Introduction
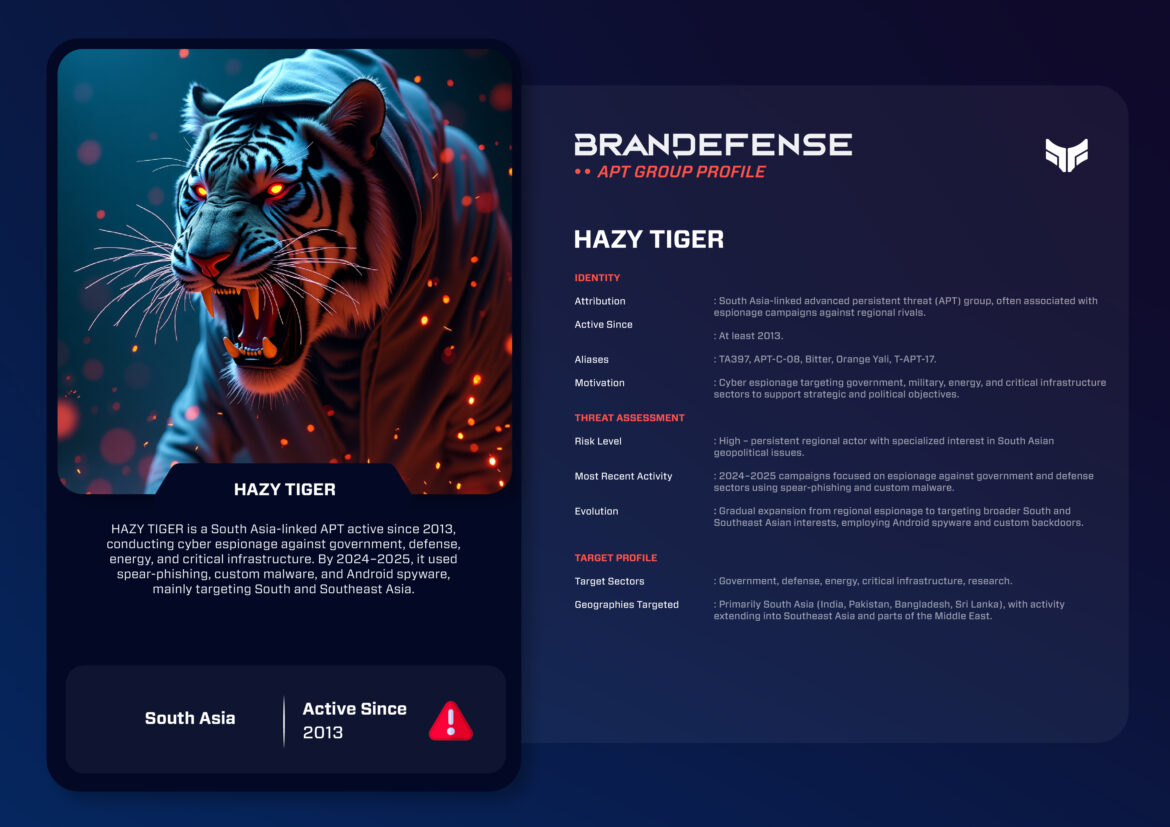
Hazy Tiger, also referred to as TA397, APT-C-08, Bitter, Orange Yali, and T-APT-17, is an advanced persistent threat (APT) group focused on South Asia that has become increasingly active over the past decade. The group has focused its efforts in an operational context on espionage [operations] against government, defense, energy, and critical infrastructure sectors. The group has a suspected nexus to India, due to reported interest in political motivations, with active campaigns against neighboring countries for the purpose of surveillance and intelligence gathering. This blog post investigates the group’s identity, tactics, techniques, and procedures (TTPs), notable operations, recent developments, and implications of their activity for regional and global cybersecurity.
Identity and Motivation
Hazy Tiger is a politically motivated APT group and has been in operation with activity assessed to go back as far as 2013–2016. Research analysts almost universally assess the group to have an India nexus, given its regular targeting of Pakistan, China, Nepal, and Bangladesh. Hazy Tiger appears to have, as its principal mission, long-term intelligence collection – a mission that supports national security priorities and military strategies.
Hazy Tiger’s use of alias to signify their presence and operations show how the identification of the group has shifted over time amongst security vendors and throughout research reporting related to their activity:
– TA397 (Proofpoint)
– APT-C-08 (Qihoo 360)
– Bitter (common alias in research reports to designate Hazy Tiger)
– Orange Yali (designated alias by the security vendor in the region)
– T-APT-17 (Chinese vendor tracking the APT group)
While at the origin of Hazy Tiger’s persistent campaigns there appears to be motivation clearly indictating their intent for espionage, as opposed to the financial gain of criminal actors.
TTPs (Tactics, Techniques & Procedures)
Hazy Tiger uses a stable set of tactics to endanger high-value targets while remaining stealthy and persistent.
Initial Access: Spear-phishing emails are still the most common initial access vector for the group, which focus on geopolitical lures based on regional tensions. Phishing campaigns frequently deliver malicious documents and attachments (i.e., weaponized Office files).
Persistence and Lateral Movement: Custom back doors and implants designed to blend in with victim environments. Abuse of legitimate tools and living off the land techniques. Use remotes access trojans (RATs) to establish footholds and persistence.
Command-and-Control (C2): HTTP/HTTPS based C2 traffic to avoid detection. Use of cloud platforms and anonymization networks for C2 infrastructure on occasion, when it is in a stealthy mode.
Malware & Tools: Custom malware families, BitterRAT and Stolen Pencil variants. Use commodity malware in addition to a custom implant. Exploiting unpatched vulnerabilities in targeted organizations software packages.
Techniques: Credential harvesting and session hijacking. Data exfiltration of sensitive files related to diplomatic correspondence and defense. Intelligence collection via extended periods of monitoring networks.
Notable Operations
Hazy Tiger has conducted several high-profile operations lately, including:
2024: Defense Sector Campaigns
Through their research, ESET has documented Hazy Tiger engaged in espionage activity attributed to weaponized phishing campaigns against defense contractors and some diplomatic offices.
2019–2021: South Asian Government Targeting
The group has been associated with phishing & spearphishing operations against Pakistani and Bangladeshi government organizations focused on military and foreign affairs.
2022: Infrastructure and Energy Espionage
There was activity targeting critical infrastructure within the South Asian region, specifically towards the energy sector. Analysts suspect that the activity was focused on the geopolitical situation in the area.
2023: Nepal and Chinese Entities
Analyzing the region’s activity, Hazy Tiger was not only targeting government departments in Nepal, but also targeting a limited number of Chinese organizations. This suggests an expanding appetite on the part of Hazy Tiger.
Recent Developments
Some of the most recent threat intelligence has pointed out some new trends in Hazy Tiger’s operations.
- Shift to Cloud Abuse: Similar to other APTs, Hazy Tiger appears to be utilizing cloud storage and VPN services for command & control.
- Increased Operational Tempo:There was an increase in operational tempo in 2024-2025 with newly reported phishing campaigns being reported approximately every quarter.
- Improved Tooling: Hazy Tiger is still developing and improving upon custom backdoors but is also using public malware frameworks for obfuscation to limit attributions to a specific APT.
- Regional Expansion: Beyond just Pakistan and Bangladesh, there is evidence suggesting Hazy Tiger engaged with organizations in the Middle East, suggesting a growing geopolitical intent.
Strategic Impact
Hazy Tiger’s activities present notable risks to regional stability and cyber defense preparedness:
• National Security Risk: By primarily focusing on the defense and government areas, the group poses a direct risk to the national security interests of countries in the region.
• Espionage Impact: Their steady campaign work is contributing to a wider escalation of cyber arms races in South Asia.
• Risk to Critical Infrastructure: Their targeting of energy and infrastructure creates a simultaneous risk of being able to execute disruption of service and/or access to intelligence.
• Relevance as a Global Actor: While their core focus is regional, Hazy Tiger shows that even mid-tier APT actors can generate strategic impact and recruit attackers when leveraging relatively modest resources.
Defensive Takeaways
Organizations, particularly those operating in South Asia, should take proactive steps to defend against Hazy Tiger’s campaigns:
• Strengthen phishing defenses by investing in email security systems and making continuous employee awareness training a routine.
• Work to patch vulnerabilities on a continuous basis since it’s known Hazy Tiger is known to exploit obscure, unpatched systems.
• Look for anomalies in cloud and VPN usage, which may be possible evidence of stealthy command and control communications.
• Use threat intelligence feeds to observe changes in tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs).
Conclusion
Hazy Tiger symbolizes a long-standing, politically driven APT threat in South Asia. The group’s ongoing campaigns, changes in its cache of malware, and changes in targets show how significant it is in the international APT environment. For defenders, monitoring and responding to groups, like Hazy Tiger, is not just a part of cyber hygiene, it is about protecting national security and strategic stability in an already tense geopolitical environment. As the group continues to improve its methods and expand its territorial reach, it will be a significant adversary to observe in 2025 and beyond.
You can download and review the sheet for all the details!







