Introduction
Larva208 has evolved into one of the more disruptive actors to emerge in the rapidly evolving cyber threat landscape of 2023-2025. As early as 2023 they were shown to operate the financially motivated ransomware, along with setting themselves up as a hybrid actor with espionage-oriented campaigns, combining eCrime type operations with espionage/combat. As alignment to Russian interests, and targeting European government contractors and NATO organizations, is particularly alarming adversary for 2025.
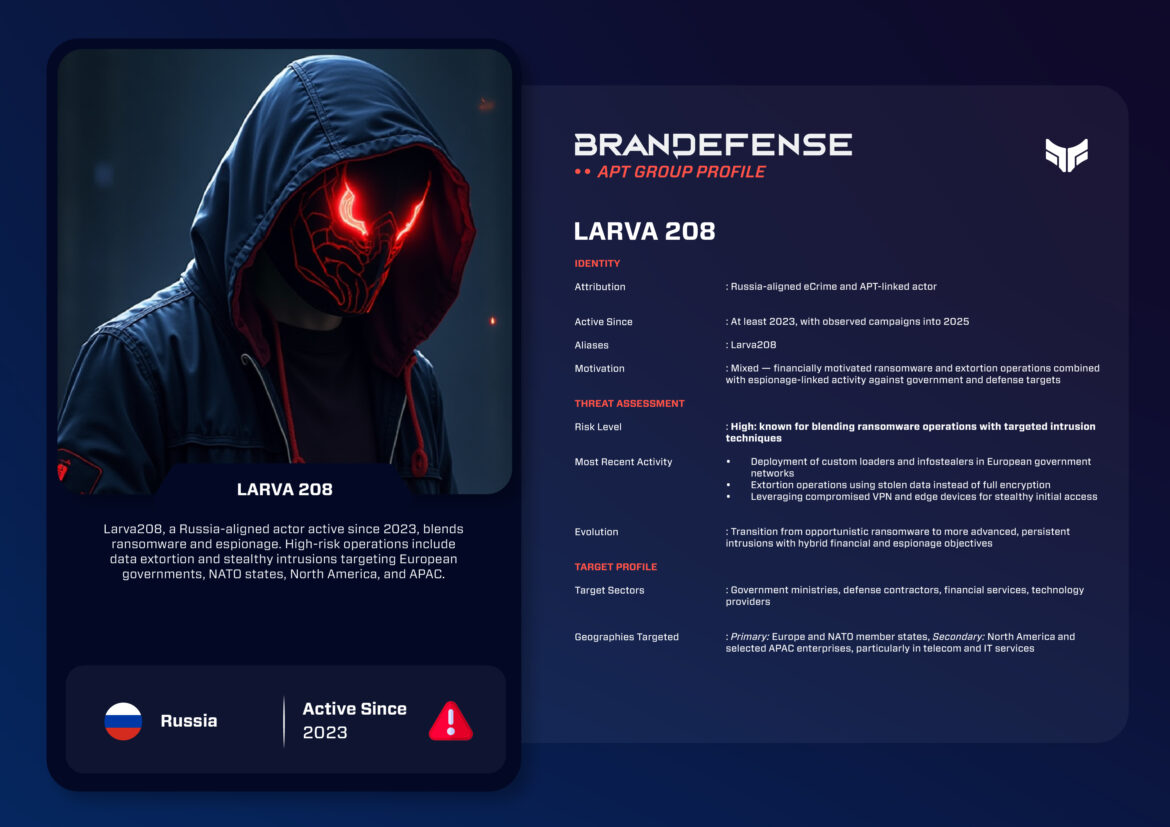
Identity and Motivation
Attribution: Russia-aligned hybrid threat actor engaging in eCrime and state-sponsored intrusion operatives
Active: At least 2023, with aggression indicating consistent increase in campaigns throughout 2024 and 2025
Alias: Larva208
Motivation: Dual motivations. “Financial gain through ransomware and extortion, as well as cyberespionage to compromise and collect intelligence against governments and defense contractors”.
Tactics, Techniques, and Procedures
Larva208 incorporated APT (Approved Threat) along with old-school cyber-criminal tactics and techniques:
Initial Access: Using VPN and edge device vulnerabilities, spearphishing campaigns using malicious attachments, and stealing credentials.
Persistence: Scheduled tasks, tunneling utilities, and stolen administrator account abuse to maintain long-term access.
C2 infrastructure: Proxy-based networks, TOR anonymization, and bitted servers used as staging points.
Malware and Tools: Custom loaders, off-the-shelf RATs, infostealers, and ransomware payload all being changed as needed for selective use.
Techniques: Data theft before encryption, selective extortion campaigns afterwards, pledging that stolen data would be used likely without a full ransomware step.
Previous Operations
2023 – Initial Ransomware Campaigns: The main opportunity was mainly financially motivated opportunistic on eastern European enterprises.
2024 – Telecom and IT Intrusions in APAC: Multiple VPN zero-day exploitations against providers to likely create footholds base for intelligence gains
2025 – European Governments Networks: Deployments of custom loaders and infostealers against ministries and later selective extortion campaigns
2025 – North America Financial services context: A series of campaigns for exfiltration of data to later demand ransom knowing that encryption wasn’t necessary for the current attack or only as a last choice showing tactical re-calibration.
Recent Developments
As of 2025, Larva208 has shifted from straightforward ransomware operations to complex blended campaigns that combine espionage and extortion, updated their models and techniques to go undetected while maximizing leverage, and has adapted into supply chain and VPN exploitation, and has made significant shifts in tactics and technique that are more plentiful than previous Russian-linked activity across various Russian fronts.
Conclusion
Larva208 continues to be a harbinger of the wave of emerging hybrid threat actors that meld traditional eCrime as represented by groups like (w)Rap and those unlikely to operationally step back from espionage – and Larva208 includes both. The hybrid strategy Larson208 exploits results in motivation and abilities as adversary characteristics, and illustrates a focus on as being a primary sophistication adversary for government and defense to monitor in 2025.
Takeaways for Defensive Action:
- Emphasize strengthening monitoring capabilities related to vulnerabilities of VPN and edge infrastructure
- Emphasize layered identity protection to protect VPN access including use of MFA and conditional access
- When evaluating all ransomware based incidents consider in the context of open source driven collection of ransomware activity, with emphasis on detection of data extraction versus encryption based ransomware
- Seek proactive defensive hunting against infostealer driven activity and custom loaders
Larva208 has illustrated that we cannot just view eCrime and nation-state based activities in separate domains. Organizations must plan for adversaries that have blended eCrime and nation-state threat capabilities as one threat.
You can download and review the sheet for all the details!






