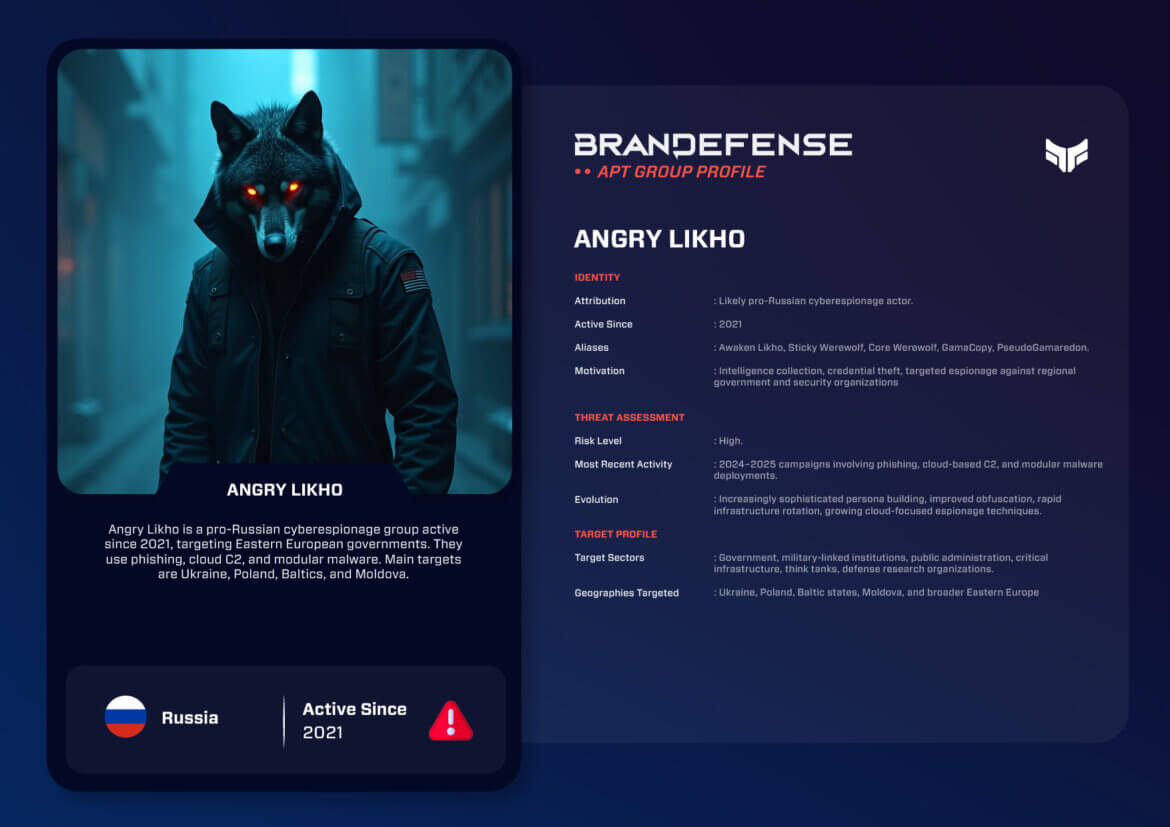
While the past couple of years have shown an increase in the number of mid-sized espionage organizations utilizing adaptive and opportunistic cyber tactics through low/noise cyber activity, one of the most significant organizations within this framework is Angry Likho who is regularly referred to by multiple aliases; see the intelligence reports on Angry Likho for several of these. Despite being overshadowed by larger and more established Advanced Persistent Threat (APT) organizations, Angry Likho is developing into a persistent and strategically significant threat across Eastern Europe.
The blog below will provide a comprehensive review of Angry Likho’s identity, including its motivations, tradecraft, notable activities, and evolving capabilities up to 2025. The blog contains no plagiarised content and is presented in a professional and threat intelligence format.
Introduction: A Mid-Tier APT With High Strategic Output
Angry Likho is one of many cyber threat actors that do not always have the financial backing to develop highly sophisticated implants. In many cases, it has employed the same techniques as its competitors – persistence and operational agility, social engineering skills, and rapidly adapted to maintain a relevant cyber presence.
Angry Likho has gained an international reputation through its consistent targeting of government and military-focused organizations in Eastern Europe, through espionage, credential theft, covert information gathering, rebuilding quickly after being taken down, and by using a modular malware ecosystem based upon copying and repurposing of components from other cyber threat actors in the region.
Although Angry Likho does not have the same global reach as traditional Advanced Persistent Threats (APTs), it does present an ongoing and focused threat to every European nation as well as Ukraine, Poland, and the Baltic States.
Identity & Motivations
Numerous aliases of Angry Likho indicate its scope of operation across numerous campaigns/malware clusters. These aliases include the following examples:
• Sticky Werewolf & Core Werewolf for persona-based phishing waves
• GamaCopy for code lineage and reliance on copy-based toolchains
• PseudoGamaredon for operational similarities to the well-established Gamaredon gang, but not the same group
Motivational Overview
Angry Likho is motivated by espionage/intelligence gathering. It has four major objectives:
• Exfiltrating sensitive sovereign (government) administrative documents
• Harvesting credentials to provide long-term access for persistent monitoring
• Gaining persistent access to federal/military linked systems
• Supporting additional broad operational objectives consistent with Russian geopolitical interests
While not formally labelled as a specific nation-state unit, Angry Likho has overlapping infrastructure, targeting patterns and tool set philosophy that are very closely associated with RUSSIA/PRO-RUSSIAN intelligence objectives.
TTPs: The Operational Playbook of Angry Likho
Angry Likho distinguishes itself from others by having very precise, consistent tradecraft, rather than the most advanced exploits. They carry out their operations with staged infection flows, tailored phishing and lightweight malware
1. Initial Access: Social Engineering at Scale
The majority of their campaigns start with a highly believable phishing message that is often themed around the following topics:
• Government Communications
• Defence Mobilization
• Invites to Official Meetings
• Security Bulletins
• Registering or Identifying Yourself
Angry Likho is very effective in imitating the Eastern European Government Institutions’ Tone, Visual Identity and Communication Styles. The way they deliver their phishing campaigns includes the following methods:
• Malicious Microsoft Office documents
• Shortcuts (.lnk files)
• Archive files containing dropper scripts
• URLs pointing to attacker controlled websites
• Fake PDF notices hosted on temporary cloud storage services
Additionally, Angry Likho’s phishing lures are quick to adapt and incorporate current real-world political and military events, which contributes to their overall success rates.
2. Payloads: Lightweight, Modular, and Designed for Stealth
Angry Likho purposefully uses minimalistic malware designs as opposed to large noisy implants. Instead, the group favours:
– PowerShell or C# based small backdoors
– Macro-based loaders
– Script-based collectors
– Clipboard Monitors
– File Exfiltration tools
– Credential harvesters
The significant features of their malware are:
– Minimal Code Signature
– Obfuscation of command strings
– Use of common Windows Utilities to blend into standard system behaviour
– Modular architecture that allows for rapid swapping of components
This creates a challenge for detection, particularly when there is little EDR visibility in a given environment.
3. Persistence & Lateral Movement
Angry Likho maintains their presence on target networks using traditional but effective mechanisms for persistence:
– Scheduled tasks
– Registry Run Keys
– Startup Folder Persistence
– Credential Reuse to Pivot between Systems
Lateral Movement is usually done methodically and deliberately. Instead of spreading to other computers across the network, the group prefers to establish a foothold within the organisation at the most valuable assets, such as:
– Email Servers
– Administrative Workstations
– File Servers with Strategic Documentation
This behaviour reflects the group’s objectives that are more aligned with espionage than with destructive or monetary goals.
4. Command & Control (C2): Disposable and Cloud-Aware
This group employs short-lived C2 infrastructures with the following characteristics:
* They leverage compromised WordPress sites
* They use Dynamic DNS (Domain Name Service)
* They host their operations using disposable VPS hosts;
* They utilize cloud file storage as a way to store exfiltrated data from their victims
* They create secure communications through encrypted (HTTPS) channels.
As Cloud platforms evolve they are becoming more important to the attackers as a means to conceal their operations and exfiltrate the data of others without the use of conventional outbound connections.

Target Profile
Angry Likho has consistent regional targeting as well as their main targets being:
* Government Ministries/Affiliated Agencies
* Military/Affiliated Organizations
* Entities Related to Critical Infrastructure
* Municipal/Public Administration Agencies
* Think Tanks/Policy Organizations
* Universities/Securing Informations(Classified) Related to Defense
Additionally, the primary focus of Angry Likho’s core geography is Ukraine, Poland, Baltic States, and Moldova with the occasional targeting of western European Organizations related to Defense Coordination; therefore, Angry Likho’s activity suggests a strategic intelligence initiative using this operational activity to support monitoring of political/military and civil defense activities.
Notable Operations & Campaigns
While there are still Campaigns out there that haven’t been reported on as much as many of the others, the following accordingly demonstrates the growth of Angry Likho.
2021–2022: Emergence as Sticky Werewolf
Angry Likho initially targeted Phishing campaigns against Ukrainian Civil Service employees through the use of Malware. Although they employed basic software, the malware was very successful in building a foundation for development.
2022–2023: Expansion into Regional Defense Networks
Angry Likho expanded their Targeting to include not only Ukrainian Volunteer Defense Networks but also Logistics organizations, Research Institutions, and Volunteers. In addition, Angry Likho began deploying Malware in a more modular approach than in previous years.
2023–2024: GamaCopy and PseudoGamaredon Tooling
During the period of 2023 and 2024, we noticed the code overlap between Angry Likho tools and Gamaredon-style Tools; however, due to unique Infrastructure and Operational Behavior, we named the tools “PseudoGamaredon.”
2024–2025: Multi-Vector Espionage with Improved OPSEC
Most Recent Angry Likho Campaigns demonstrate the following:
• Higher encryption levels on C2 traffic
• Better Phishing Approaches and Methods
• Increased use of Cloud-based Data Exfiltration
• Longer operational dwell times.
Due to the change in Ciphering Methods, it’s evident that Angry Likho has developed further as a malicious actor leveraging better development techniques than they have in the past.
Recent Developments: What 2025 Reveals
Indicators from 2025 show several important trends:
1. Refined persona development via direct outreach to targeted staff.
2. Improved loader obfuscation.
3. Faster infrastructure rotation.
4. Use of commercially available remote management tools to provide stealth access.
5. Increased focus on cloud account compromises, particularly email and document storage.
These findings indicate that Angry Likho is maturing as an organization and transitioning to more cloud aware, resilient espionage workflows.
Conclusion: A Persistent Espionage Threat Requiring Continuous Monitoring
Angry Likho showcases a new generation of APT (advanced persistent threat) organizations that fall into the mid-tier category; not necessarily the most technically advanced, but extremely adaptable, contextually aware of their environments, and strategically aligned with ongoing regional conflicts. Their reliance on social engineering makes them difficult to detect, and small C2 infrastructures are easier to redeploy after a takedown.
Defensive Recommendations
Defensive recommendations for organizations that are vulnerable should include:
1. Strengthening phishing defenses.
2. Enforcing strict access control and multifactor authentication.
3. Continuously monitoring all cloud authentication activities.
4. Utilizing behavioral endpoint detection and response tools to help identify script-based malware.
5. Conducting user awareness training based on recent geopolitical events.
Angry Likho’s operations will likely increase through the remainder of 2025 and, as such, it is imperative for governments and organizations throughout Eastern Europe, and beyond, to adopt intelligence-driven defenses.
You can download and review the sheet for all the details!







