This blog post comes from the “LockBit 3.0 Technical Analysis Report” by the Brandefense CTI Analyst Team. For more details about the analysis, download the report.
Overview
With the group’s return, Lockbit introduced Lockbit3.0, a new variant of Lockbit 2.0. LockBit 3.0 ransomware (aka LockBit Black) Based on the BlackMatter group and adopting Ransomware-as-a-Service, LockBit is an advanced version of the RaaS family. The ransomware, also called Lockbit Black, has developed itself with new extortion techniques and added the option to pay with Zcash and the existing Bitcoin and Monero crypto payment methods.
As a result of critical bugs discovered in Lockbit 2.0 in the first quarter of 2022, malware authors began adding new features to improve encryption processes and thwart security researchers.
In addition to these developments, the group announced the Bug Bounty program, breaking new ground among cybercriminal gangs. For many other cybercriminals, the program promises rewards between $1000 and $1,000,000 for the idea of bug fixing or improving existing features.
Features Changed with Lockbit 3.0
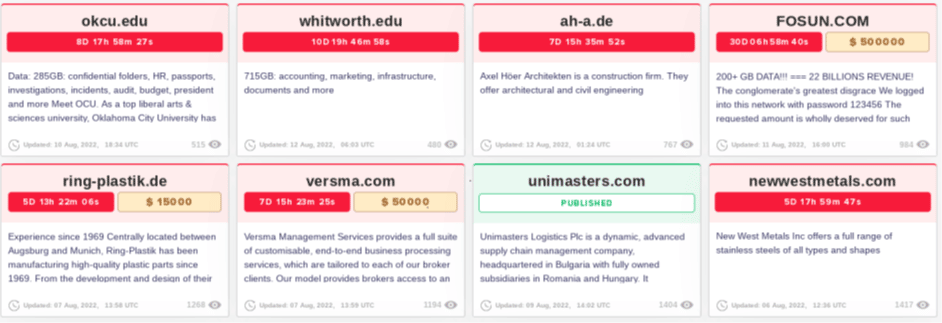
With the introduction of Lockbit 3.0 by the Lockbit gang, their operators and their gang-affiliated collaborators started to adopt Lockbit 3.0 quickly. As a result, as of June 2022, affected organizations and many affected organizations have been identified on the “Version 3.0” leak site of the leaked data.
(hxxp://lockbitapt[REDACTED]ead[.]onion)
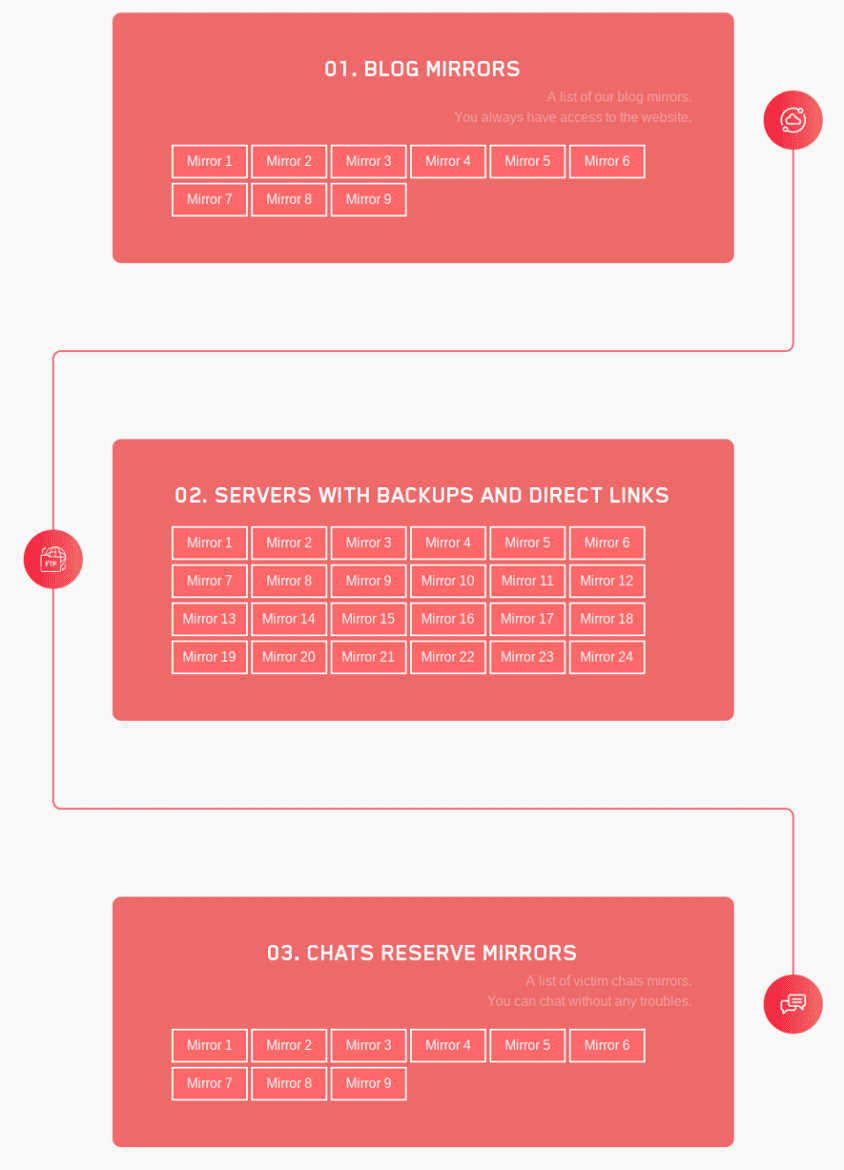
It is also aggressively releasing alternate Onion addresses with copies of the data they managed to leak to ensure continuity of announcements of leaked data and to increase resilience to interception efforts.
Another change with Lockbit 3.0 is adding a search feature that will allow a targeted organization to browse publicly published data without downloading it instantly.
In addition to its existing payment methods, Bitcoin and Monero, Lockbit has added the ability to pay with Zcash crypto. On the other hand, one of the most remarkable developments was the bug bounty program they announced.
Among the topics in the scope of the program is the detection of errors that may occur during encryption, XSS, shell, etc., found on the website. All kinds of ideas can make Lockbit more dangerous and functional, such as injections, detection of situations that may reveal the identities of collaborators, TOX Messenger vulnerabilities used for messaging, IP address learning for servers in the TOR network, root access, database dumping, and all kinds of ideas that can make it more dangerous and functional.
This blog post comes from the “LockBit 3.0 Technical Analysis Report” by the Brandefense CTI Analyst Team. For more details about the analysis, download the report.






