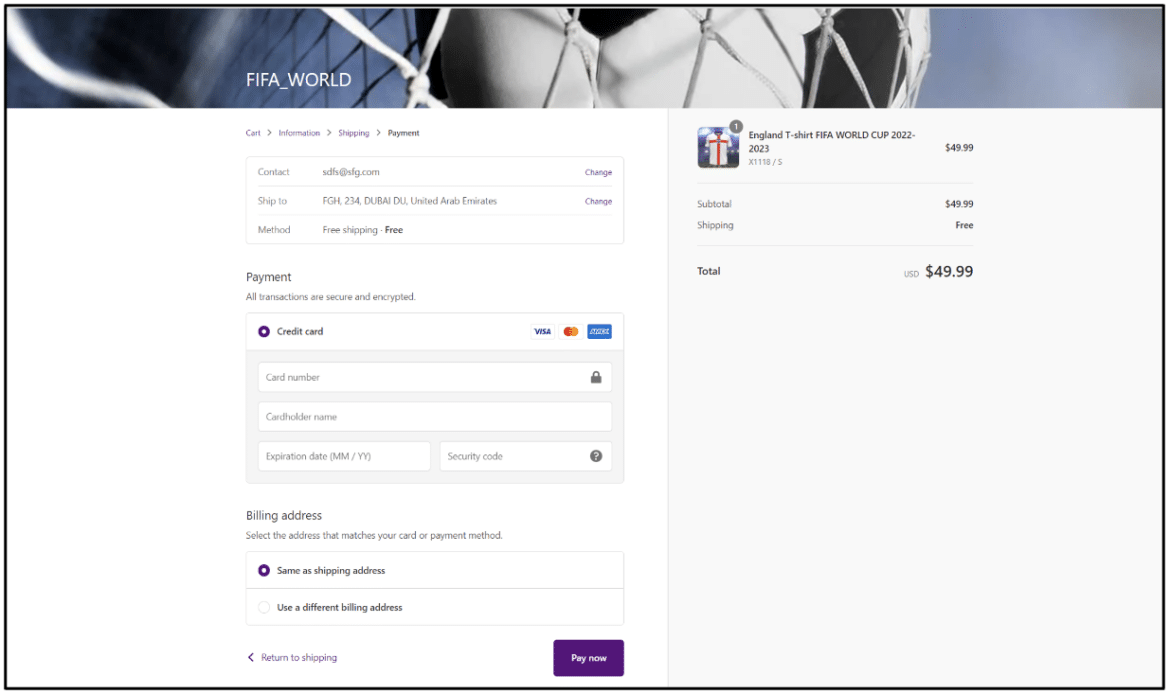
In the section we left behind, we mentioned that the fans are quite inclined to buy tickets and products for their favorite team. In this section, we will focus on phishing pages created to defraud fans with the promise of selling fake tickets and merchandise. These phishing pages imitate platforms associated with the Qatar 2022 World Cup, deceiving targets and fans.
Fake/Malicious Mobile Apps
Threat actors develop fake mobile apps to install adware, steal PII (Personally Identifiable Information) and financial data, extract cookies and credentials, and download more malware from a remotely controlled domain. More than one fake mobile application developed within the scope of the 2022 FIFA World Cup in Qatar that distributes malware has been detected.
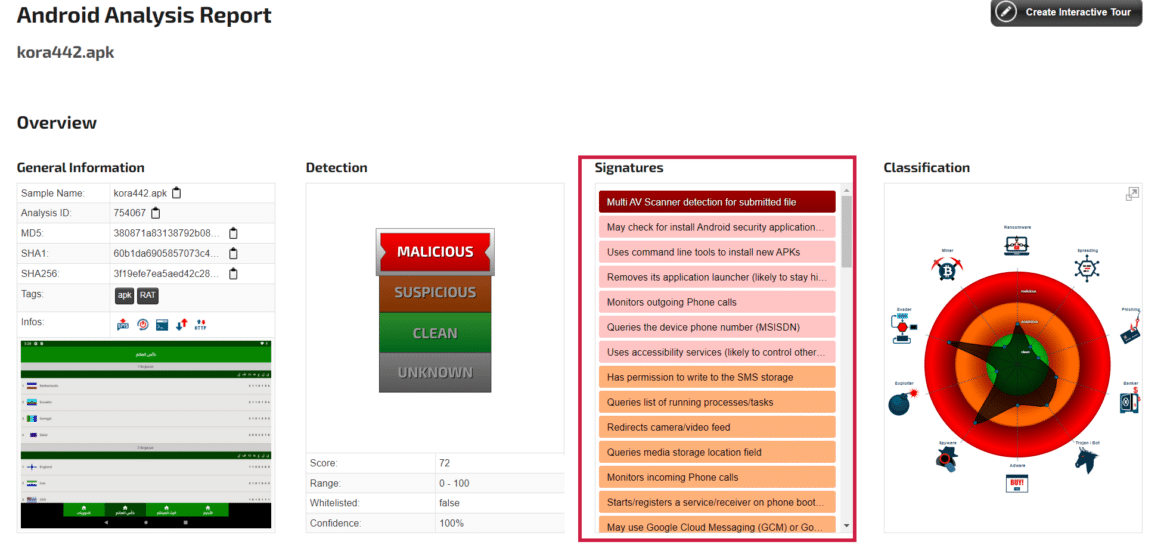
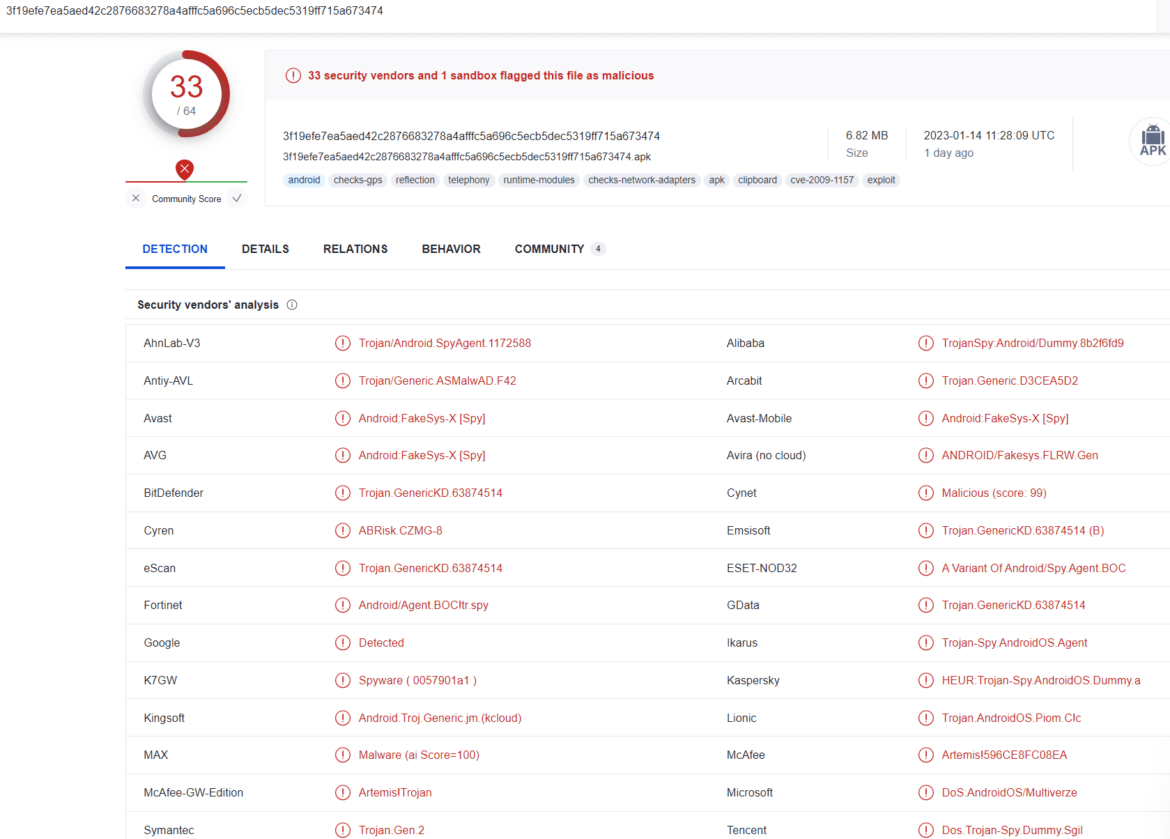
One of the fake/harmful mobile applications examined in the studies distributes AndroidRAT malware, which aims to capture user and system information on Android devices. The threat actors behind this malware have created a Facebook page called Koora 442, where users can visit and download a malicious application from a distribution site. In the posts shared on the page, it is stated that Facebook users can follow the World Cup matches live on the Koora 442 application by simply clicking on the given link. The site to which users are directed when the link is clicked requests installing the kora442.apk file on mobile devices for live tracking of the matches. If users click on the download button, AndroidRAT malware, which is responsible for capturing their data, is downloaded to their devices.
Fake Social Media Pages
Threat actors acting with financial motivation create fake social media accounts very similar to the real ones to carry out disinformation campaigns, imitate brand VIPs and managers, and carry out social engineering attacks.
Lots of social media pages have been detected impersonating assets belonging to the Qatar World Cup. Most of these pages contain harmless content. However, multiple Facebook and Instagram pages have been observed using the Qatar World Cup branding and logos to engage in fraudulent activities.
Stolen Credentials
There has been a massive increase in fraudulent sites and similar scam sites claiming to offer free streaming of FIFA 2022 Qatar World Cup matches and asking targets to enter payment card details. Legit platforms such as Xiaomi, Reddit, OpenSea, and LinkedIn have been found to contain fake links that lead to these malicious sites.
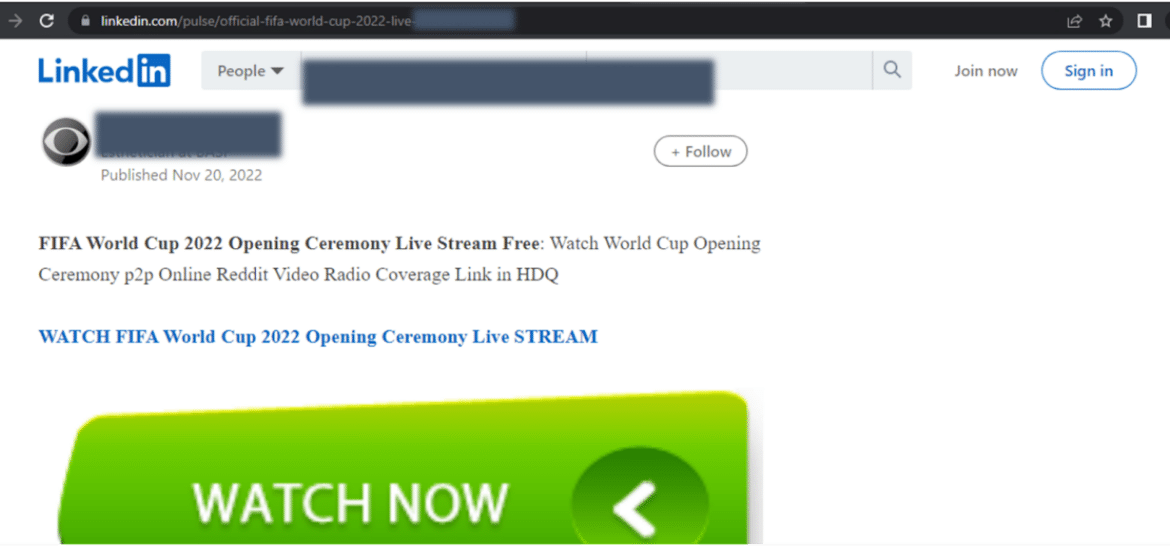
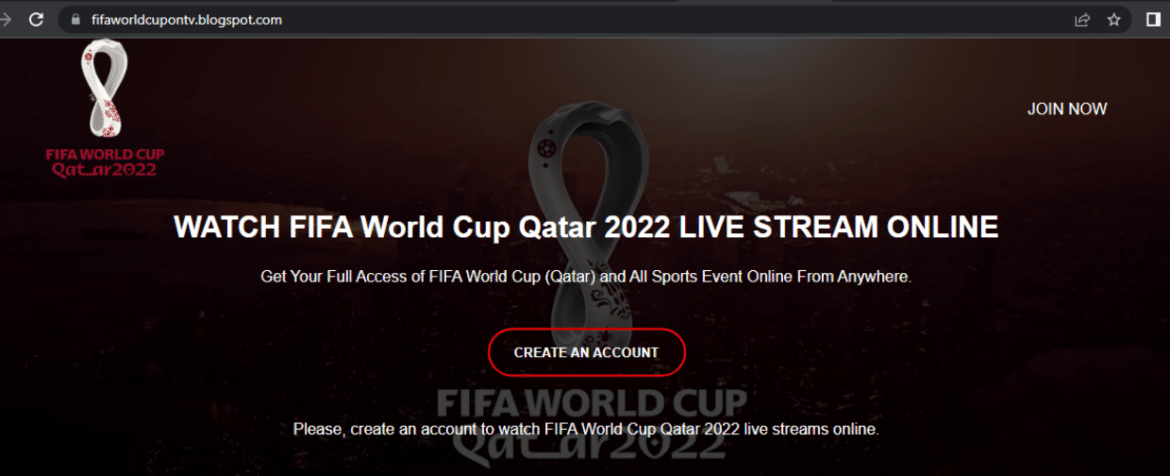

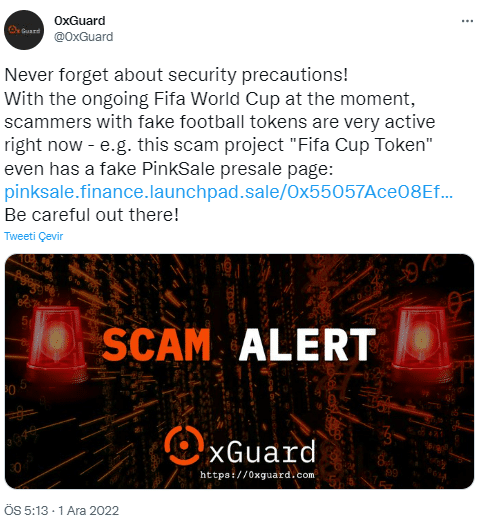
In addition to phishing pages targeting sensitive information of victims, it has been observed that threat actors create and sell fake cryptocurrency within the scope of the FIFA 2022 World Cup in order to make money directly from the targets.
Malware Activity
Malware activities targeting the FIFA 2022 Qatar World Cup have been carried out through the distribution of cracked FIFA games or through fake websites claiming to provide free streaming services.
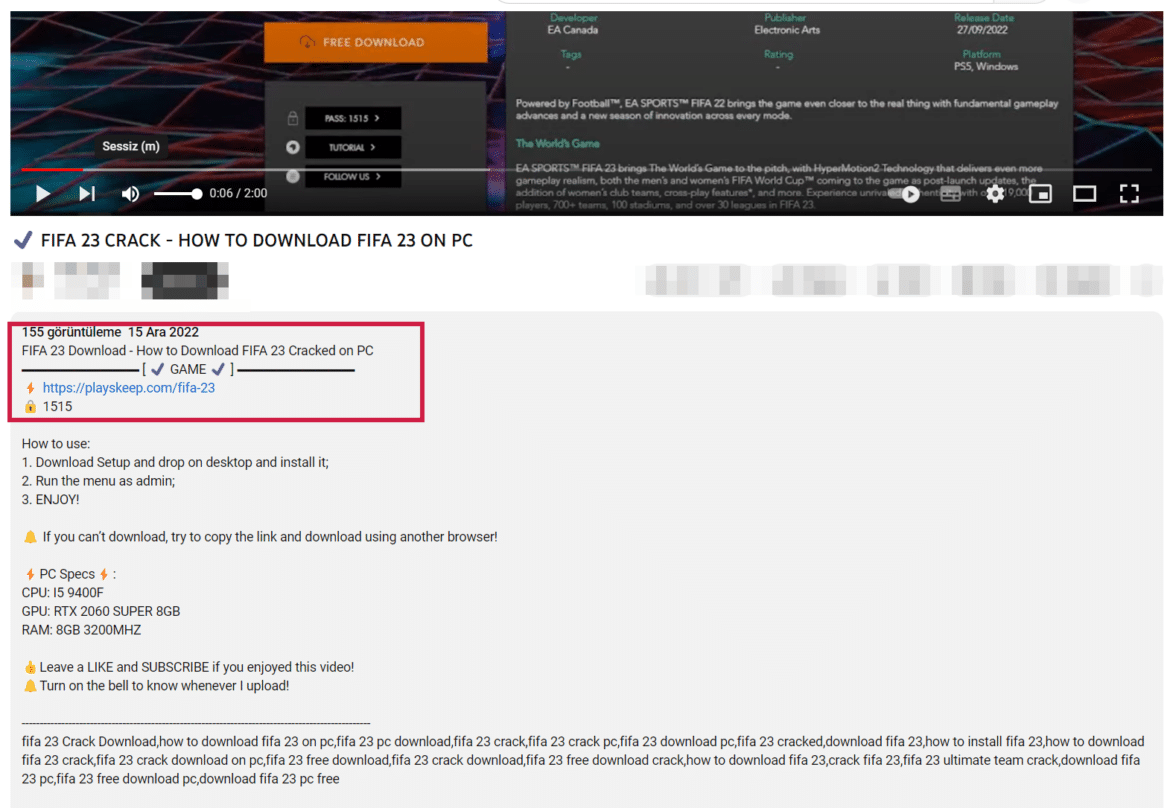
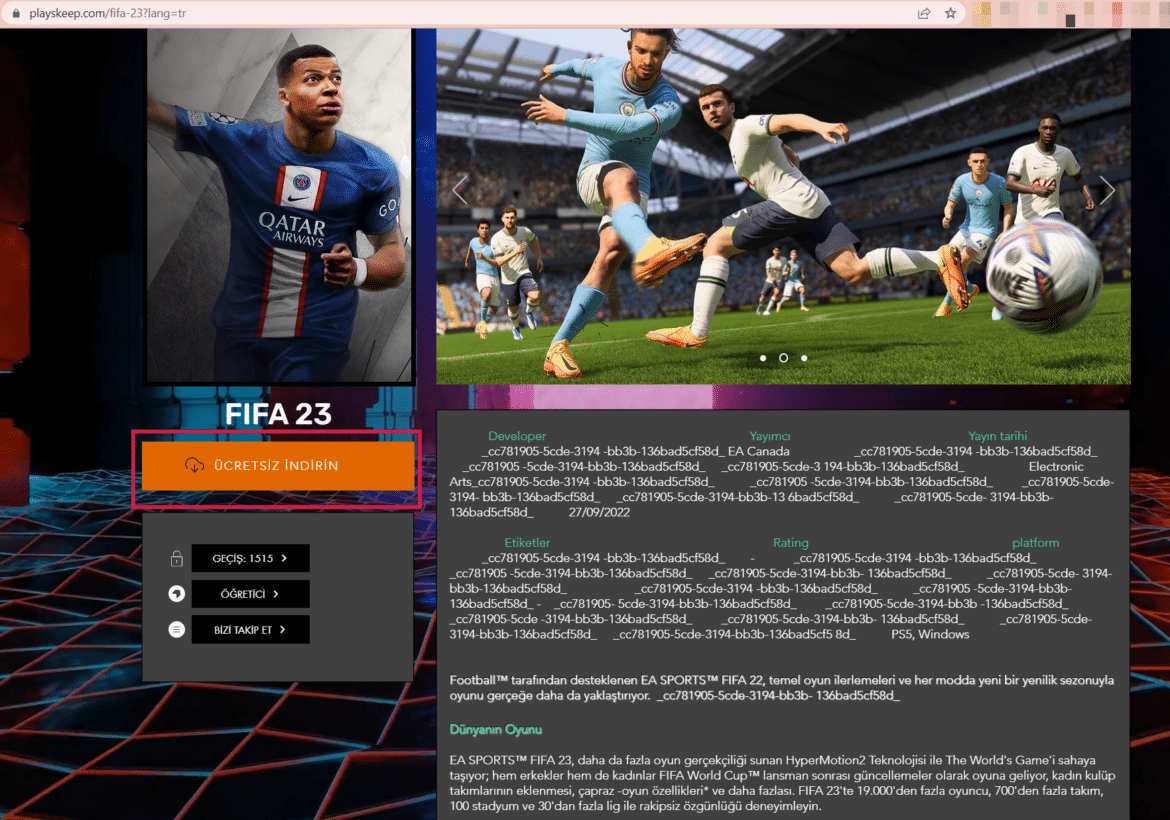
Only one of these malicious activities starts with the threat actors distributing a cracked version of the FIFA 23 game containing malware on the internet when the 2022 FIFA World Cup starts in Qatar. This game distributes the notorious RedLine trojan malware, which captures user and critical system data on the infected system.
This malicious activity was first observed in YouTube videos and comments containing cracked game download links. Clicking on the download link opens a website created for downloading the game. When the Free Download button on the site is clicked, a RAR file hosted in Mediafire is downloaded to the system. The RAR file opened on the target system contains the Redline malware.
How To Prevent These Threats with Brandefense?
Brandefense is a proactive digital risk protection solution for organizations. Our AI-driven technology constantly scans the online world, including the dark, deep, and surface web, to discover unknown events, automatically prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Our digital brand protection solution helps you quickly detect and respond to digital threats such as botnet activities, data breaches, and fraudulent activities. It allows you to identify and respond to phishing attacks, as observed in the campaigns mentioned above. For this, Brandefense keeps its finger on the pulse of 24/7 social media activities and phishing attempts.






