Installation
gOSINT is an open source intelligence gathering tool developed in Go programming language. It is a fairly new OSINT (Open Source Intelligence) gathering tool that is still in development and open to anybody willing to contribute to its further development. It can be compared to Recon-ng in some ways even though the former is more stable and has a better interaction interface. You can read my earlier post on recon-ng from this link OSINT with Recon-ng
gOSINT is dependent on Tesseract Open Source OCR, libtesseract-dev and libleptonica-dev which have to be installed before it can be used on a machine. It can be installed on both Linux and Windows machines.
The simplest way to install it on a Linux system, which is the system most likely to be used by a hacker or penetration tester, is by using go get command:
go get github.com/Nhoya/gOSINT/cmd/gosint
We can also get it installed by first cloning the repository with the following command:
git clone https://github.com/Nhoya/gOSINT.git
and then installing the dependencies manually with:
curl https://raw.githubusercontent.com/golang/dep/master/install.sh | sh
(Without having to use Golang)
An advantage that Recon-ng has over gOSINT is that its installation is way simpler as most of its dependencies are often already available in most flavors of Linux (It comes already installed on Kali Linux as standard)
Once we are through with the installation process we can now explore the few modules that have so far been integrated and implemented in gOSINT. First we navigate to the directory from where we can run gOSINT
root@prismacsi:~/go/src/github.com/Nhoya/gOSINT/cmd/gosint#
We then type:
./gosint –help
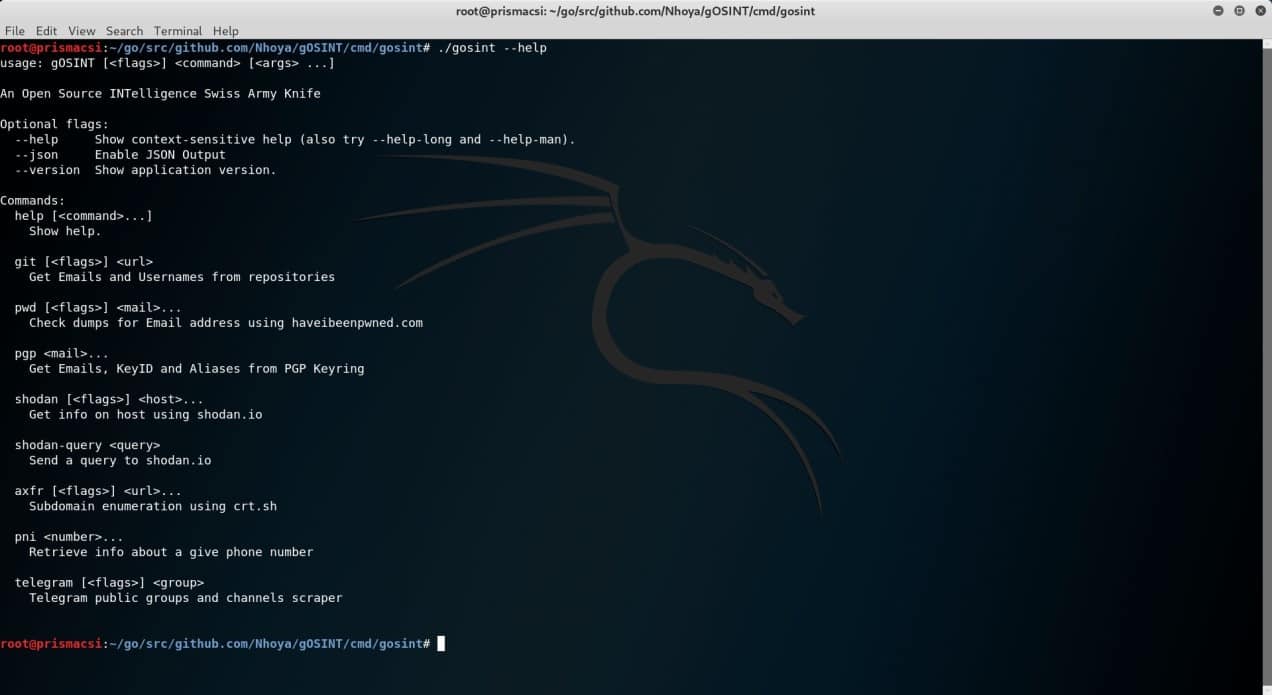 This allows us to view all the features that the tool offers.
This allows us to view all the features that the tool offers.
We can see that so far gOSINT has the following modules already implemented:
- Git support for mail retrievals with the github API or plain clone and search
- Search for email addresses, aliases and KeyID in PGP Servers
- Search for email addresses leaked in data breaches from haveibeenpawned.com
- Retrieval of Telegram Public Group Message History
- Send queries to shodan.io
- Retrieve phone number owner names
- Subdomain enumeration using crt.sh
Some of the modules are not yet fully functional but as mentioned earlier gOSINT is still work in progress. Let’s take a look at some of the few that have already been implemented.
PGP Module
This module works by searching for email addresses aliases and KeyIDs in Pretty Good Privacy (PGP) servers.
To use this module type:
./gosint pgp <domain_name>
You can see the results from two example domain names below.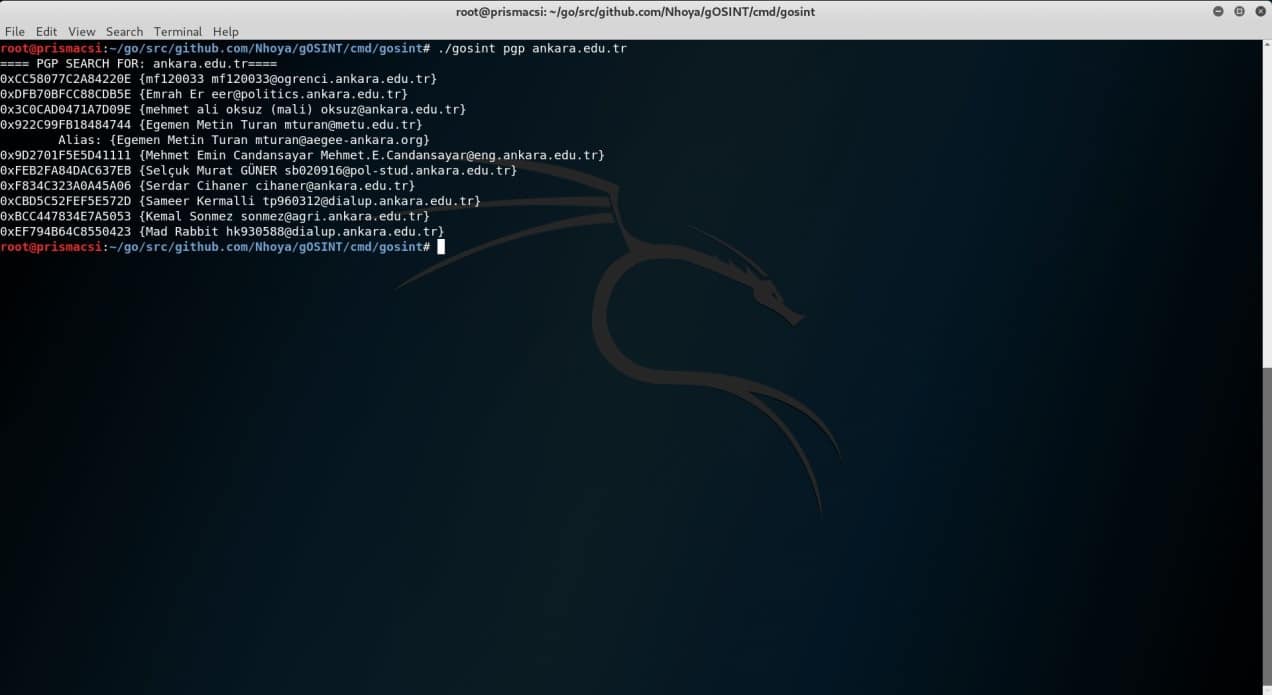
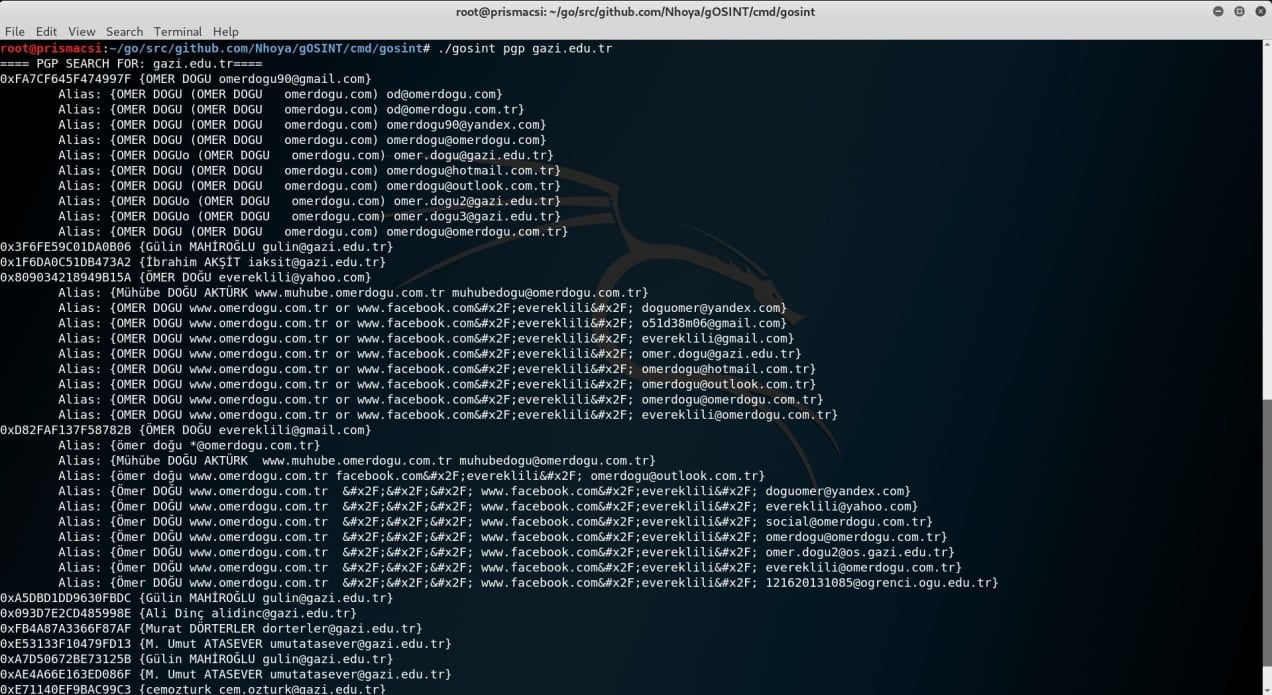 Now let’s compare the results we obtained from gOSINT with those from recon-ng shown in the screenshots below. (The two similar domain names are used in recon-ng)
Now let’s compare the results we obtained from gOSINT with those from recon-ng shown in the screenshots below. (The two similar domain names are used in recon-ng)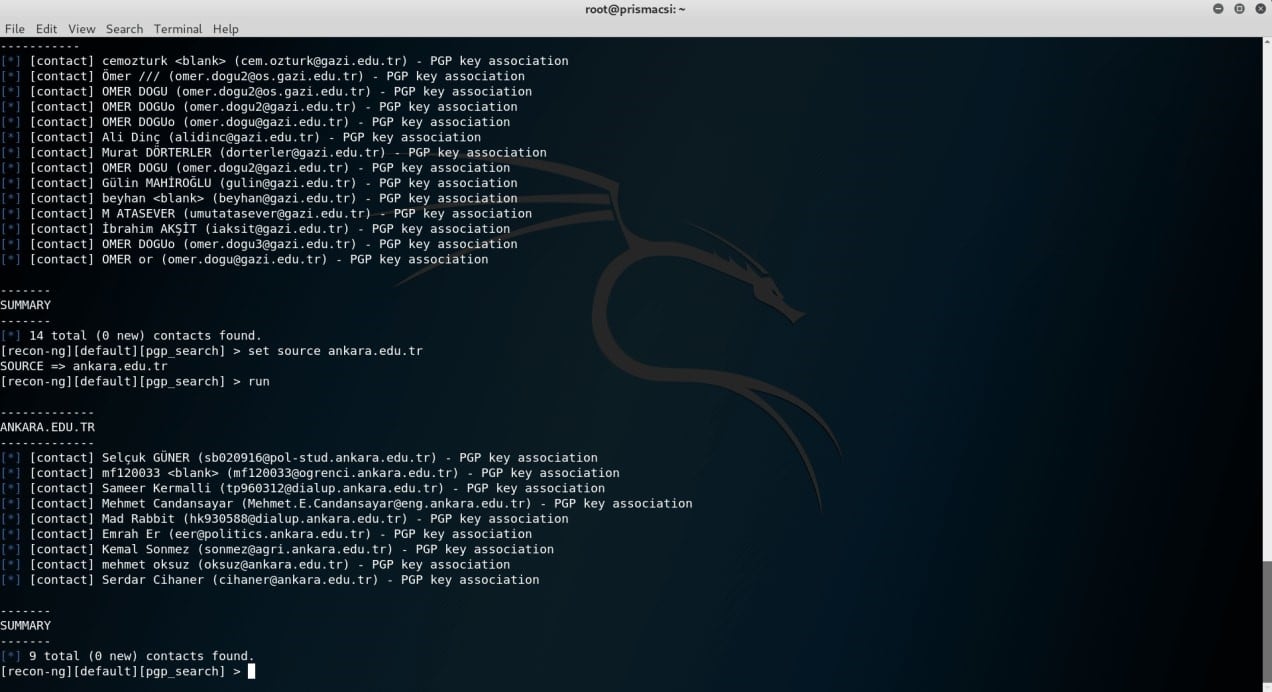 We immediately notice that even though the interface from gOSINT is less organized, the tool provides more detailed results compared to recon-ng. Any respectable computer security expert is willing to compromise and settle for more detailed results instead of a better looking interface.This however does not mean that recon-ng does not get the job done, on the contrary it saves the user a lot of headache by directly saving the retrieved data in its internal database. This can prove very useful in later reconnaissance expeditions.
We immediately notice that even though the interface from gOSINT is less organized, the tool provides more detailed results compared to recon-ng. Any respectable computer security expert is willing to compromise and settle for more detailed results instead of a better looking interface.This however does not mean that recon-ng does not get the job done, on the contrary it saves the user a lot of headache by directly saving the retrieved data in its internal database. This can prove very useful in later reconnaissance expeditions.
PNI Module
This module in gOSINT looks up phone numbers in sync.me servers and returns the owner names. It is yet to be fully functional as it’s currently obstructed by CAPTCHA but that is expected to be rectified once more developers get involved with the module. The screenshot below shows the results that can be obtained from the module in its present state.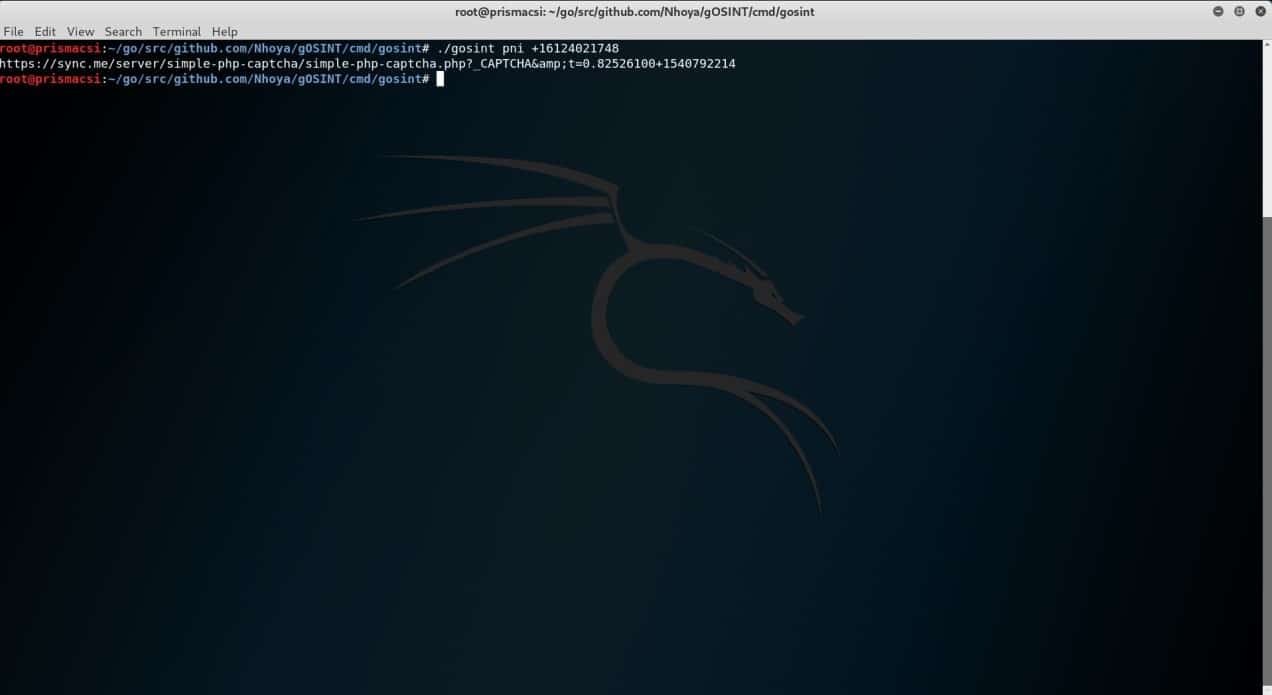 Recon-ng does not have a module that performs this exact function but has one which is able to return a list of email addresses and names associated with a given host or domain name. Take a peek at the screenshots below.
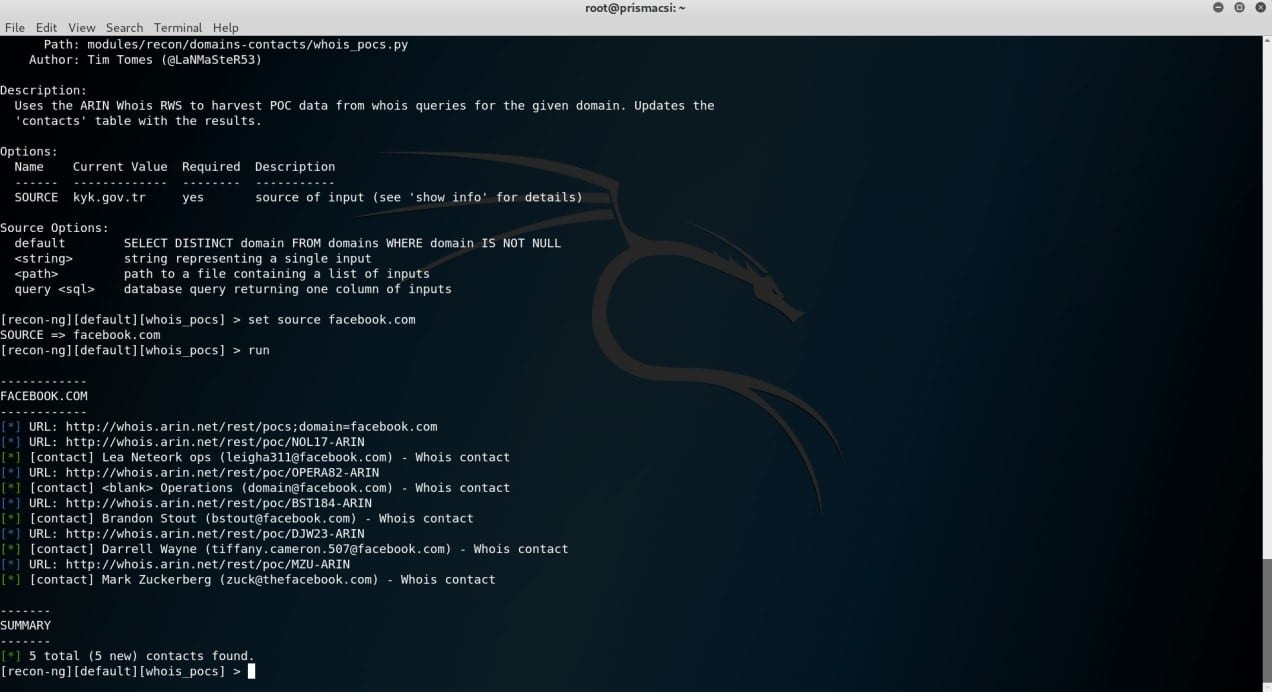
Recon-ng does not have a module that performs this exact function but has one which is able to return a list of email addresses and names associated with a given host or domain name. Take a peek at the screenshots below.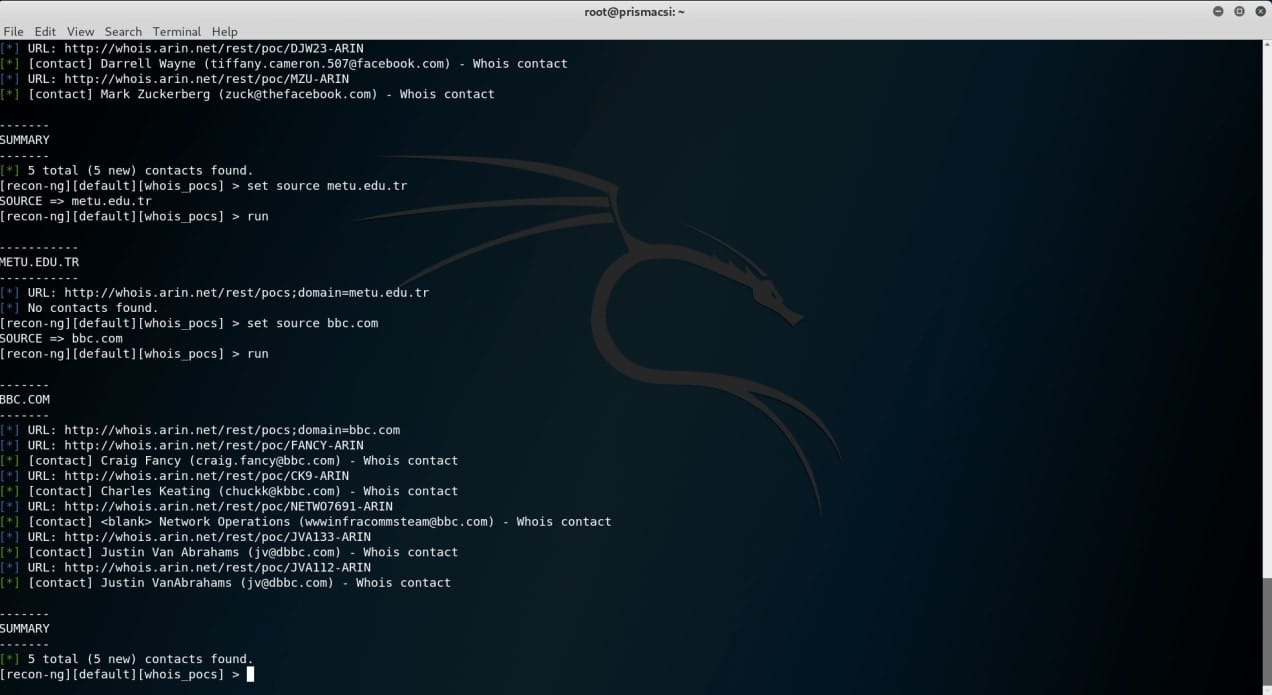
PWD Module
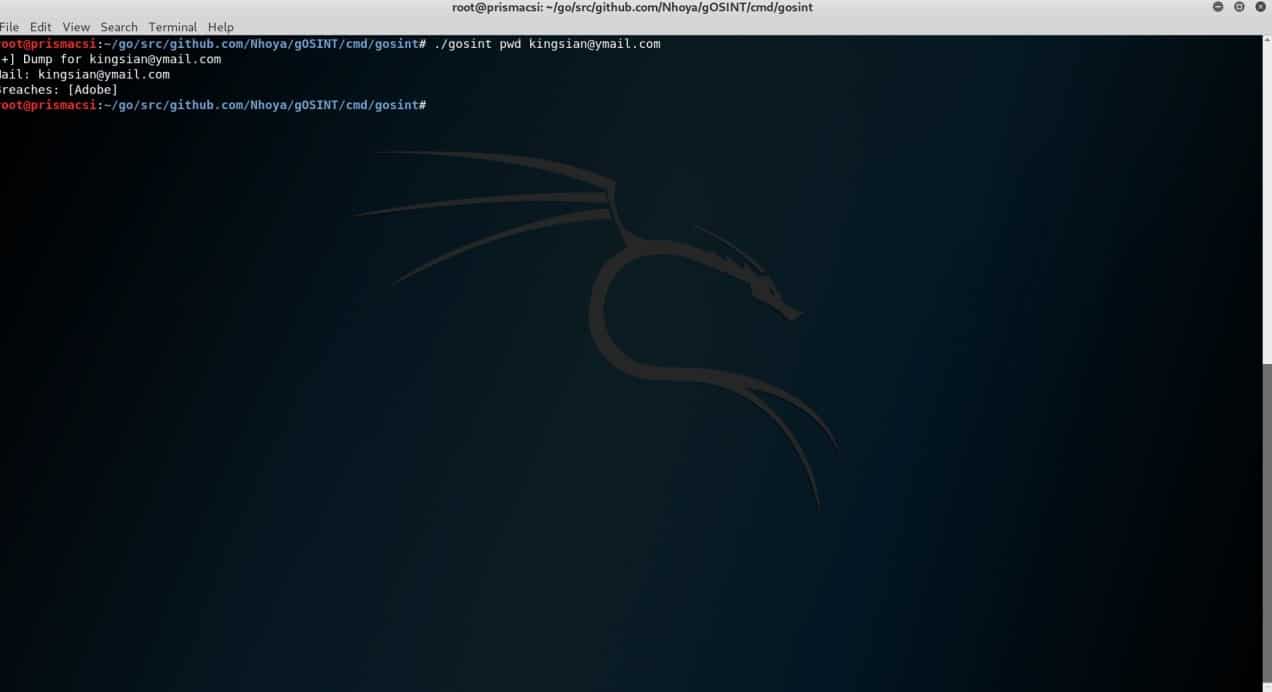
The module utilizes the services of haveibeenpawned.com. It checks dumps for email addresses that might have been leaked in past data breaches. This can be a potential source of targets for a hacker. Penetration testers would therefore advice companies whose employees have email addresses appearing in such gOSINT command execution results to take better proactive measures in securing their email accounts. An example is shown in the screenshot.
The command format is:
./gosint pwd <email_address>
Shodan Module
This is the final currently functional module that we will take a look at in this post. According to its Wikipedia definition, Shodan is a search engine that allows users to find specific types of computers connected to the internet via custom filters.
Shodan implementation on gOSINT is still basic but it performs the intended function including discovering honeypots which are often set up to wade off intrusive attacks on an organization’s computer and network infrastructure.
./gosint shodan 23.22.39.120 honeypot
Returns the results below.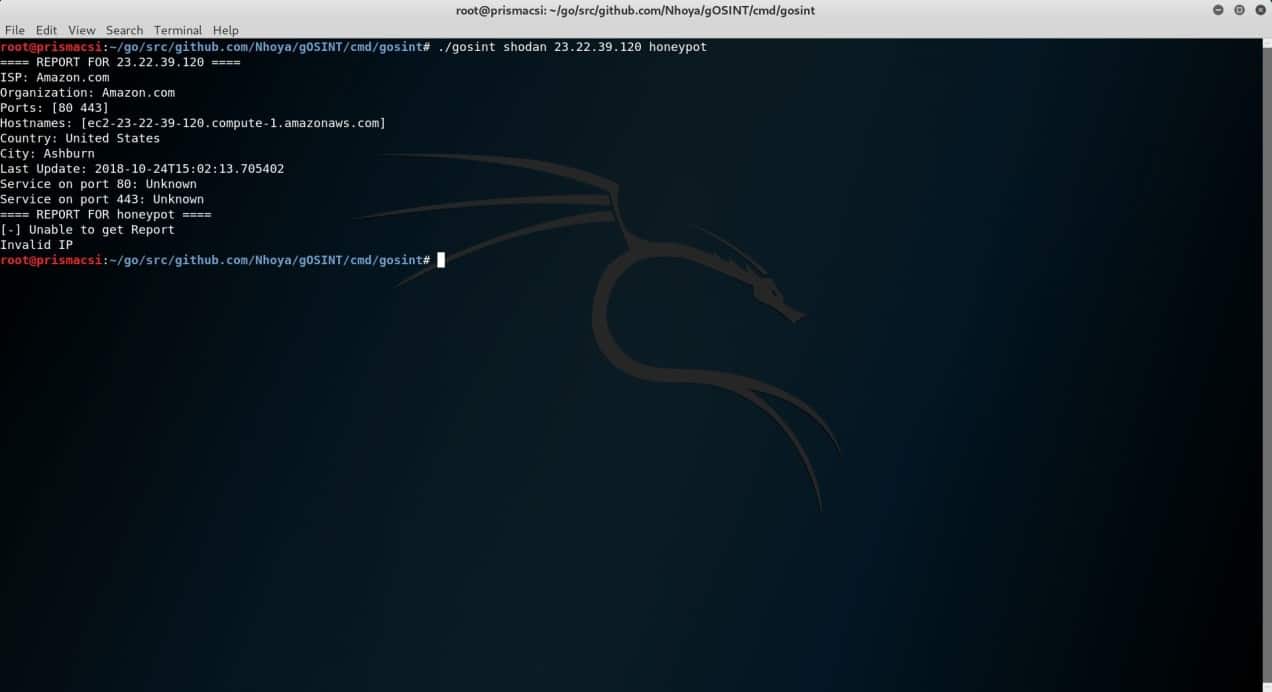 shodan.io allows performance of a multitude of different searches while applying a variety of filters but not many have so far been implemented in gOSINT’s shodan module. That will probably change in the future as more developers get involved in the open source project. Considering what recon-ng offers, gOSINT still has a long way to go. The following extracts are from an execution of a shodan module on recon-ng that returned several host names associated with the specified domain name.
shodan.io allows performance of a multitude of different searches while applying a variety of filters but not many have so far been implemented in gOSINT’s shodan module. That will probably change in the future as more developers get involved in the open source project. Considering what recon-ng offers, gOSINT still has a long way to go. The following extracts are from an execution of a shodan module on recon-ng that returned several host names associated with the specified domain name.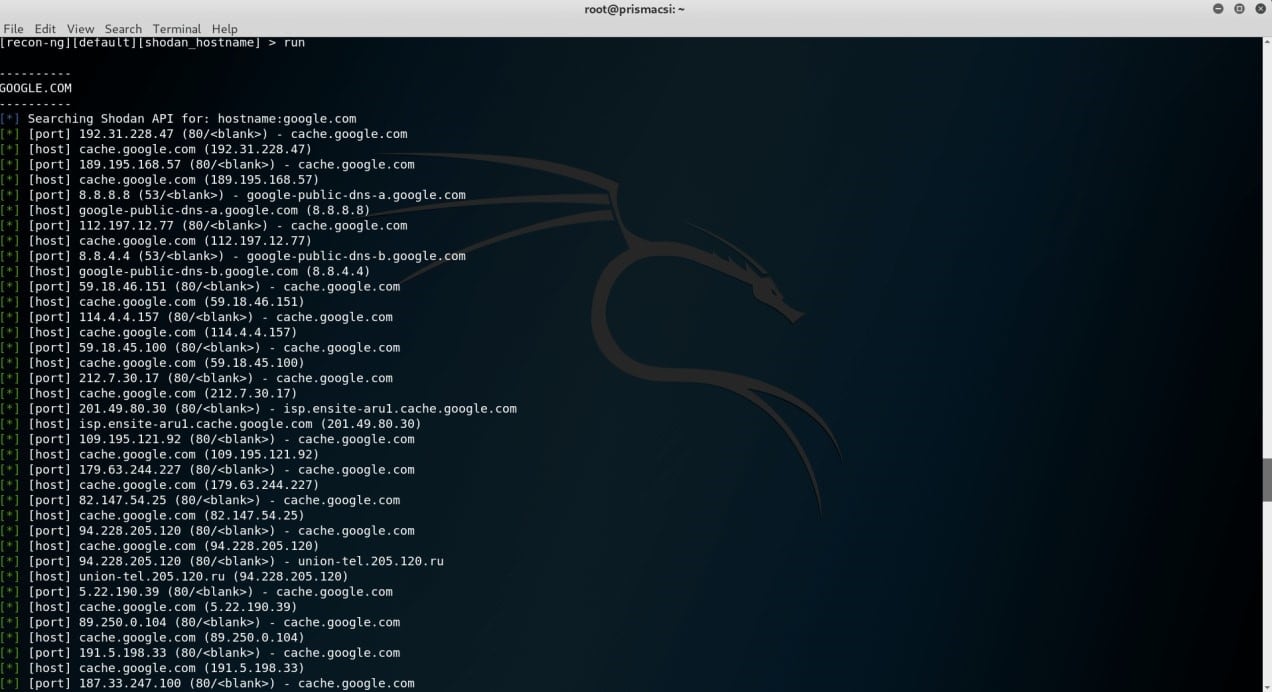
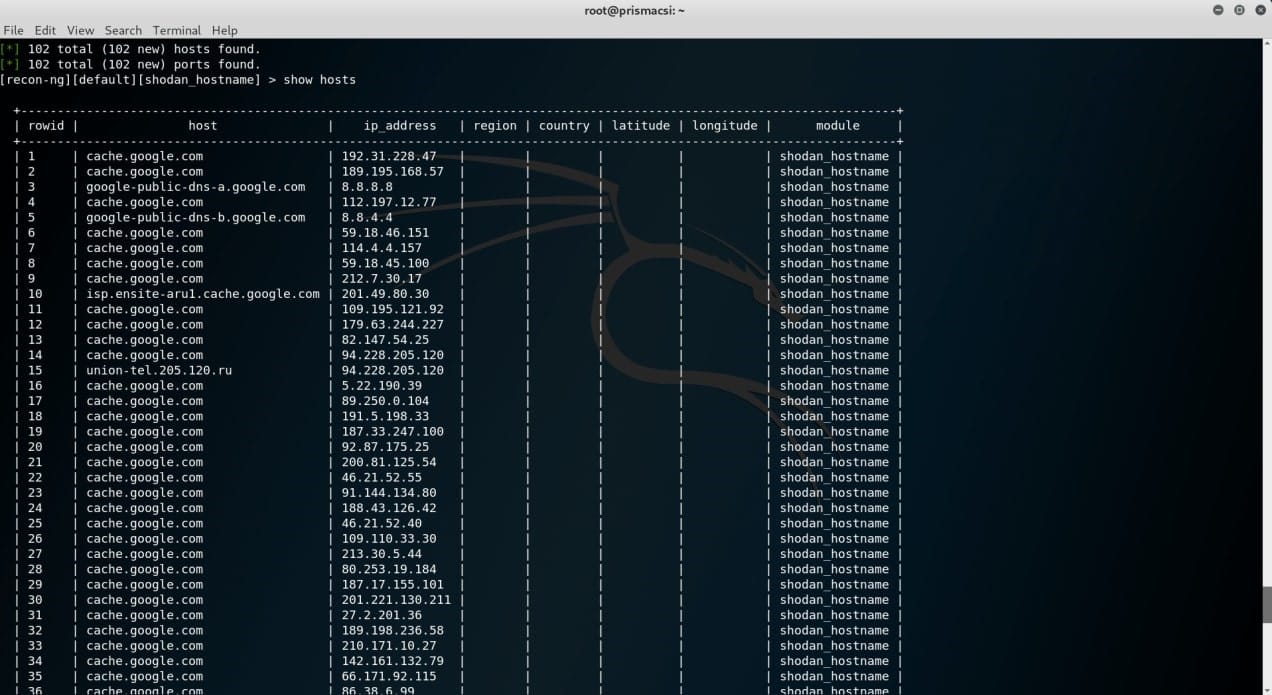 This shows just how well recon-ng organizes its results in databases, which is crucial for any penetration tester or hacker looking to save a little more time in their OSINT recon. It is the reason why it has been a number one go to recon tool for many users involved in massive intelligence reconnaissance before a hack or an attempt to penetrate any computer system/infrastructure. New tools like gOSINT are a welcome thought given the docile state that recon-ng has fallen into in the past few years with respect to development improvements. gOSINT has the potential of being a very powerful recon tool once all its modules are up and running properly. Only time will tell if the tool can live up to that potential.
This shows just how well recon-ng organizes its results in databases, which is crucial for any penetration tester or hacker looking to save a little more time in their OSINT recon. It is the reason why it has been a number one go to recon tool for many users involved in massive intelligence reconnaissance before a hack or an attempt to penetrate any computer system/infrastructure. New tools like gOSINT are a welcome thought given the docile state that recon-ng has fallen into in the past few years with respect to development improvements. gOSINT has the potential of being a very powerful recon tool once all its modules are up and running properly. Only time will tell if the tool can live up to that potential.
If you have a question about the blog post, you can contact us.
Ian Kings





