Introduction
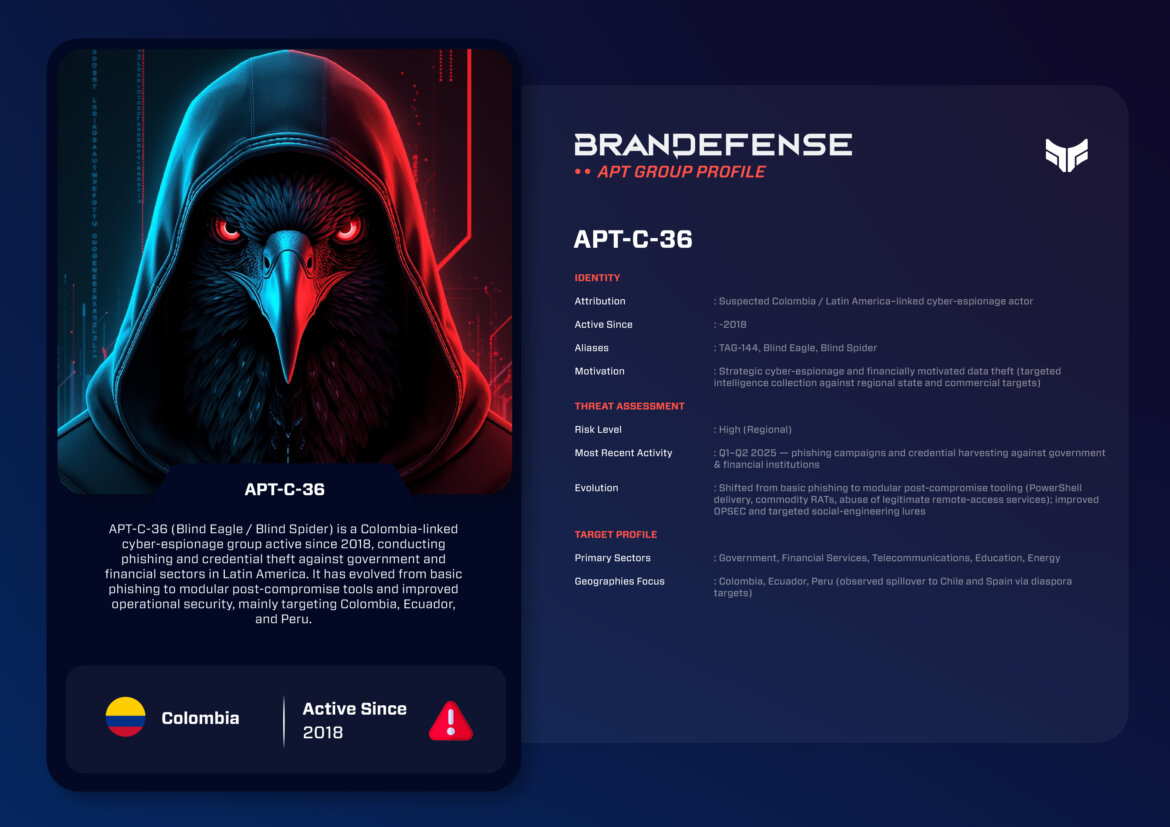
APT-C-36, also known as TAG-144, Blind Eagle, and Blind Spider has emerged as one of the most staunch cyber-espionage actors in Latin America. Active since approximately 2018, the group has been noted for targeting government and financial entities in South America. Different from many advanced persistent threat groups of global powers, APT-C-36 operates within an operationally distinct context from cyber threats and blends operational objectives with espionage motivations as financial-driven campaigns. The group’s evolution is a reflection of the maturity of Latin America in cyber actors and emphasizes the importance of local cyberspace activities in global threat intelligence.
Identity and Motivation
It is suspected that APT-C-36 operates out of Colombia, or at least primarily within the region. Its activities indicate a hybrid form of motivation: collecting intelligence for political and strategic purposes and stealing money to fund operations. The group focuses on, but is not exclusive to, targeting government ministries, financial services, telecommunications providers, and educational institutions. Phishing is the group’s signature methodology, but recent activity shows greater dependence on living-off-the-land methods and commercially available remote access tools (RATs), such as AsyncRAT, QuasarRAT, and BitRAT.
The actor’s stated motivations fall under two broad categories: 1. Espionage: Collecting intelligence from government and critical infrastructure networks. 2. Financial Gain: Stealing credentials and sensitive data from banking and corporate networks for financial purposes.
APT-C-36’s operations suggest an opportunistic component as it often impersonates tax authorities, law enforcement, or telecommunications companies to entice targets to launch malicious payloads.
Tactics, Techniques, and Procedures (TTPs)
APT-C-36 typically operates with a focus on simplicity, consistency, and flexibility. The group may not be as technically advanced as leading advanced persistent threats, but their familiarity with local socio-political contexts offers them a significant strategic advantage.
Exfiltration and Impact: The primary objective is data theft. Stolen credentials are either employed for additional access, or subsequently exposed for sale on dark web markets. The group’s attacks have disrupted operations across government institutions and private sector companies alike.
Initial Access: Spearphishing continues to be the main mode of access. The group sends emails that pose as government tax notifications or legal documents, often containing malicious PDF or ZIP attachments. Some effects include links that lead to counterfeit credential-harvesting sites.
Execution and Persistence: Once the victim accesses the attachment or link, a PowerShell-based script is executed to download the second stage payload. Persistence is established by means of scheduled tasks, registry changes, and abuse of legitimate remote administration tools.
Command and Control (C2): APT-C-36 employs HTTPS-based communications, VPNs, and dynamic DNS services to obfuscate their infrastructure. They frequently use cloud services and remote administration tools to blend any malicious activity in with normal network traffic.
Malware and Tools: The group utilizes a combination of open-source and commodity RATs—AsyncRAT, QuasarRAT, njRAT, and BitRAT—along with custom droppers designed to evade local antivirus solutions. These RATs facilitate remote access, credential theft, and document exfiltration.

Notable Operations
Over the years, the APT-C-36 group has adapted its tactics, while maintaining a consistent tempo of operations in South America:
- 2023 – Tax Authority Phishing Campaign: The group impersonated Colombia`s DIAN (Dirección de Impuestos y Aduanas Nacionales) and sent phishing emails with PDF attachments to recipients. The payload leveraged AsyncRAT to extract credentials from government employees.
- 2024 – Financial Institution Breach: A new wave of phishing emails targeted banking networks in South America. The emails used fake legal notifications as lures and compromised credentials allowed lateral movement within internal banking systems, which resulted in data exfiltration.
- 2025 – Public Sector Espionage Campaign: Recent intelligence suggests that APT-C-36 conducted operational spearphishing campaigns within Colombian ministries. The spearphishing attacks were conducted utilizing PowerShell loaders and encrypted C2 channels, indicating a shift to a more stealthy and sustainable approach.
The operations show that the actor is not only engaging in espionage or financial theft, but he understands local government bureaucratic flows and communication norms on a competitive sophisticated level.
Recent Developments and Evolution
The latest reports on the group’s threat intelligence from 2024–2025 indicates that APT-C-36 continues to evolve and change within the cybersecurity space. The group has added operational security (OPSEC) improvements, such as:
- Infrastructure rotation: Frequent new domain registrations and temporary servers to avoid blacklisting.
- Encryption: Usage of HTTPS and cloud-based C2 communications to enhance stealth.
- Tool diversification: Use of more commodity malware versus custom software reduces traceability and lowers development costs.
ESET and several regional intelligence firms reported the group being implicated in APT-C-36 campaigns amidst broader regional phishing waves throughout Latin America. This points to either regional affiliate behavior or shared infrastructure – suggesting the development of a semi-organized cyber crime ecology.
The tools the APT-C-36 group chose to use and the exploitation techniques they chose (through social engineering) showcases their lack of global threat sophistication versus their regional relevance. The localization – using culturally familiar institutions and regionally common dialects – allows them to be very effective in their campaigns against Latin Americans and their regional institutions as user sophistication and institutional defenses vary across Latin America.
Strategic Impact and Defensive Takeaways
APT-C-36 is a manifest of a growing class of regionally driven APTs that straddle the line between espionage and financially motivated activity. In remaining successful, it indicates that regional actors can sustain long-duration campaigns, while applying minimal resources by exploiting social trust and utilizing publicly available modules.
There are a number of clear defensive implications:
- Localized Awareness Campaigns: Organizations in Latin America should develop and support awareness training focused on the local landscape of phishing techniques for government impersonation attacks.
- Behavioral Detection Over Signature-Based Security: To detect commodity malware, focus on behavioral based indicators of attacks such as PowerShell execution that is abnormal or signs of command and control connections.
- Network Segmentation and Zero Trust Models: Through segmentations, the lateral movement is limited. Focusing on a Zero Trust model is important to monitor user activity and privilege escalation activity.
- Regional Intelligence Sharing: Work together as Latin American CERTs and private sector organizations to disrupt APT-C-36’s infrastructure and identify overlaps quickly.
Conclusion
APT-C-36 (Blind Eagle) embodies how a regional threat actor can develop into a persistent, adaptive, and effective espionage effort. Its campaigns reflect a nuanced understanding of the socio-technical environment in Latin America and demonstrate a pragmatism for resource utilization. Presently, in 2025, APT-C-36 remains an active and maturing threat potentially because of exploitation or exploitable malware, but rather because of their persistent in-context targeting and social engineering abilities.
For cybersecurity professionals and policymakers, this group represents a case study example of the enhanced significance of regional APT ecosystems. It exemplifies that localized defense strategies, information sharing, and investment into user awareness are all necessary to combat threats that arise from within the same cultural and linguistic context that they exploit.
You can download and review the sheet for all the details!







