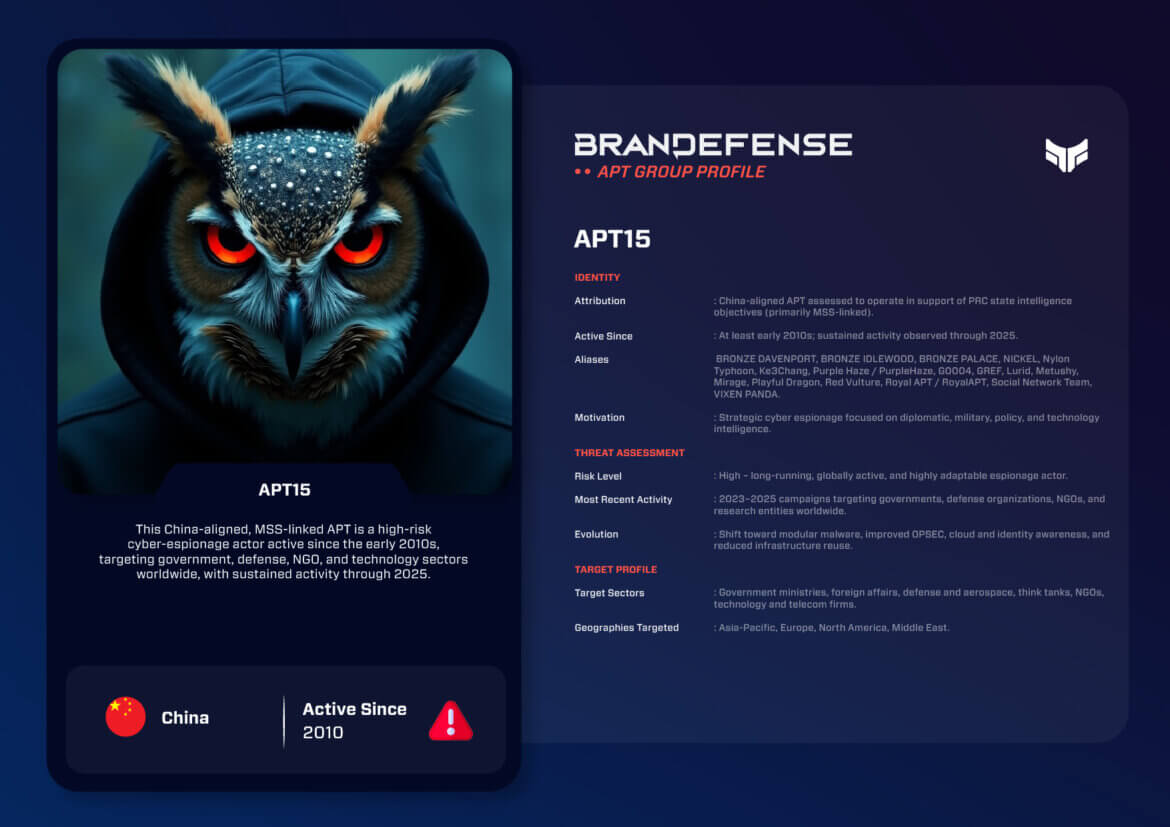
APT15 otherwise known as BRONZE DAVENPORT, BRONZE IDLEWOOD, BRONZE PALACE, NICKEL, Nylon Typhoon, Ke3Chang, Purple Haze / PurpleHaze, G0004, GREF, Lurid, Metushy, Mirage, Playful Dragon, Red Vulture, Royal APT / RoyalAPT, Social Network Team and VIXEN PANDA is one of the longest running, most complex China-aligned advanced persistent threat (APT) Groups. The organization has operated for over a decade and has been tracked under a multitude of different aliases representing an extensive ecosystem of interrelated campaigns, rather than a single, static entity . Its longevity, variety of tools used and global reach on its targets signify the group’s contribution within the larger Chinese cyber espionage environment. The major focus of APT15 has remained on gathering intelligence rather than engaging in disruption or financial cybercrime, and therefore closely aligns itself with China’s diplomatic, military and strategic interests . The following blog post is a 1000-word intelligence style analysis of APT15 that outlines their identity, motivations, cyber operations and Strategic Impact.
Identity & Attribution
APT15 (sometimes referred to by other names) is thought to be associated with the Chinese state, given APT15’s close relationship to such entities as the PRC Ministry of State Security. As APT15 has been tracked over time, numerous security vendors and research agencies have tracked the same or similar activities, leading to large numbers of aliases associated with the APT15 actor.
While different names have been used to describe APT15 activity, there are several characteristics which can be found across all APT15 activity:
– Long-term, intelligence-based campaigns
– Predominantly government and diplomatic targets
– Consistent use of specially developed malware types
– Patience and operational security
APT15’s primary focus is strategic cyber espionage, with the goal of obtaining information needed to support Chinese foreign policy, defense planning, domestic security goals, and expanding China’s influence in the region. APT15 has little to no interest in financial gain, and does not participate in destructive operational activities.
Tactics, Techniques, and Procedures (TTPs)
APT15 demonstrates mature and adaptive tradecraft, combining traditional espionage techniques with continuous technical evolution.
Initial Access
APT15 often gains access through the use of: Targeted email phishing campaigns to diplomats, officials and researchers. These emails are themed around government relations, policy, conference invitations and media requests. Weaponized documents that are designed to exploit known vulnerabilities or take advantage of trusted document formats. Sometimes they are able to compromise exposed internet-based services, especially in government networks.
The volume of these campaigns is low, but they are highly contextualized based on the fact that APT15 conducts extensive reconnaissance on their targets.
Execution & Malware Tooling
When APT15 has successfully established an initial point of entry into the target network, they deploy a variety of custom and semi-custom malware programs, including: Ke3Chang (backdoors that allow for remote command execution and data theft), modular loaders that can directly execute payloads from memory, credential harvesting tools that are aimed at browsers, email clients and operating systems as well as proxy and tunneling solutions that provide lateral movement within the environment, as well as covert access.
The malware developed by this group is frequently modified and/or recompiled to avoid signature-based detection.
Persistence
APT15 utilizes multi-layered persistence methods to maintain long-term access to compromised hosts, including: Registry autorun keys and scheduled tasks, DLL sideloading by using validly signed executables, installation of services presented as benign system components, as well as redundant persistence routes that allow the group to survive cleanup operations.

Command and Control (C2)
The Command and Control (C2) infrastructure of APT15 has the following characteristics:
1. Resilience and Stealth:
– HTTPS Communications are encrypted and blended with normal web traffic
– Use of Compromised Servers and Dynamic DNS Services
– Frequent Rotation of Domains and IP Addresses
– Multi-hop Proxy Chains to Obfuscate the Operator’s Location
2. C2 Traffic Volume:
– C2 Traffic is kept to a Low Volume, which decreases the likelihood of triggering Network-Based Alerts
Defense Evasion
Defense Evasion is one of APT15’s Primary Strengths:
– Obfuscation and Encryption of Malware Payloads
– Utilizing Native System Tools for Living off the Land Techniques
– Minimal Reuse of Malware Artifacts and Infrastructure
– Timing of Execution of Operations to Avoid Peak Monitoring Times
The techniques used to evade detection also make APT15 difficult to detect by traditional security controls.
Data Collection & Exfiltration
While APT15 does not perform every type of data collection and exfiltration, it is focused on collecting Intelligence Value, rather than Bulk Data Theft. Examples of Targeted Data Collections include:
1. Communications from Government to Government
2. Documents Maintaining Strategy
3. Research
4. Credentials and Access Preparation for Future Operations
All of the collected data is Staged, Compressed, Encrypted, and Slowly Exfiltrated to Avoid DLP (Data Loss Prevention Equipment) and Anomaly Detection Systems.
Notable Operations
Numerous high profile espionage campaigns have been carried out by APT15 for many years now.
Diplomatic and Government Espionage
APT15 has consistently attacked foreign ministries, Embassies and inter-governmental organisations. By breaking into these institutions, APT15 was able to obtain information related to diplomatic negotiations between China and its allies as well as other policy discussions concerning China.
Defense and Security Sector Targeting
APT15 continues its targeted attacks on defence contractors and security-related entities. As a result of these security breaches, APT15 has gained access to sensitive military strategy documents, research data, and communications regarding military modernisation and regional security.
NGO and Think Tank Surveillance
APT15 has targeted think tanks, NGOs, and academic institutions involved with studying China, regional conflict, and human rights issues in order to further PRC’s objectives in the area of internal security and narrative management.
Global Reach Campaigns
APT15 has been linked to APT15 activities that span the globe, spanning Asia Pacific, Europe, North America and the Middle East, indicating that APT15 has a global operational presence.
Recent Developments (2022–2025)
APT15 has continued to develop and demonstrate increased sophistication in operations over the last few years. Specifically, there has been an increase in the use of unique campaigns for each of their active operations that is not typical of their prior operational security practices. APT15 has also increased the complexity of their malware frameworks, making them more modular in design and enabling the creation of tools specifically designed for specific targets (i.e. based on their target’s characteristics). Furthermore, APT15 has created a hybrid approach to targeting systems that are located in both on-premises and cloud environments (e.g. identity and endpoint access instead of focusing solely on the exploitation of networks). Finally, while many APTs associated with the People’s Republic of China (PRC) have been publicly exposed and are becoming less active, APT15 continues to be active and has no indications of slowing down in terms of strategic tasking.
Strategic Impact
APT15’s significance to China’s long-term strategy for collecting intelligence from foreign sources cannot be overstated as there are several ways in which the group can aid the PRC in collecting information related to its political and diplomatic goals, conducting military operations, developing emerging technologies, and monitoring specific NGOs and think tanks that represent competing viewpoints or interests. Hence, APT15 will always remain at the forefront of China’s strategy of targeting foreign government entities for intelligence collection due to their continued existence and the amount of information collected by APT15..
Conclusion
APT15, which has also been called BRONZE DAVENPORT, NICKEL, Ke3Chang, Nylon Typhoon, VIXEN PANDA, and various other names, is one of the most flexible and long-lasting China-oriented cyber intelligence organisations. With APT15’s vast capacity for adaptability, hidden operation and worldwide activity for longer than ten years, both the technical development of their tools and the importance of the strategy of this organisation has never been more pertinent. It will continue to stay a prominent risk as we enter into a time of greater international competition and where digital infrastructure is becoming an even more critical component of national powers, in order to mitigate risks of such an organisation requires significant workforce, enhanced behavioural detection, aggressively patching and an ongoing threat intelligence programme. More so, corporations should realise that the most dangerous adversaries are those who may go about their operations in a very stealthy manner, taking calculated risks and with strategic purpose.
You can download and review the sheet for all the details!






