Executive Summary
This report provides a comprehensive overview of the offshore and anonymous domain service ecosystem, a critical enabler of cybercrime operations such as phishing, ransomware deployment, and cryptocurrency theft.
By examining service providers, infrastructure patterns, and underground market dynamics, the research demonstrates how cyber threat actors leverage these services to sustain persistent operations while evading detection and legal accountability.
Key findings include:
- Q1 2025 data indicates a steady increase in the offering of offshore domain services on underground platforms, suggesting a maturing and self-reinforcing cybercriminal ecosystem.
- Threat actors consistently rely on anonymous domain registration services to bypass Know Your Customer (KYC) protocols and avoid traceability.
- Services are actively promoted via Telegram bots, dark web forums, and web panels frequently bundled with bulletproof hosting options.
- Providers offer a range of features such as SSL certificates, anti-bot protections, domain rotation mechanisms, and cryptocurrency-based payments to maximize operational resilience.
- Prominent ransomware groups, including Conti, Medusa, and RansomedVC, have been observed utilizing offshore domain services particularly those associated with providers.
- Infrastructure supporting these services is designed to resist takedown attempts and is often hosted within permissive jurisdictions.
| Disclaimer |
| This report is classified as TLP:WHITE, allowing for full public distribution. A more detailed TLP:AMBER:STRICT version containing technical indicators and actor-attributed infrastructure is available upon request through official communication channels. |
Introduction
Cyber threat actors employ a variety of sophisticated methods to sustain their operations and evade detection. One such method involves the procurement of domain names used during malicious activities. Rather than registering domains directly, threat actors often rely on third parties who specialize in providing anonymous and offshore domain acquisition services.
The primary motivation behind this practice is to enhance anonymity and reduce traceability. Direct registration increases the risk of linking domain ownership to threat actors. By leveraging intermediaries and bulletproof service providers entities that intentionally disregard legal and regulatory takedown requests threat actors can significantly mitigate operational risks.
These services typically involve domains registered with fabricated identities, compromised domains, or pre-existing active domains, offering a secure and resilient foundation for malicious operations.
Another important driver for the use of such services is the evasion of Know Your Customer (KYC) requirements and regulatory scrutiny. Legitimate domain registrars often mandate identity verification, making direct registration riskier for threat actors.
Anonymous and offshore services allow them to circumvent these controls, further complicating efforts by law enforcement to trace malicious activities. This approach not only strengthens operational security but also minimizes exposure to legal risks for illicit activities.
Moreover, some offshore providers openly advertise their ability to resist takedown efforts initiated by cybersecurity firms and law enforcement, especially for domains used in phishing campaigns targeting financial institutions or government entities. This reflects a shift from mere anonymity services to active anti-intervention positioning as part of their value proposition.
Our research identified that these services are marketed and sold primarily through two channels: web-based panels and Telegram bots. Additionally, evidence suggests that the offshore and anonymous domain service ecosystem often intertwined with bulletproof hosting operations has been active since the early 2000s:
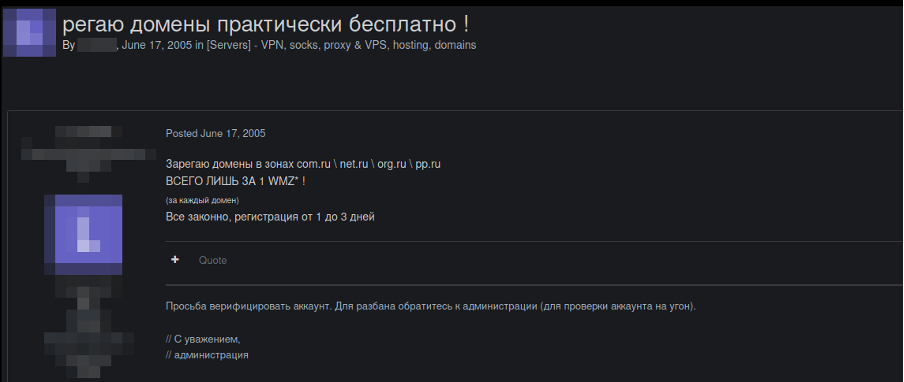
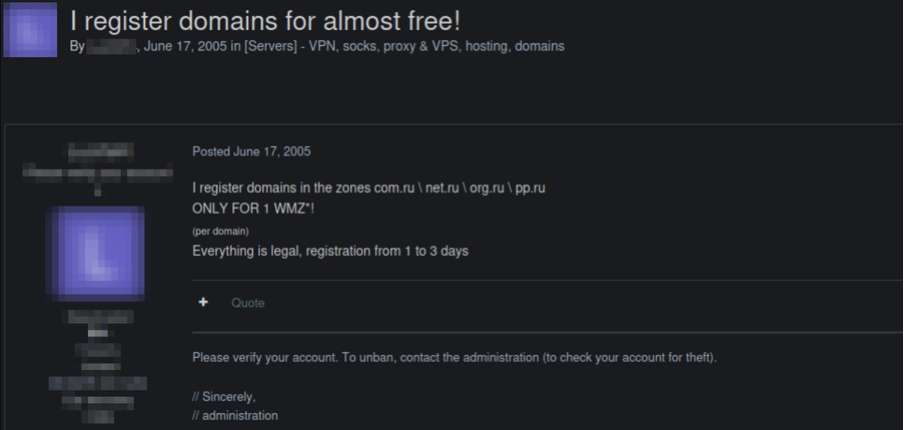
Offshore Domain Service Sector
The offshore domain service sector plays a critical role in enabling and sustaining malicious operations by offering domain registration and hosting solutions that emphasize anonymity, operational security, and flexibility. This sector directly supports activities such as phishing campaigns, ransomware distribution, cryptocurrency theft, and various black-market services by reducing traceability and circumventing traditional detection mechanisms.
Offshore domain providers often work in tandem with bulletproof hosting services, creating robust infrastructures that are highly resistant to legal takedown efforts and automated security controls.
3.1. Purpose and Use Cases of Offshore Domains
Offshore domain services are primarily used for the following purposes:
- Phishing and Bank Login Attacks: Threat actors register domains that closely mimic legitimate organizations (e.g., banks, e-commerce platforms) to deceive victims and harvest sensitive credentials.
- Ransomware Campaigns: Domains facilitate payload delivery, victim communication, ransom payment collection, and C2 (command-and-control) infrastructure operations.
- Cryptocurrency Drainers: Dedicated offshore services cater to drainer groups that focus on stealing cryptocurrencies from compromised wallets.
- Bulletproof Hosting Support: Certain providers offer “red page prevention,” anti-bot mechanisms, and rapid domain replacement services to maintain uninterrupted malicious operations even after exposure.
- Malware Delivery and Botnets: Domains are used to distribute malware payloads and coordinate botnet communications securely.
3.2. Service Providers on Underground Platforms
Many threat actors operating in the offshore domain market present their services through websites that, at first glance, resemble legitimate hosting and domain registration companies. However, upon closer inspection, it becomes evident that these platforms primarily cater to cybercriminals seeking anonymity, operational security, and resilience against takedown attempts.
These service providers often highlight features such as “No KYC“, “Bulletproof policies,” and “instant provisioning,” directly appealing to actors involved in phishing, malware distribution, ransomware operations, and other illicit activities.
During our intelligence research, we identified a threat actor openly advertising “Bulletproof domains” and “DMCA ignored” policies, offering domain services for high-risk activities such as affiliate programs, warez, torrents, and scam pages.
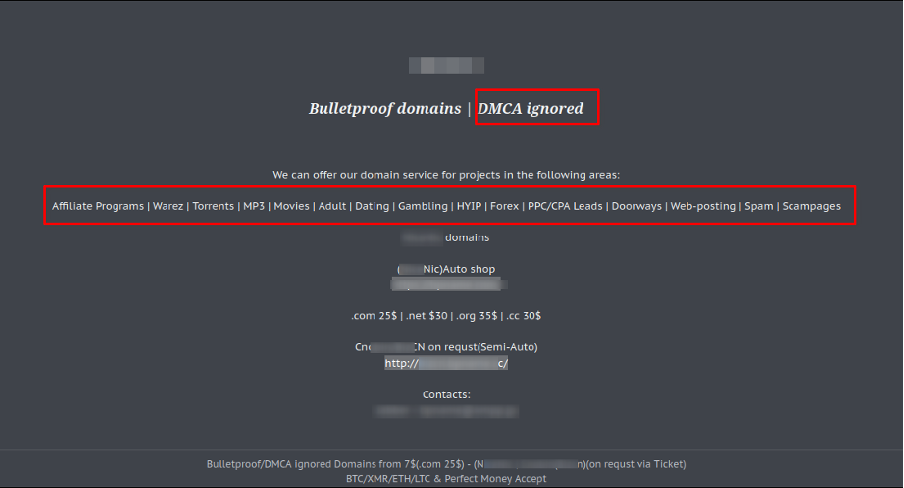
Threat actor emphasizes support for a wide range of controversial and illicit activities, including warez distribution, gambling operations, scam pages, and black-hat marketing campaigns. Prices for domain registration vary depending on the TLD, with payments accepted via cryptocurrencies such as Bitcoin (BTC), Monero (XMR), and Ethereum (ETH).
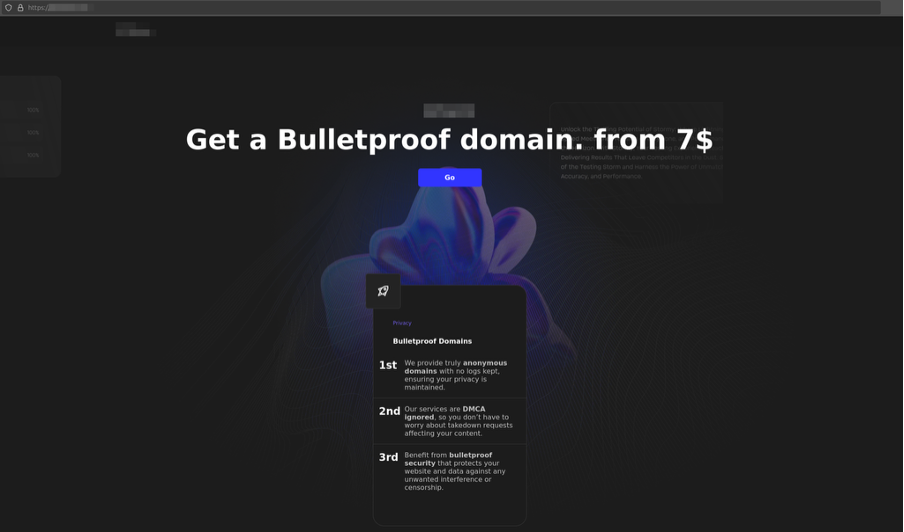
A threat actor offers offshore domain registration with explicit claims of bulletproof protection and 24/7 customer support through encrypted communication channels.
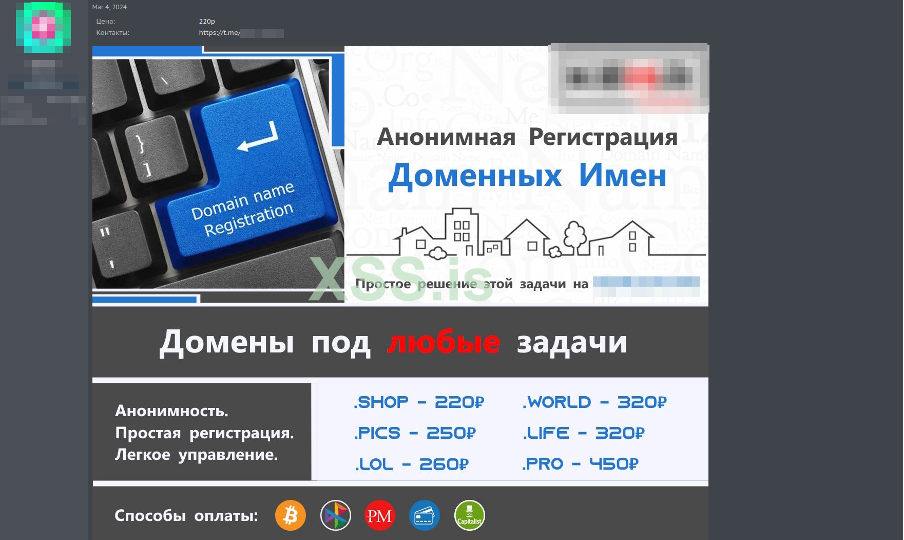
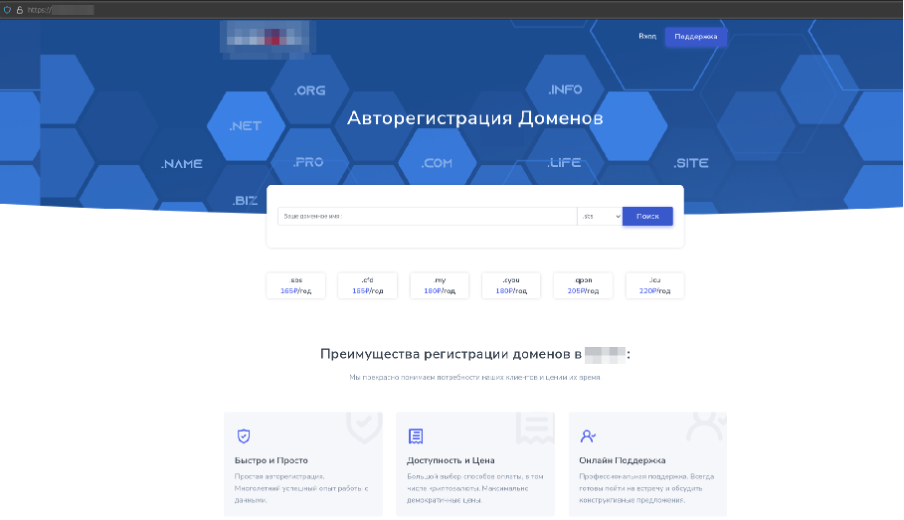
One such provider distinguishes itself by offering a “content-neutral” hosting policy, alongside fast domain replacement options for flagged or seized domains.
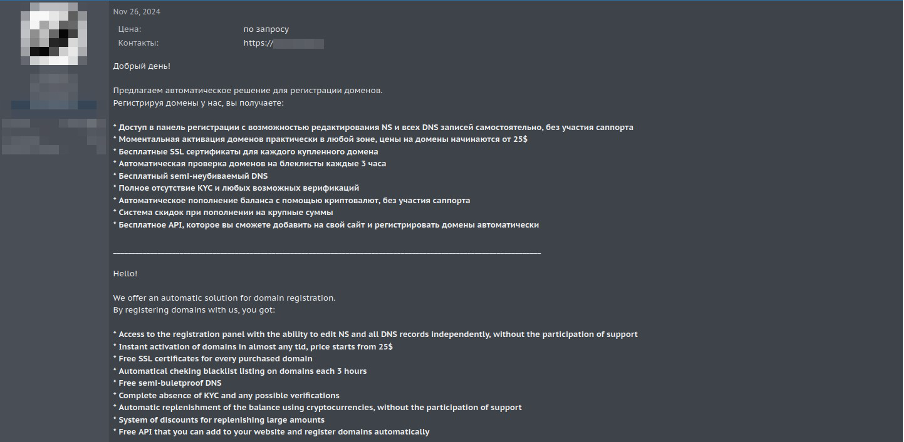
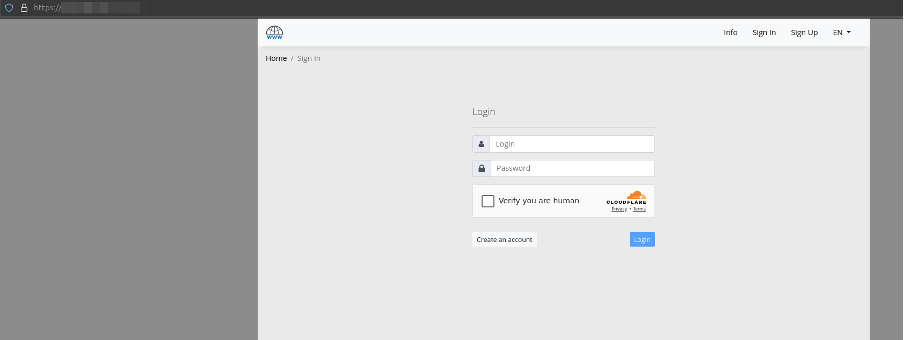
Figure 8: Homepage of an anonymous domain registration platform
Some offshore providers promote themselves as “trusted platforms for red teamers and private projects,” offering domain registrations without any verification requirements.
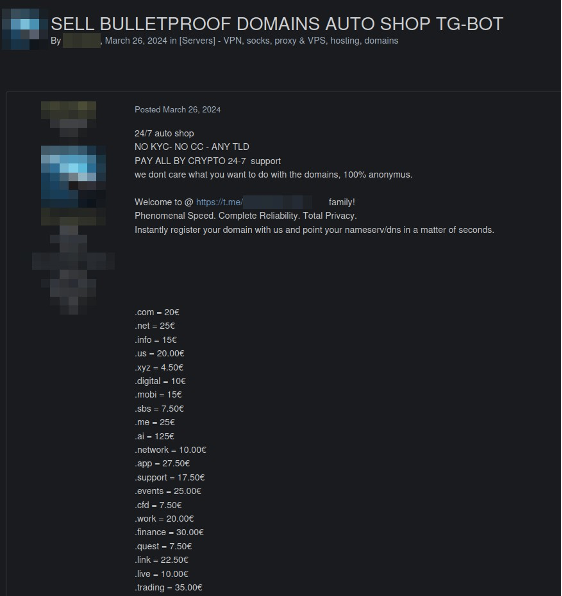
In addition to traditional websites, certain services use Telegram bots to automate the ordering process and preserve operational anonymity.
While most offshore providers operate without content restrictions, a minority impose selective limitations to reduce unwanted attention or manage operational risks. For example:
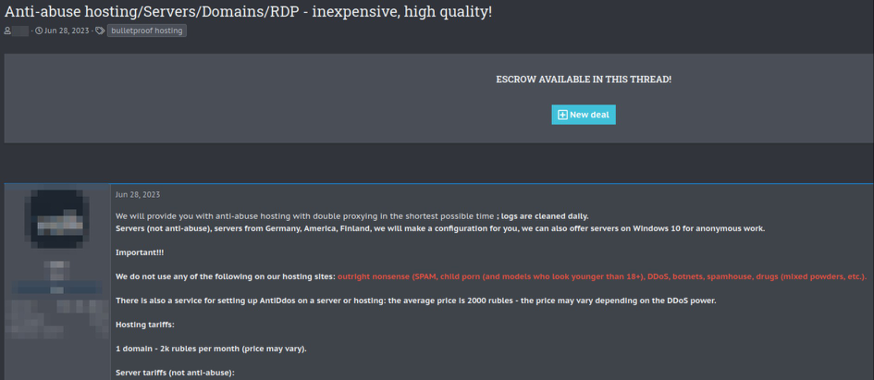
| Analyst Note |
| The presence of content restrictions indicates that some providers seek to balance operational longevity with perceived ethical boundaries, aiming to avoid unwanted scrutiny from law enforcement or regulators. |
In addition to independent websites, many service providers actively advertise their offerings through dark web forums. These posts often include:
- Descriptions of available domain and hosting packages
- Direct links to their service portals or Telegram bots
- Screenshots of the user interface and service dashboards
- Testimonials or customer reviews to build credibility
Example structure observed during research:
- Forum Advertisement: A detailed post outlining service features and pricing
- Service Redirection: A URL or Telegram link provided for direct access
- Service Interface: Screenshots showing the service ordering panel or domain management dashboard
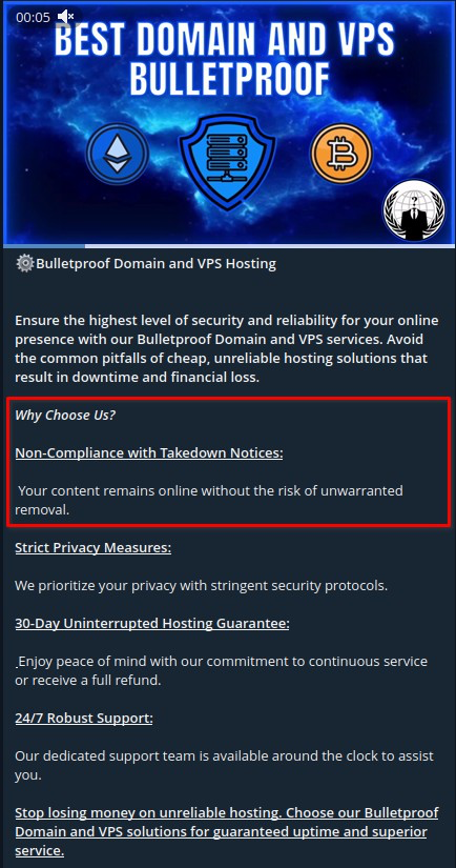
As observed during our investigation, underground bulletproof domain and VPS services are frequently promoted via Telegram using marketing language that closely mirrors that of legitimate infrastructure providers. One such example, originating from a channel, is shown below:
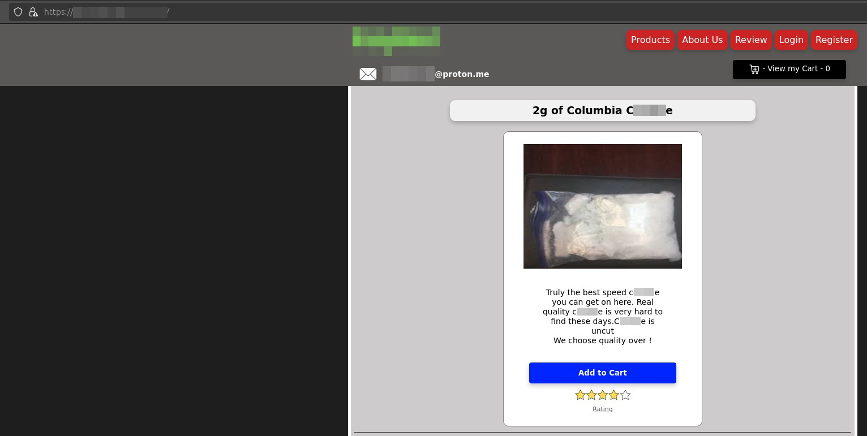
In addition to ransomware and phishing operations, offshore domain services have long been leveraged to facilitate a wide range of illicit trade activities ranging from counterfeit goods and fraudulent services to unlicensed pharmaceuticals-making them accessible on the clear web under a veil of anonymity:
3.3. Services Offered by Threat Actors
Threat actors offering offshore domain services provide a range of features that enhance operational security and usability:
- Anonymous Domain Registration: Domains are registered without KYC (Know Your Customer) verification or by using fake or stolen identity information.
- Automated Panels and API Access: Threat actors offer web-based panels and APIs to streamline domain management and automate registrations.
- Free SSL Certificates: Providers often include free SSL certificates to legitimize malicious domains and avoid browser warnings.
- Blacklist Avoidance: Domains are automatically checked against blacklists every few hours to prevent blocking.
- Resilient DNS Services: Providers advertise “semi-bulletproof” or “unbreakable DNS” solutions to ensure domain uptime.
- Anti-Bot Solutions: Advanced anti-bot measures filter out unwanted traffic, such as security crawlers and Google Safe Browsing bots.
- Geo-Targeted Traffic Filtering: Anti-bot tools restrict traffic to specific regions (e.g., mobile devices in target countries) to evade spam detection.
- Cryptocurrency Payments: Payments via cryptocurrencies eliminate traceable financial footprints.
- Domain Rotation and Expiration Alerts: Services include domain cycling to replace flagged domains and extend malicious campaigns.
- Free Cloudflare Integration: Services include integration with Cloudflare to shield domains from takedowns and DDoS attacks.
- Domain Transfer Capabilities: Domains can be transferred between users without verification.
| Analyst Note |
| These features create a robust ecosystem for threat actors, enabling them to establish resilient infrastructure that supports various cybercrime operations. |
Technological Infrastructure of Service Vendors
Offshore and bulletproof hosting service providers typically operate on privacy-oriented, highly resilient infrastructures. These providers are not only theoretically structured but have been directly observed by our team during a case investigation involving a known service that supplies domains to ransomware groups.
Their infrastructure is built on the following technical pillars:
- High-performance servers hosted in jurisdictions with limited regulatory oversight.
- Redundant power systems, access control mechanisms, and environmental monitoring tools ensure service continuity.
- Network architecture is reinforced through multi-homing, BGP routing, and DDoS mitigation.
- Standard security protocols include HTTPS, full disk encryption, and intrusion detection systems (IDS).
- Anonymous payments (e.g., cryptocurrency) and WHOIS protection services are provided to preserve user privacy.
4.1. Observed Technologies in Offshore Infrastructure
In our OSINT-based scanning of servers the following technologies were most commonly observed:
Browser Trust Level: Endpoints are often marked as “Trusted”, despite their use in illicit operations.
Web Server: Nginx – one of the most widely used HTTP servers.
Admin Panel: Webmin – a Linux server management interface, accessible via port 10000.
Remote Access: OpenSSH – standard for secure server connectivity.
WAF/Security Layer: F5 Big-IP Access Policy Manager.
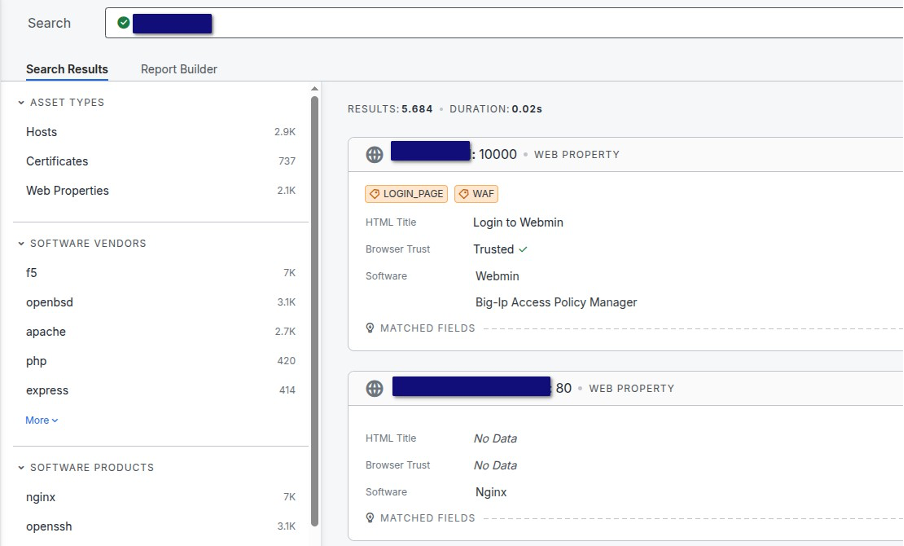
These technologies are composed of widely adopted open-source and commercial solutions. No uncommon or advanced components were identified; the systems are generally built on mainstream, reliable infrastructure choices.
| Analyst Note |
| By configuring their infrastructure with common components like Nginx and Webmin, threat actors ensure both performance and camouflage. The fact that these systems are labeled “Trusted” by browsers delays initial detection and hinders reputation-based filtering mechanisms. |
Offshore Domain Services, Trends, and Crime
Based on our analysis, we identified more than 10 popular offshore domain service providers, each responsible for registering over 1,000 domains. Most ransomware groups and dark web forums also utilize services from offshore domain providers.
During our investigation, we also discovered dedicated providers that exclusively serve crypto drainer groups:
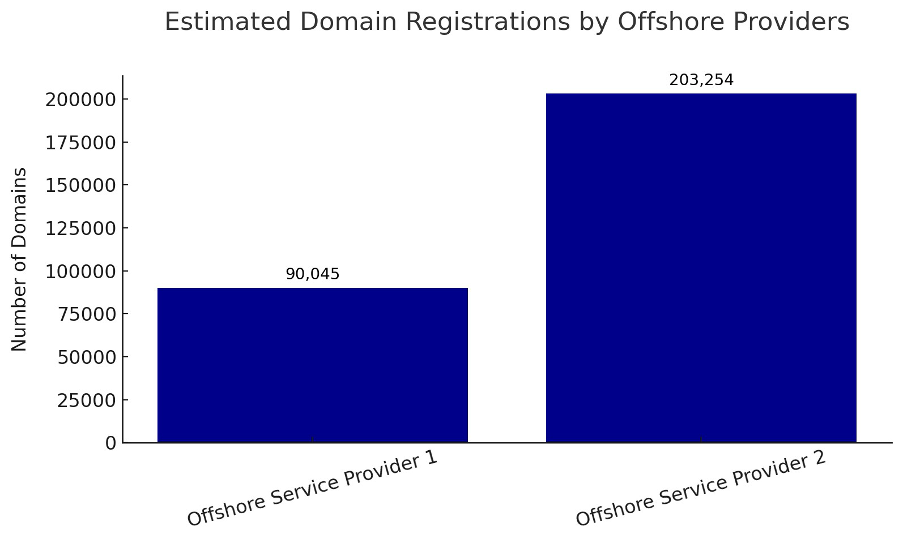
Our findings indicate that the two most frequently used offshore domain providers by threat actors are Offshore Service Provider 1 and Offshore Service Provider 2.
Domains registered via these entities typically appear under the names associated with their respective corporate fronts. The total number of domains registered under these two providers is around 300,000 overall.
A steady increase was observed in offshore domain service activity across Q1 2025, with March showing a more than 50% rise compared to January:
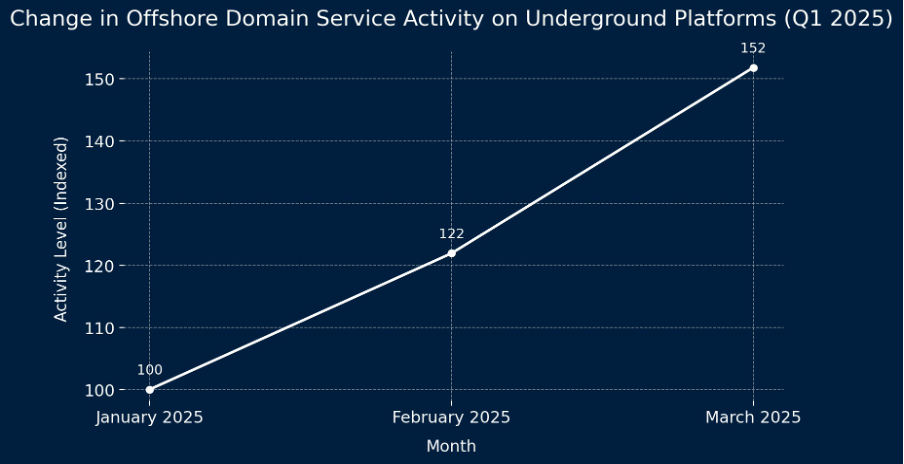
This pattern suggests growing demand for quickly deployable infrastructure, commonly used to facilitate phishing, malware delivery, and command-and-control operations.
The upward trend not only reflects a growing reliance on offshore and bulletproof hosting providers by threat actors, but also points to an acceleration in underground trade between these actors.
Our findings reinforce the connection between domain infrastructure services and ransomware operations, indicating that threat groups function as part of a mutually reinforcing ecosystem, where service provisioning, data extortion, and monetization tactics are increasingly interdependent.
(Note: In the TLP:WHITE version of this report, the real names of these providers are anonymized.)
5.1. Usage Patterns of Offshore Domain Providers
To illustrate the scale and consistency of usage, we identified a representative sample of domain names registered under Offshore Service Provider 1 and Offshore Service Provider 2.
While the full domain names and registrar information have been restricted in this version, the sample clearly reflects a recurring pattern of registrations associated with suspicious or malicious operations.
- Both providers show domain creation dates clustered within recent years, suggesting ongoing malicious activity.
- Several domain names appear structurally similar or themed around cryptocurrency, anonymization, or underground services.
- In total, over 90,000 domains are attributed to Offshore Service Provider 1, and more than 200,000 domains to Offshore Service Provider 2, based on reverse WHOIS data.
Note: Full domain details are presented only in the classified version of this report.
Supporting this assessment, our team identified through the analysis of the Black Basta chat leak that domains used in their operational activities had been registered via “Provider 1” offshore service provider with known ties to bulletproof infrastructure.
This finding further reinforces the broader trend of cyber threat actors deliberately leveraging privacy-focused and jurisdictionally distant registrars to obscure infrastructure ownership and hinder attribution efforts.
5.2. Registrar Abuse Response Gap
One of the key factors contributing to the resilience of offshore domain services is the lack of timely and effective abuse handling by certain domain registrars. Despite receiving multiple abuse complaints including those related to phishing, ransomware, and crypto scams some registrars consistently fail to take down malicious domains or respond only after extended delays.
Our research revealed that the majority of domains used by offshore providers were registered via two major registrars, referred to here as Registrar 1 and Registrar 2.
Both entities appear frequently across infrastructure used by ransomware groups, crypto drainers, and phishing campaigns. These registrars are often characterized by:
- No real-time abuse reporting systems
- No automated domain suspension policies
- Delayed or manual ticket-based takedown processes
- Geographical or legal insulation from Western law enforcement
Historical abuse reports associated with these registrars indicate recurring patterns of delayed or absent takedown responses, reinforcing their position as preferred intermediaries within the underground domain ecosystem.
| Analyst Note |
| The abuse response gap represents a systemic weakness in global domain governance. Threat actors are well aware of this policy blind zone and actively register domains through non-cooperative registrars to extend campaign longevity. |
The following table outlines the observed associations between ransomware groups and the top five offshore domain providers, reflecting their alignment with infrastructure acquired via lenient registrars.
| < | Offshore Provider 1 | Offshore Provider 2 | Offshore Provider 3 | Offshore Provider 4 | Offshore Provider 5 |
| RansomedVC | ✓ | ||||
| Abraham’s Ax | ✓ | ||||
| Karakurt | ✓ | ||||
| Black Basta | ✓ | ||||
| Hunters Internationals | ✓ | ||||
| Inc Ransom | ✓ | ||||
| Conti | ✓ | ||||
| Dispossessor | ✓ | ||||
| Malek Team | ✓ | ||||
| Medusa | ✓ | ||||
| Mosesstaff | ✓ | ||||
| Nullbulge | ✓ | ||||
| Radar | ✓ | ||||
| Snatch | ✓ | ✓ |
| Analyst Note |
| These service providers, commonly used for illicit activities, host hundreds of thousands of domain names. This widespread infrastructure use demonstrates the critical role such providers play in supporting large-scale phishing and ransomware operations, as well as various other cybercriminal campaigns. |
Conclusion and Evaluation
The continued availability and evolution of offshore domain services significantly contributes to the sustainability of cybercriminal operations. These services act as both a shield and an enabler, protecting the identities of malicious actors while offering the technological capabilities needed for persistent and scalable attacks.
Our analysis of Q1 2025 data reveals a clear upward trend in the underground offering of such services, particularly those related to domain provisioning. This growth reflects an increasing operational dependency on offshore infrastructure among cybercriminal groups, especially in the context of ransomware and data extortion campaigns.
Key takeaways:
- Regulatory blind spots and lack of global cooperation allow these services to thrive.
- Threat actors increasingly automate domain acquisition via bots and APIs, lowering barriers to entry for cybercrime.
- Ransomware groups and crypto drainers depend on resilient infrastructure, reinforcing the importance of targeting these ecosystems in mitigation efforts.
- The offshore domain ecosystem is part of a mutually reinforcing underground economy, where service providers, attackers, and monetization tools feed into each other’s growth.
| Distribution Notice |
| This blog is classified as TLP:WHITE, allowing for unrestricted sharing. To access the full TLP:AMBER:STRICT version with actionable threat intelligence, contact our team through the designated secure channels. |

Why Brandefense?
Cybercriminal organizations exploit your company’s weaknesses to access sensitive information, organize phishing activities, and infiltrate your organization. With these actions, they aim to generate income or damage your reputation.
The Brandefense module provides proactive protection against cyber threats by constantly monitoring potential risks to your brand, employees, executives, and customers.
- For over a decade, Brandefense has been at the forefront of the cybersecurity sector.
- We have been protecting over 600 brands since this time.
- Through our extensive experience in this field, we developed a deep understanding of cybersecurity concepts.
How Does Brandefense Help You?
- Get continuous and real-time cyber intelligence from Dark Web & Surface Web.
- Minimize false-positive records by leveraging machine learning and analysts’ expertise.
- Integrate your security devices like firewalls, SIEM, and SOAR with incidents and intelligence indicators.
1. Brandefense Solutions
1.1. Brand Protection
- Breach Monitoring
- Dark Web Monitoring
- Phishing Monitoring
- Compromised Device Detection
- Data Leak Monitoring
- Executive Protection
- Social Media Monitoring
1.2. Cyber Threat Intelligence
- Threat Intelligence
- Strategic Intelligence
- Fraud Intelligence
- Operational Intelligence
- Tactical Intelligence
- Threat Reports
1.3. 3rd Party Risk Management
- 3rd Party Vendor Risk Assessment
- Secure Snap
1.4. External Attack Surface Management
- Attack Surface Management
- Vulnerability Intelligence
- Security Scan
1.5. Fraud Monitoring
- Fraud Protection
- Global Stolen Credit Card Database
- TTP Reports
2. What Brandefense Provides?
2.1. Risk-Free Exploration
Safeguard your sensitive data and avert unauthorized access without venturing into the perilous dark web realm.
2.2. Strategic Intelligence Power
To avoid potential harm to your business, proactively guard against threat actors and attacks targeting your sector and region with foresight.
2.3. Controlled Attack Surfaces
Effortlessly assess the risks of potential attacks and new applications on our servers while keeping tabs on their ever-evolving, openly-accessible surfaces.
2.4. Guard Against Fraud
Detect stolen cards and alert your employees and customers to stolen information, and thwart fraudulent actions carried out in your name online.
2.5. Secure Critical Staff
Monitor data breaches specific to those who have access to important information, and protect your company’s reputation by monitoring suspicious activity and fake accounts.
2.6. Protection from CVEs
To prevent the chain of attacks, prevent possible ransomware attacks with vulnerability intelligence that allows you to take timely action against vulnerabilities.







