Introduction
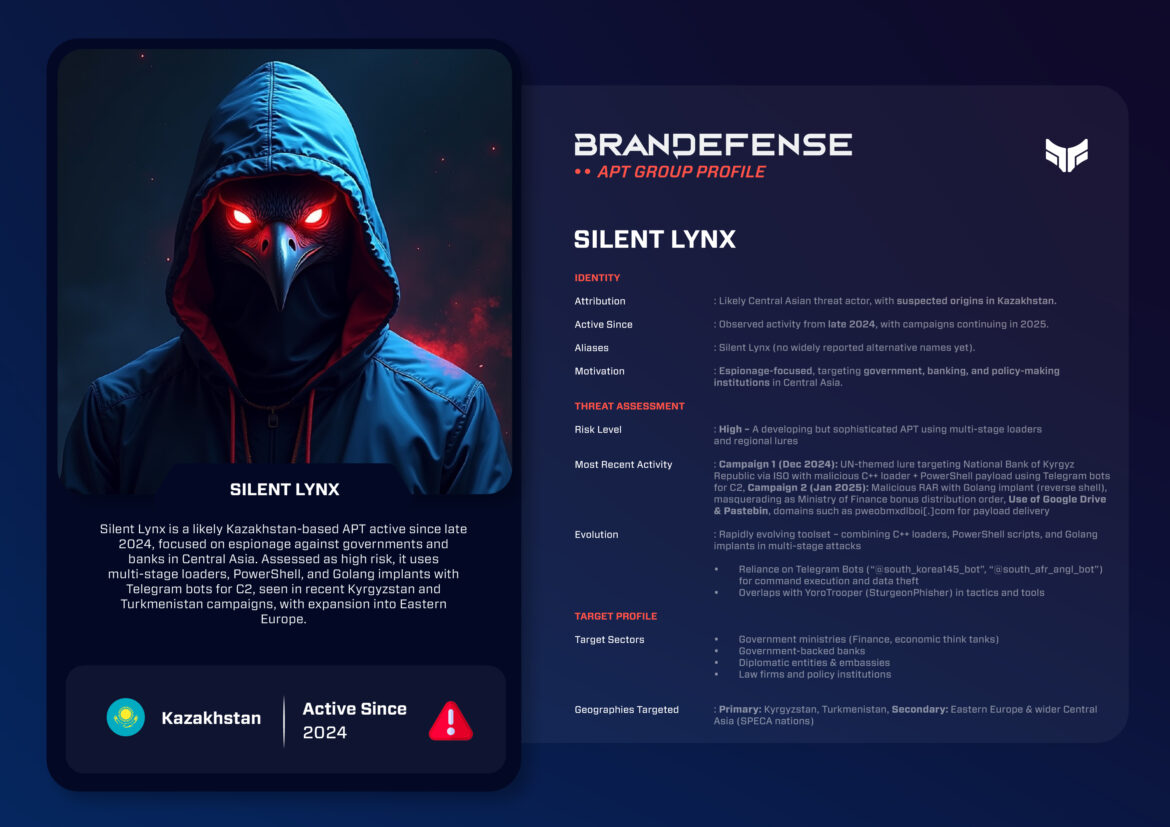
Silent Lynx is a new APT group with an espionage focus in Central Asia. Silent Lynx was sighted for the first time in late 2024 and has been active to date in 2025. It has likely operated from Kazakhstan but has targeted Kyrgyzstan and Turkmenistan, along with a few other Central Asian neighbors.
Silent Lynx is organized mainly as a espionage threat actor with an apparent regional focus, and is one of the few APT groups we see that use loaders in multiple stages, PowerShell, and Golang implants to breach high value targets ultimately to acquire sensitive information and data.
Identity and Motivation
• Attribution: Formerly a Kazakhstan based actor – with operations in various Central Asian countries.
- Active Since: Mid to late 2024.
- Aliases: Silent Lynx (unknown to have any aliases at this stage).
- Motivation: Espionage – intelligence acquired on governments, banks, and the policymakers of Central Asia.
By the exhibits it has demonstrated with its operations, Silent Lynx has a focus on the regional geopolitics and financial intelligence of Central Asia using espionage, with campaigns more targeted on the economic structures and agencies of decision making.
TTPs
Silent Lynx follows a multi-stage attack chain which incorporates social engineering and technical sophistication:.
- Initial access: Spear-phishing through advantage of RAR/ISO attachments sent by compromised accounts. The initial skies were themed around UN economic meetings and the Kyrgyz Ministry of Finance orders.
- Execution: C++ loaders that decode the embedded PowerShell scripts to create RAT capabilities. The last campaigns used Golang reverse shells.
- Persistence: Using Telegram for command channels and staged loaders.
- Defense evasion: Base64 encoding of the PowerShell commands; also the decoy documents mimicked either UNESCAP communications or typical government forms.
- Command & Control: Telegram bots (@south_korea145_bot; @south_afr_angl_bot), a custom domain (pweobmxdlboi[.]com), and a server owned by the attackers (185.122.171[.]22:8082).
- Exfiltration: Target sensitive documents were also being sent either through telegram bots or staged with Google Drive or Pastebin..
Identifiable Actions
• Dec 2024: UNESCAP-themed spear-phishing against the National Bank of Kyrgyz Republic. The ISO file included a C++ loader and PowerShell RAT controlled via Telegram bots.
• Jan 2025: Phishing campaign leveraging the Ministry of Finance; the RAR archive dropped a Golang reverse shell implant, calling home to 185.122.171[.]22:8082.
• 2025 (ongoing): Wider espionage operations expanding to Turkmenistan targeting ministries, banks, and think tanks.
Timeline of Silent Lynx Activity
– Late 2024: Initial detected, ISO-based phishing campaigns.
– Dec 2024: Financial institution targeting in Kyrgyzstan using a multi-stage PowerShell RAT.
– Jan 2025: Golang-based implants delivered in Kyrgyz state-sponsored targeting.
– 2025: Expansion of operations to Turkmenistan and regional SPECA member states.
Recent Activity
This threat actor, Silent Lynx, has established a trajectory of rapid change in their toolbox and infrastructure; from C++ loaders and PowerShell scripts to hybrid Golang implants.
This group uses Telegram as their C2 and for exfiltration, which is both non-standard and effective given their ability to remain inconspicuous in the area. There is overlap with another actor YoroTrooper (SturgeonPhisher) that has been conducting similar operations targeting CIS states with PowerShell and Golang malware.
Closing Thoughts
Silent Lynx is an emerging espionage actor in Central Asia that is developing a high level of sophistication and regional focus. They can exploit vulnerabilities of the region (open access), and relied upon accounts and trusted communication themes.
They are positioned to continue their intelligence collection against governments, primarily Kyrgyzstan and Turkmenistan, as well as banking institutions, and more.
Defensive Takeaways
• Enhance Phishing prevention – invest in filtering ISO/RAR file attachments, and train users on decoy lures.
• Monitor for C2 traffic using Telegram, this is uncommon for most enterprise environments.
• Identify outbound connections to known infrastructure (pweobmxdlboi[.]com; 185.122.171[.]22).
• Look for log entries and SIEM alerts for Base64 PowerShell Executions.
• Regional entities should be considering threat intelligence products focused on Central Asia, as they are likely to change the face of the campaign.
You can download and review the sheet for all the details!






