Introduction
External Attack Surface Management (EASM) has transitioned from a compliance boxcheck to a critical security domain. As attackers continue to sharpen their weapons and use the complexity of IT and OT ecosystems to their advantage, organizations must begin to prepare for upcoming EASM Challenges in 2026. This forecast will illustrate how the digital perimeter will change, how APT campaigns are evolving, and what innovations need to be developed to enable defenders to stay ahead of EASM Challenges.
The Shifting Digital Perimeter
Most of the traditional perimeter will be vanished by 2026. Multi-cloud adoption, growth of SaaS, IoT/IIoT deployments and the need for remote access are contributing to a much larger and more volatile attack surface. Studies show that over 80% of incidents arise from unmanaged external assets like abandoned cloud workloads, exposed APIs, or legacy VPN gateways.
The upcoming EASM Challenges are expected to reshape how organizations approach cybersecurity and manage their attack surfaces.
Issues:
- Shadow IT introducing unmonitored exposures
- Third-party applications adding undisclosed dependencies
- OT systems leveraging more public networks
What we need:
- Autonomous asset discovery with context for the IT, OT and vendor environments
- Dynamic risk scoring that ranks exposures based on exploitability and business consequences
- EASM feeds are integrated with SIEM/SOAR for automated remediation in near-real time
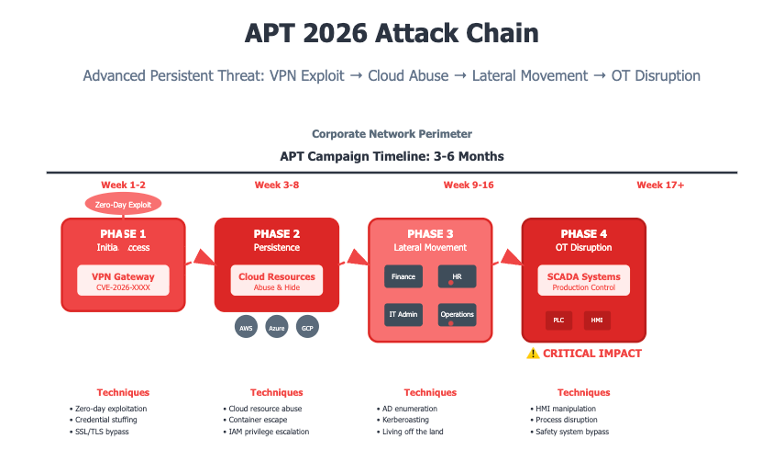
APT 2026: From Espionage to Disruption
Advanced Persistent Threats (APTs) are changing from covert espionage to more direct disruption of operations.
- China-aligned groups like Mustang Panda and DigitalRecyclers are taking advantage of cloud services and VPNs to infiltrate European energy and maritime networks.
- Russia-aligned Sandworm continues to refine their wipers to disable OT environments, with a focus on energy grids and telecom infrastructure.
- Iran-aligned MuddyWater and OilRig are using a combination of spearphishing and remote monitoring tools to take over critical firms through cyber disruption.
In light of these EASM Challenges, integrating advanced technologies will become crucial for maintaining security.
Innovations Needed:
- AI-based anomaly detection for persistence and lateral movement within OT systems.
- Deception model combined with EASM for predicting APT operation in less secure networks.
- Cross-sector collaboration for easier visibility of attack surfaces on critical infrastructure.
The Supply Chain and Ransomware Convergence
Ransomware operators are migrating from encryption to extortion using supply chain compromise. Groups such as CL0P, Qilin, and Akira have already revealed their trials to exploit zero-days in managed file transfer (MFT) software and enterprise applications. By 2026, supply chain will become the preferred entry vector.
Challenges:
- Poison software updates that are coded with back doors.
- Access broker marketplaces that sell logins and passwords for third-party vendors.
- Ransomware 3.0 – theft of your data, a Distributed Denial of Service (DDoS) attack, and disrupting or shutting down your supply chain.
Innovations Required:
- Validation of the Software Bill of Materials (SBOM) at every update.
- Predictive (or behavioral) monitoring of vendor ecosystems for suspicious exposures.
- Resilient “logically air-gapped” backup architectures that have been tested against destructive attacks.
AI Arms Race: Offense vs Defense
Adversaries are already using generative AI to conduct reconnaissance, phishing, and malware development. By 2026, expect:
- AI-enabled phishing efforts with real-time deepfakes.
- Polymorphic malware capable of mutating faster than signature detection.
- Automated reconnaissance of all exposed attack surfaces.
Defender AI-driven copilots, to keep up with this will include:
- SOC copilots that can correlate EASM alerts with threat intelligence on a global scale.
- Natural Language Processing that can surveil dark web discussions for early warning.
- Adaptive playbooks will adapt with adversary’s tactics automatically.
Autonomous EASM: The Path to Resilience
In 2026, static inventories and manual audits will be facing obsolescence. Organizations will need Autonomous EASM ecosystems:
- Automated orchestration of discovery, prioritization, patching, and response.
- Continuous red-teaming and purple-teaming powered by attack simulations.
- Real-time threat surface telemetry sharing with sector-wide intelligence fusion centers.
- Continuous resilience-first models that measure success by time-to-recovery not simply reduced exposure.
Conclusion
In the next twelve months, EASM Challenges will enter the new normal. Beyond visibility, defenders should start preparing for a future with APT disruption, ransomware-supply chain convergence, and AI-driven adversaries. The winners of this transition will be those that embrace and continuously accelerate autonomous, intelligence-led EASM programs that minimize unknown exposures. Resiliency, if created now, will drive the shock and challenges of 2026 and further the pace for the decade ahead. With the rise of EASM Challenges, companies will need to rethink their security strategies. It is vital to understand the EASM Challenges that lie ahead and act accordingly.







