Introduction
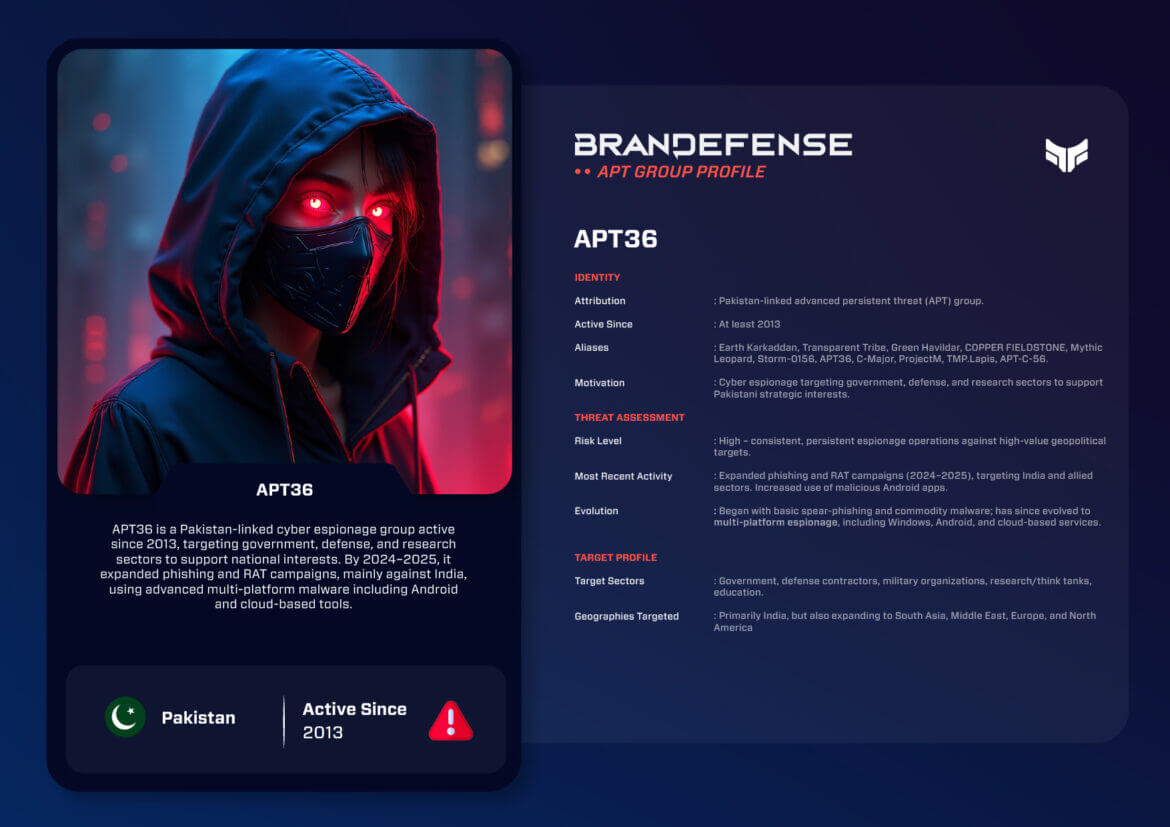
In the changing dynamics of global cyber conflict, state-linked advanced persistent threat (APT) groups continue to have a central part in espionage and influence missions. Of those, Operation C-Major, more commonly known as APT36, has continued to remain relevant due to its persistence, adaptability, and targeting of strategic intelligence collection. Following a sequence of different names Transparent Tribe, Earth Karkaddan, Green Havildar, Mythic Leopard, COPPER FIELDSTONE, Storm-0156, ProjectM, and TMP.Lapis APT36 is still a high-priority adversary for defenders in the government, defense, and research sectors.
This blog post intends to look at APT36’s identity, motivations, tactics, operations, and recent activities, creating an organized understanding of APT36’s long-term relevance to the global cybersecurity landscape.
Identity and Motivation
APT36 has been active since at least 2013, and it is generally attributed to operators based in Pakistan. APT36 members have an overarching goal of cyber espionage, primarily towards institutions and individuals related to strategic interests of South Asia, specifically India.
APT36’s motivation is geopolitical:
- Collecting military and defense focused intelligence against competing nations
- Monitoring policy and research missions
- Building regional influence by infiltrating educational, governmental, and strategic organizations
In contrast to ransomware actors seeking financial gain, APT36 is an intelligence-gathering operation for the long haul. This level of persistence can be more dangerous than financially motivated ransomware actors that may yield an initial attack; in many cases, the attacker wants the victim to remain unaware of the attack for as long as possible.
TTPs (Tactics, Techniques & Procedures)
APT36 possesses an assorted, but recognizable, toolkit. While the tactics evolve, some tactics have been consistent throughout.
- Initial Access:
- Spear phishing emails with malicious file attachments disguised as documents from defense or government agencies.
- Fake job offers intended for defense, government, and academic targets.
- Malicious Android apps that mimicked legitimate tools or government apps.
- Persistence:
- Creates scheduled tasks or registry modifications.
- Deploys trojanized software to establish long-term footholds once other means of persistence have been removed.
- Command & Control (C2):
- Uses HTTP/S, dynamic DNS, and cloud service for communication.
- Use encrypted communications to evade detection.
- Malware and Tools:
- CrimsonRAT: A remote access trojan that has been APT36’s flagship RAT for years, they have been using variations of this since the early days of the group.
- ObliqueRAT: An emerging RAT delivered via compromised websites and phishing attachments during the same time CrimsonRAT began emerging.
- CapraRAT: An Android surveillance tool.
- Various custom Android spyware apps to collect data from mobile devices.
- Techniques:
- Exploitation of Office macros and PDF exploits.
- Use of social engineering tactics to target military and academic personnel.
- Data exfiltration using encrypted communication.
The information in the TTPs demonstrates APT36’s capacity to integrate inexpensive phishing-based techniques with custom espionage malware, along with both adaptability and effectiveness.
Notable Operations (Timeline)
APT36 has conducted instances of high-profile campaigns over the last decade that demonstrate its continued persistence and expansion.
- 2016–2018: A wave of spear-phishing campaigns targeted Indian military and governmental organizations, often with malicious documents related to defense operations roughly formed by a hallmark.
- 2020: The use of ObliqueRAT, delivered via legitimate government websited that had been compromised.
- 2022–2023: The group expanded into mobile spyware, using CapraRAT and delivering Android APKs that monitored military personnel, diplomats, and civilian academics.
- 2024–2025: The group resumed spear phishing campaigns that used defense and research lures and continued utilizing Android surveillance apps and expanded impacted geography into areas outside of India, including the Middle East and Europe, and into North America.
Recent Developments (2024–2025)
Recent intelligence assessments emphasize a marked change in APT36’s activity patterns. Though India continues to be the main threat vector, the group has also added to its models and regional targeting scope:
- Wider Geographic Reach: APT36 campaigns now extend into Europe, Middle East and North America, representing a wider-scale espionage efforts.
- Mobile Expansion: Increased use of Android-based spyware to allow deeper access to personal communications and mobility data.
- Persistent Phishing: Continued use of spear-phishing emails, although with improved sophistication and localization to bypass traditional defenses.
These changes show how APT36 can adapt to global security environments and conduct intelligence collection against suspected states while remaining relevant even as detection and defense mechanisms continue to improve.
Strategic Impact
The longevity of this Operation C-Major constitutes a strategic concern to cybersecurity itself. Targeting of military and government and research places a significant emphasis on the group’s goals to sustain disruption and monitoring of an adversarial state’s actions. Three implications stand out:
- Regional Geopolitics: By centering APT36 efforts on particular institutions in India, APT36 can carrying out its activities in support of its foreign policy objectives of Pakistan and South Asia.
- Global Expansion: APT36 footprint is increasingly present in Europe and North America, indicating a larger global operational aspiration, and possible international collaboration.
- Mobile Espionage Capacity: APT36’s increased usage of Android spyware reflects adults in modern engagement in intelligence collection. Mobile applications use mobile devices as a gateway into the personal and professional manner.
Defensive Takeaways
Organizations may improve their protective posture against APT36 with actionable steps, including:
- Phishing Defense: Routine training, to include advanced email filtering and phishing simulations.
- Endpoint Security: EDR (Endpoint Detection & Response) tools to reveal Remote Access Tool activity
- Mobile Security: MDM (Mobile Device Management) and threat detection for Android mobile devices
- Threat Intelligence: Utilize threat intelligence feeds to track IOCs and campaigns as they evolve
- Zero Trust Principles: Limitation on the lateral movement by implementing stringent access and segmentation.
APT36 is successful in part due to its exploitation of social engineering and the user, thus human-focused awareness of security is as important as a technical defense.
Conclusion
Operation C-Major (APT36) illustrates the tenacity and adaptability of modern state-linked APT actors. In over a decade’s time, it evolved from a regional espionage entity into a multi-platform, globally active threat actor. India remains a central focus for APT36, however, its recent operational activity in further stages of Europe, the Middle East, and North America shows an ambition for broad-scale intelligence-gathering.
From a defensive standpoint, APT36 should be understood as more than a technical threat, it is a geopolitical mechanism to achieve Pakistan’s long-term priorities for intelligence collection. A combination of vigilance, proactive defensive mechanisms, and a strong incident-response approach can help organizations reduce their exposure to this longstanding, adaptive adversary.
You can download and review the sheet for all the details!






