Introduction
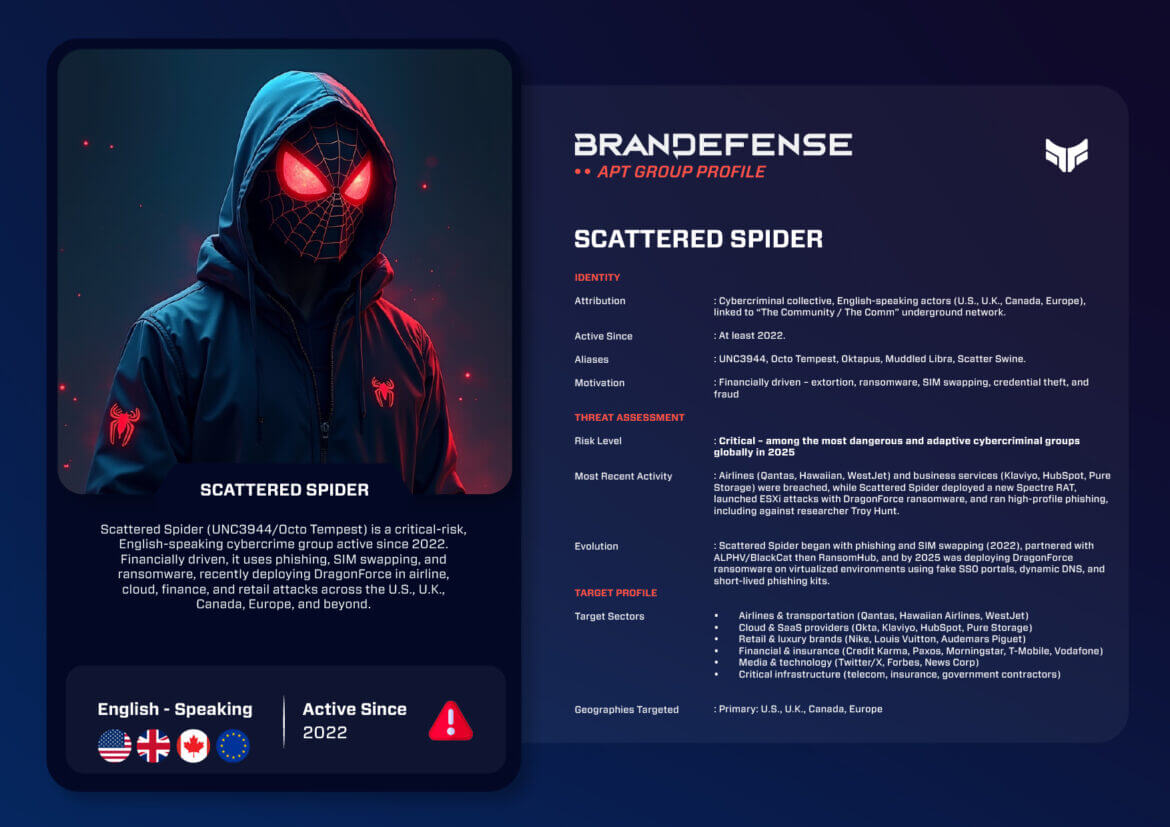
Scattered Spider, aka UNC3944, Octo Tempest, 0ktapus, Muddled Libra, and Scatter Swine, is one of the most dangerous and adaptive financially motivated groups in the cyber threat landscape in 2025.
The group is connected with the underground network often referred to as “The Comm,” and is infamous for its combination of sophisticated social engineering and ransomware operations. Following large-scale arrests in 2024, the collective continued to ramp up operations, which indicates they were able to bounce back and adapt.
Identity & Motivation
• Attribution: Cybercriminal collective primarily comprised of English-speaking actors located in the U.S., U.K., Canada, and Europe.
• Active Since: At least 2022.
• Aliases: UNC3944, Octo Tempest, 0ktapus, Muddled Libra, Scatter Swine.
• Motivation: Financial gain through extortion, ransomware, credential theft, and SIM swapping.
The group operates in a decentralized format, and them being decentralized allows them to withstand arrests to their leaders, while still being able to continue to escalate attacks in a coordinated manner across different industries.
TTPs
Scattered Spider uses a combination of living-off-the-land (LotL) techniques, commercially available tools, and their own unique malware. Social engineering at scale is still their hallmark.
• Initial Access: Phishing & smishing campaigns with fake Okta/SSO portals, dynamic DNS domains and MFA fatigue.
• Social Engineering: Voice phishing (vishing) impersonating IT staff to convince help desks to reset credentials.
• Execution: RMM tool abuse (AnyDesk, TeamViewer, ScreenConnect, Tailscale VPN) as well as the deployment of Spectre RAT and off-the-shelf malware (WarZone, Vidar, Raccoon).
• Persistence: Using malicious Identity Providers in cloud comms, privileged accounts and persistence via any VPN/RMM.
• Defense Evasion: Hypervisor-level attacks on VMware ESXi; use of proxies, rotating IPs, blending in with legitimate PowerShell/PsExec activity.
• Exfiltration & Impact: Using cloud storage (MEGA.nz, AWS S3) for exfiltration and DragonForce ransomware for double extortion (encryption + leak).
Notable Operations
• 2025 (Jul): Breach of Qantas Airways revealing 6M customers with Hawaiian Airlines, WestJet affected;
• 2025 (Mar): High-profile phishing attack against security researcher Troy Hunt using mailchimp-sso[.]com;
• 2025 (Feb – Apr): Klaviyo, HubSpot and Pure Storage targeting with an updated Spectre RAT;
• 2025 (Ongoing): ongoing deployment of DragonForce ransomware against VMware ESXi hypervisors;
• 2024: went from ALPHV/BlackCat to RansomHub after law enforcement engagements disrupted activity;
• 2023 (in September) – MGM Resorts and Caesars Entertainment breach $100M+ damage.
• 2022 – Initial SIM swapping and Okta portal phish campaigns.
Timeline of Evolution
– 2022 – SIM swapping shows up and phishing starts.
– 2023 – MGM/Caesars breaches occurred.
– 2024 – Association with RansomHub, indictments and arrests occur but they continue to operate.
– 2025 – Hypervisor ransomware (DragonForce), expand significantly in aviation and SaaS.
Recent Activity
• Newer variants of Spectre RAT with obfuscation and new C2 procedures are available.
• DragonForce ransomware targeting ESXi hypervisors to maximize damage.
• Impermanent phishing infrastructure (5-30 minutes) is difficult to detect.
• Global targeting: airlines, SaaS, retail, finance, telecommunications, and media.
These highlight Scattered Spider’s predilection for scaling social engineering, while also addressing enterprise infrastructure vulnerabilities increasingly.
Takeaway
Scattered Spider is now a dangerous global threat actor with unique advantages: native English speakers, culturally familiar with Western enterprises, and social engineering campaigns that can operate independently and, ultimately, extremely effectively. Their clear progression to hypervisor-level ransomware, and SaaS valueless credential theft campaigns, is alarming.
Defense Suggestions
• Monitor for outbound short-lived phishing domains and Okta/SSO impersonation domains.
• Strengthen MFA, prefer phishing-resistant solutions, and protect against SIM swapping.
• Restrict and monitor RMM tools (AnyDesk, Tailscale, TeamViewer).
• Determine VMware ESXi security posture against ransomware-type security events, if applicable.
• Anticipate double extortion scenarios, including negotiation playbooks.
You can download and review the sheet for all the details!







