Introduction
The internet as most people know it represents only a small fraction of what truly exists online. Beneath the surface lies the Deep Web and its even more elusive subset, the Dark Web—a hidden realm where anonymity reigns supreme. While the Dark Web offers opportunities for privacy and legitimate uses, it also harbors significant risks, including cybercrime, illegal marketplaces, and the sale of stolen data. This article explores what the Dark Web is, how to access it, and most importantly, how to stay protected from its dangers.
What is the Dark Web?
It is a part of the internet that cannot be accessed by browsers such as Google, Firefox, and Opera, but mostly contains illegal content and applications such as black market, drug dealing, and cybercrime, and can be accessed with the help of specific tools such as Tor Network.
History of the Dark Web
The dark web is a part of the internet that is not accessible through traditional search engines and requires specific software or configurations to access. The history of the dark web can be traced back to the 1970s and 1980s when researchers at the United States Naval Research Laboratory began developing a network of computers called Tor (The Onion Router). The goal was to create a secure and anonymous communication system for government agencies.
In the early 2000s, Tor was released to the public and became popular among users who wanted to protect their privacy online. The dark web, a small part of the larger deep web, began to emerge as a result.
One of the earliest and most well-known dark web marketplaces was the Silk Road, launched in 2011 by Ross Ulbricht. The site allowed users to buy and sell drugs, weapons, and other illegal goods using cryptocurrencies such as Bitcoin. The Silk Road was shut down by law enforcement in 2013, but other dark web marketplaces have since emerged to take its place.
The dark web has also been used for other nefarious activities, such as the sharing of child pornography and the planning of terrorist attacks. Law enforcement agencies have tried to track down and prosecute individuals involved in such activities, and there have been several high-profile arrests and convictions in recent years.
Despite its association with illegal activities, the dark web also has legitimate uses, such as providing a means for journalists and activists to communicate securely and anonymously and offering a platform for whistleblowers to share information without fear of retaliation.
How Big is the Dark Web?
It is difficult to determine the exact size of the dark web, as it is not indexed by traditional search engines, and its contents are often hidden behind layers of encryption and anonymity. However, it is estimated that the dark web makes up only a small fraction of the overall internet, likely less than 0.01% of the total content.
The dark web is also a dynamic and ever-changing space, with new sites and services constantly emerging and others being taken down by law enforcement or other actors. Therefore, any estimate of its size is likely to be imprecise and quickly outdated.
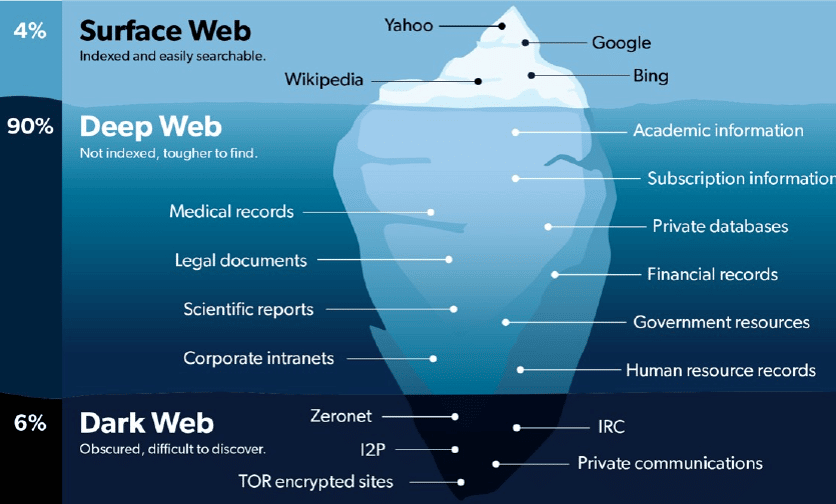
What is the Difference Between the Dark Web & Deep Web?
The terms “dark web” and “deep web” are sometimes used interchangeably, but they actually refer to different aspects of the internet.
The deep web refers to all parts of the internet that are not indexed by search engines and are not accessible through traditional means, such as password-protected websites, private databases, and online banking systems. It is estimated that the deep web makes up the vast majority of the internet, possibly 90-95% of it.
The dark web, on the other hand, is a small portion of the deep web that is intentionally hidden and can only be accessed using special software or configurations, such as the Tor network. The dark web includes various illicit activities, such as black markets, drug sales, illegal pornography, and hacking forums. It is known for its anonymity and lack of regulation, making it a haven for criminal activity.
In summary, the deep web refers to all parts of the internet that are not indexed by search engines, while the dark web is a small subset of the deep web that is intentionally hidden and used for illicit purposes.
Is It Illegal to Access the Dark Web?
Accessing the dark web is not inherently illegal in most countries, as it is simply a hidden part of the internet that can be accessed through the use of certain software or configurations. However, the dark web is known for hosting illegal activities, such as drug trafficking, weapon sales, hacking services, and child exploitation, among others.
Therefore, if a person accesses the dark web with the intention of engaging in illegal activities or purchasing illegal goods and services, they could be committing a crime. Additionally, some countries may have laws that prohibit accessing the dark web or using certain software or configurations to access it. It is important to note that even browsing the dark web can be risky, as there is a high risk of encountering malicious content, scams, and other dangers.
Risks of the Dark Web
Navigating the Dark Web offers anonymity and freedom, but it also comes with significant risks that can jeopardize both individuals and organizations. One of the most pressing threats is the prevalence of malware. Hidden websites often harbor malicious software designed to steal sensitive information, infect devices, or even deploy ransomware. A single careless click can compromise your entire digital ecosystem. To counter such threats, Brandefense’s Dark Web Monitoring solution scans underground forums and communication channels, providing early alerts and actionable insights to help businesses mitigate risks effectively.
Another danger lurking in the Dark Web is the proliferation of phishing scams. Fraudulent websites mimic legitimate ones, tricking users into sharing login credentials, financial details, or other sensitive information. These scams not only affect individuals but can also tarnish a company’s reputation. Brandefense’s Threat Intelligence platform proactively identifies phishing campaigns and provides real-time data to protect brands from exploitation, ensuring your online presence remains secure.
Perhaps the most alarming threat is the sale of stolen data. Personal and corporate information, including email addresses, passwords, and even intellectual property, is often monetized in hidden marketplaces. The impact of such breaches extends beyond financial loss, as it can erode trust and damage reputations. With Brandefense’s Dark Web Monitoring, businesses gain visibility into where and how their data is being exploited, allowing them to take immediate action to prevent further harm.
Lastly, navigating the Dark Web also carries legal risks, as unintentional engagement with illegal platforms or content can lead to severe consequences. Maintaining compliance with legal and regulatory standards is essential for businesses operating in this space. Brandefense’s solutions not only detect risks but also provide a framework to ensure that your activities remain within the bounds of the law, protecting both your brand and your reputation.
How to Get on the Dark Web Safely?
What Are the TOR and TOR Browser?
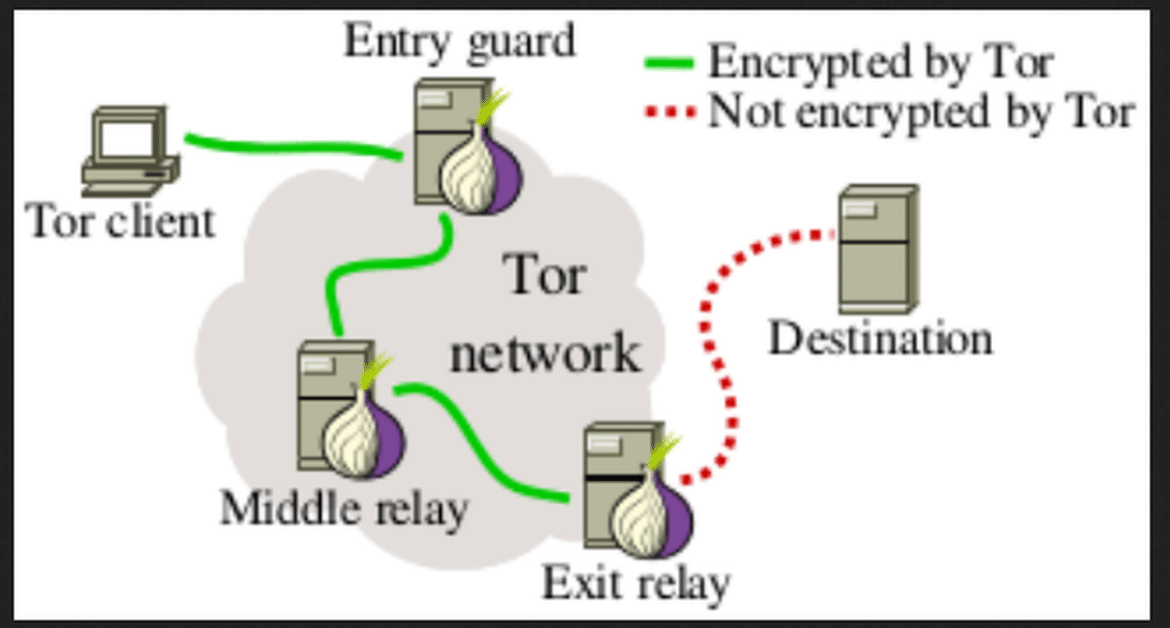
TOR (The Onion Router) is a software that makes it possible for users to communicate and browse the internet anonymously. This is achieved by directing internet traffic through a global network of servers, which conceals the user’s identity and location. The main purpose of TOR is to provide access to the dark web and bypass censorship and surveillance in countries with restricted internet access. On the other hand, the TOR browser is a web browser that uses the TOR network to offer users private and anonymous internet browsing.
It safeguards the user’s online activities and identity by encrypting internet traffic and directing it through a series of TOR servers. While the TOR browser is frequently employed to access the dark web, it can also be used to browse the regular web more securely and privately.
Installation of Tor Browser
Step 1
Download the Tor browser from https://www.torproject.org/download/ and install the downloaded file.
Step 2
After installing, start the Tor browser. If Tor is not banned in your country, you can directly click the “Connect” button and connect to the Tor network. If it is prohibited, you will need to adjust the connection settings. Follow the other steps for this.
Step 3
Click the button in the upper right corner and open the “Settings” section.

Step 4
In the window that opens in the settings section, click on the “Request a Bridge…” button from the “Connection” section on the left.
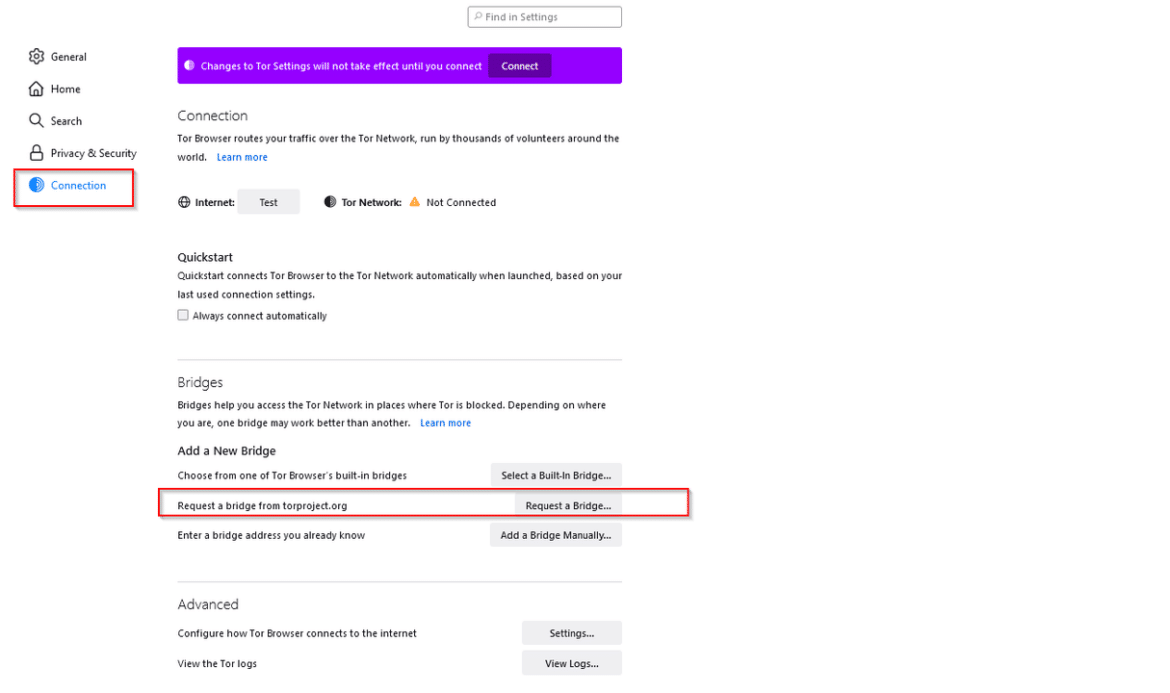
Step 5
Complete the CAPTCHA process on the screen that opens after pressing the button.
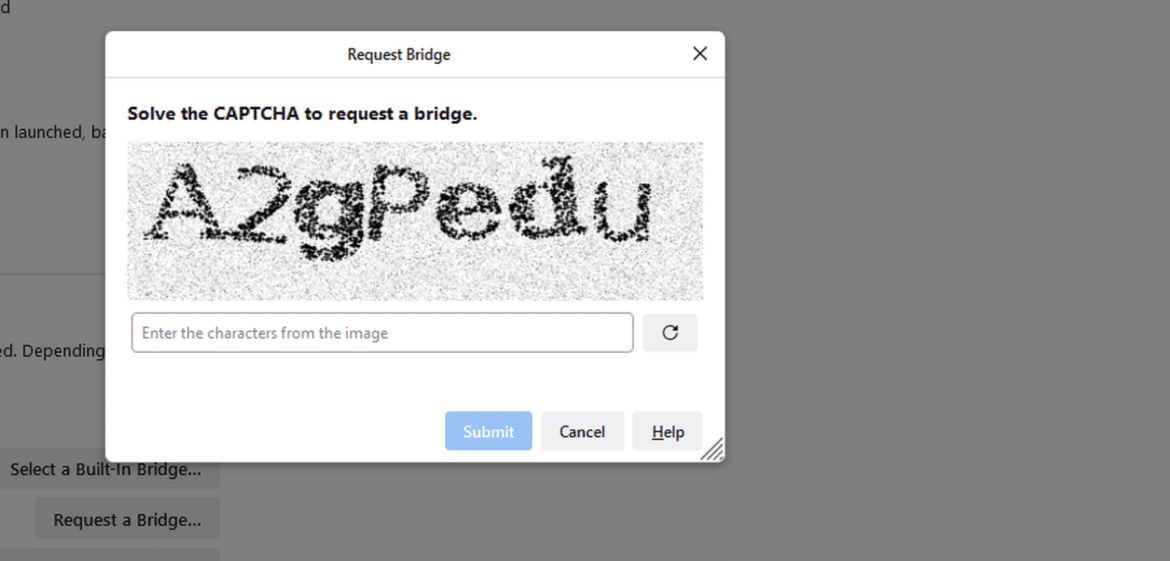
Step 6
After completing the operations and completing the bridge connection, click the “Connect” button in the same window.
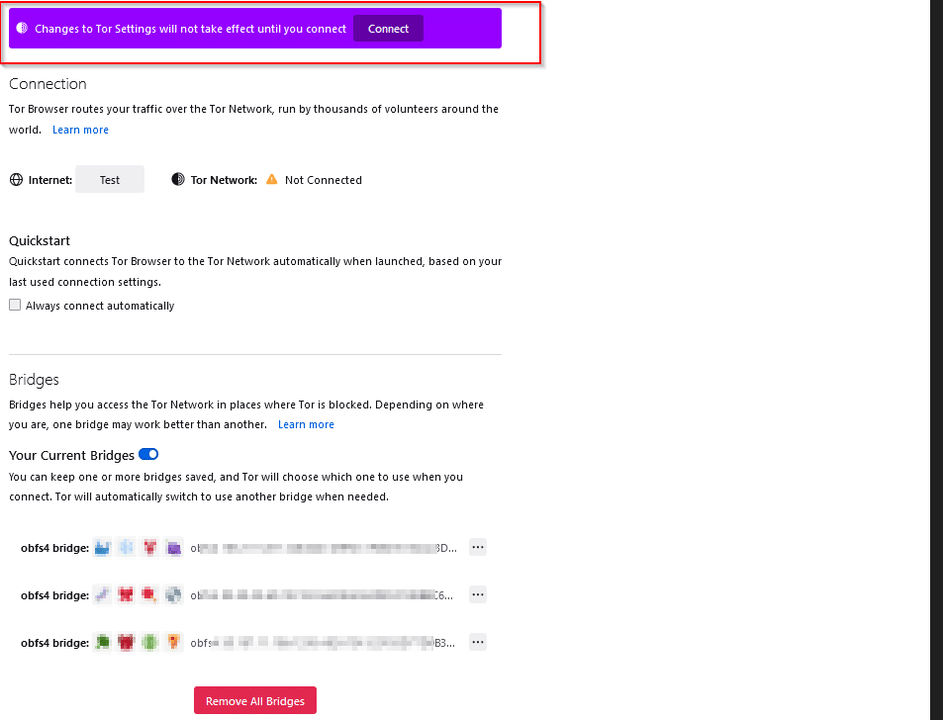
Step 7
After clicking the “Connect” button, you are now connected to the Tor network.
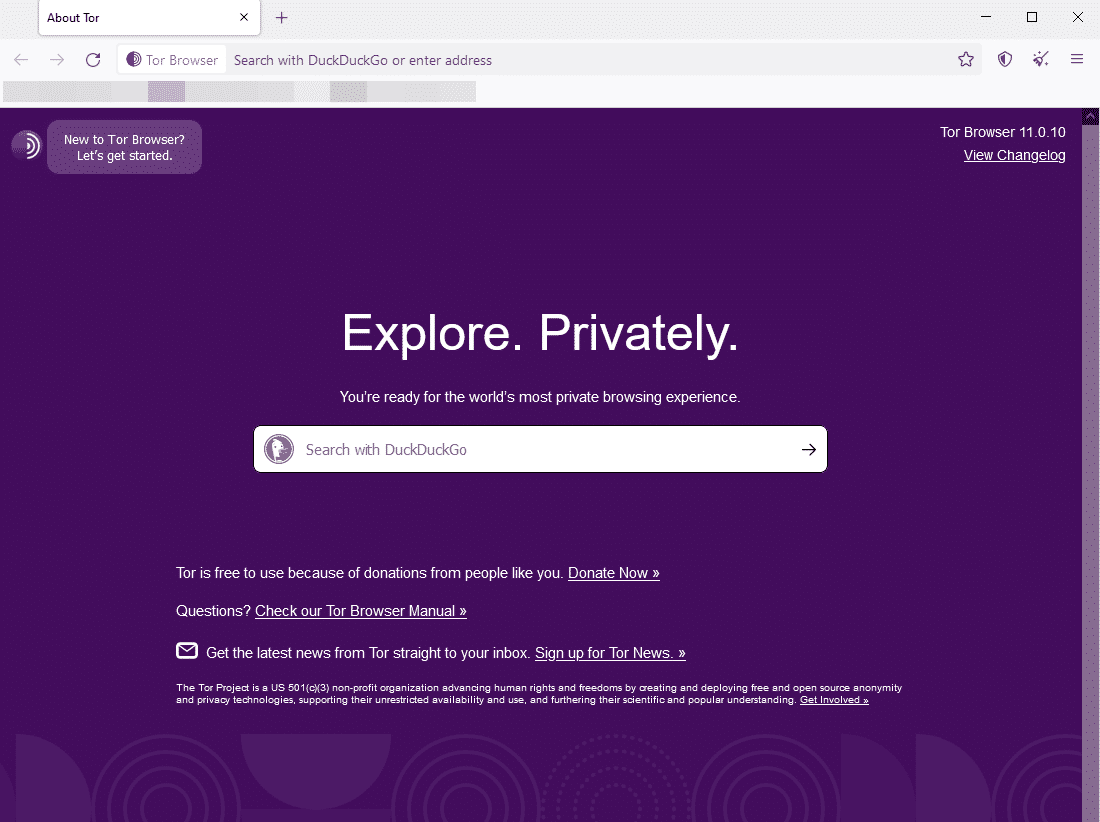
Suppose you do not want to use the bridge connection feature of the Tor browser. You can first make a VPN connection, then open the tor browser and directly press the “Connect” button to connect. You will use the Vpn over Tor method to bypass the ban in this way. In addition, it is known that this method is used by actors to increase anonymity.
Different Way Access to Dark Web
You can also access the Tor network with the Brave browser.
Step 1
Download Brave browser from https://brave.com/ and install the downloaded file.

Step 2
Start Brave browser. Click the button in the upper right and press the “New private window with Tor” in the open window.
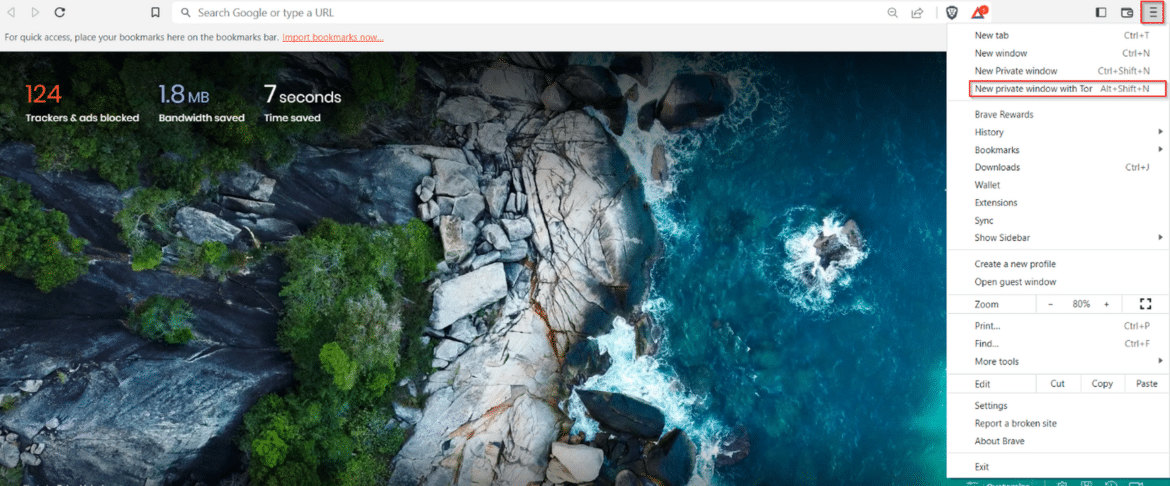
Step 3
We are connected to the Tor network in this way. After connecting to the Tor network, the Brave browser in the bottom left corner, “If your personal security depends on staying anonymous, use Tor Browser instead.” gives a warning.
As described above, you can connect to the Tor network in 2 ways. Entering the Tor network does not constitute any criminal element. However, illegal activity will cause you to commit a crime. In addition, you can use methods such as Vpn over Tor or Tor over Vpn to increase your anonmity.
Dark Web Tools & Services
The dark web offers a variety of tools and services that are not available on the clear web, some of which can be legal while others are illegal. Here are some examples:
Tor Browser
This is a free software tool that allows users to access the dark web and browse anonymously.
Cryptocurrency wallets and exchanges
Cryptocurrencies such as Bitcoin and Monero are commonly used on the dark web for their anonymity and untraceability.
Darknet markets
These are online marketplaces that operate on the dark web and are used for buying and selling illegal goods and services, such as drugs, weapons, and stolen data.
Hacking services
Some dark websites offer hacking services, such as password cracking and DDoS attacks, for a fee.
Anonymity tools
These include VPNs, proxy servers, and anonymizing networks such as Tor, which are used to hide a user’s online activity and location.
Counterfeit documents
Some sites on the dark web offer forged documents such as passports, driver’s licenses, and social security cards.
Illegal pornography
The dark web is known to host illegal and disturbing types of pornography, including child exploitation and violent content.
It is important to note that many of these tools and services are illegal, and using them can result in serious legal consequences.
Dark Web Browsers
Dark web browsers are specialized software programs that allow users to access the dark web. These browsers use encryption and other security measures to help protect users’ privacy and anonymity. Here are some of the most popular dark web browsers:
Tor Browser
The Tor Browser is the most widely used dark web browser. It is free, open-source, and available for Windows, Mac, and Linux. The browser uses the Tor network to anonymize users’ internet traffic and provides access to .onion websites.
I2P
The Invisible Internet Project (I2P) is another dark web browser that provides anonymity and privacy for users. It is primarily used for file sharing and provides access to .i2p websites.
Freenet
Freenet is a decentralized, peer-to-peer network that provides anonymity and censorship resistance. It is primarily used for file sharing and provides access to .freenet websites.
ZeroNet
ZeroNet is a decentralized, peer-to-peer network that allows users to create and host websites without the need for a centralized server. It provides anonymity and censorship resistance and is available for Windows, Mac, and Linux.
It’s important to note that while these browsers provide anonymity and privacy, they do not guarantee complete security. Users should take additional measures to protect their online identity and personal information when using the dark web.
Brandefense Dark Web Monitoring Solution
Our innovative service offers a range of benefits that can help you stay ahead of cybercriminals and protect your brand reputation. With early detection of cyber threats, you’ll have more time to respond and prevent potential data breaches or other attacks. Our dark web monitoring can enhance your overall security posture and protect your sensitive data and assets.
Our Dark Web Monitoring service offers;
Early Detection of Cyber Threats: Dark web monitoring allows businesses to detect cyber threats early on, giving them more time to respond and prevent potential data breaches or other attacks.
Enhanced Security: By monitoring the dark web for potential threats, businesses can stay ahead of cybercriminals and protect their sensitive data and assets.

Brand Protection: Dark web monitoring can also help businesses protect their brand reputation by detecting any attempts to sell counterfeit products or impersonate their brand.
Cost-Effective: The cost of a data breach can be substantial in terms of financial losses and damage to brand reputation. Dark web monitoring is a cost-effective way to mitigate these risks and prevent costly cyber attacks.
Contact us today to learn more about how Brandefense’s dark web monitoring service can help you protect your business and achieve peace of mind.
Conclusion
The Dark Web is a powerful tool that offers anonymity and freedom for users who navigate its hidden layers. It can serve as a haven for whistleblowers, journalists, and those living under oppressive regimes to communicate securely and bypass censorship. However, with such anonymity comes great responsibility. Users must approach the Dark Web with caution and adhere to ethical practices, avoiding engagement with illegal activities or supporting harmful platforms.
For businesses and individuals alike, the Dark Web poses unique threats that go beyond individual use. From data breaches to counterfeit products and unauthorized brand use, malicious actors exploit the Dark Web’s anonymity for financial and reputational harm. This is where Brandefense comes in.
With solutions like Dark Web Monitoring, Threat Intelligence, and Threat Detection, Brandefense empowers users to detect threats early, respond proactively, and safeguard their digital assets. Whether you are protecting sensitive information or your brand’s reputation, Brandefense ensures you remain secure in the evolving digital landscape. Contact us today to learn how we can help.
This article is intended for informational purposes only and does not endorse or promote any illegal activities. While the Dark Web offers legitimate uses, it also harbors significant risks. Users are encouraged to exercise caution, adhere to ethical practices, and comply with applicable laws when navigating online spaces.






