Introduction
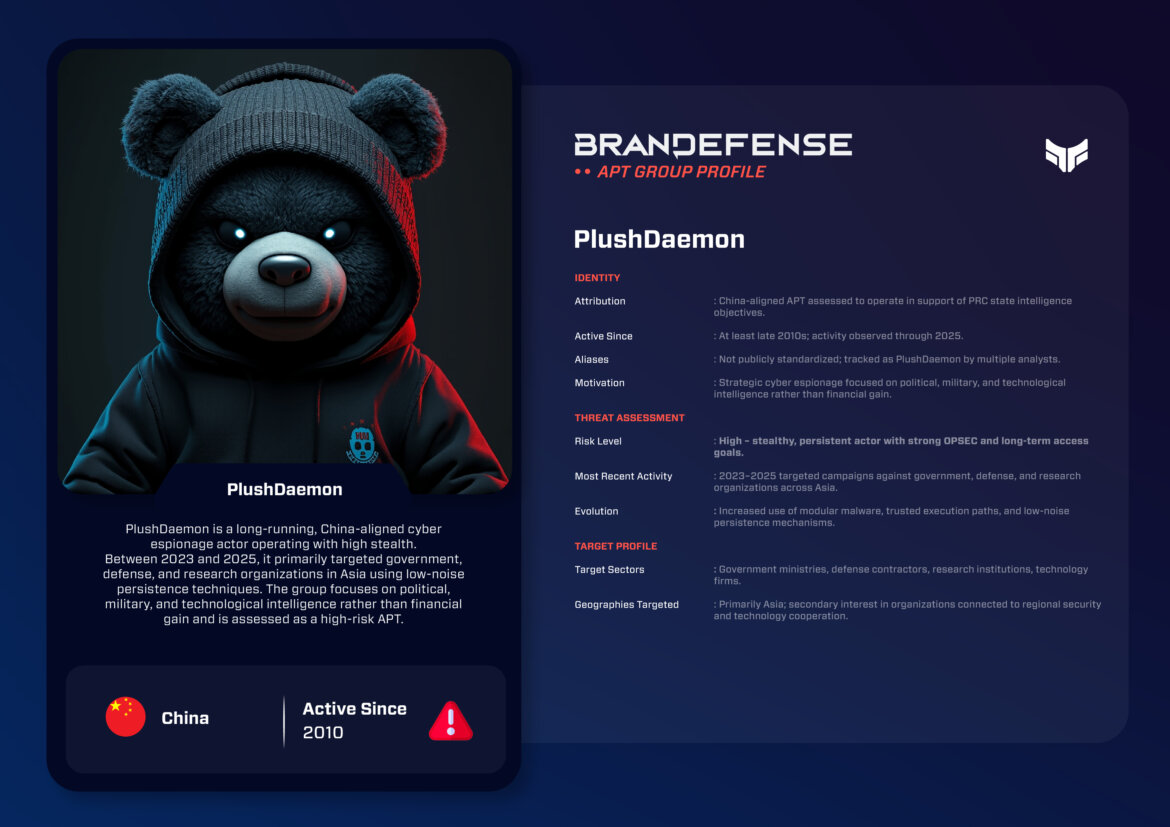
PlushDaemon is a well-organized advanced persistent threat (APT) group attributed to the People’s Republic of China (PRC) that has conducted long-term cyber espionage against high-value targets in Asia and globally. PlushDaemon operates in a quiet, methodical, and discreet manner, demonstrating many of the characteristics associated with China’s current approach to cyber espionage, including low noise, a high degree of operational security, and an emphasis on obtaining information that will be of strategic value to the PRC, rather than simply causing disruption.
PlushDaemon has targeted a variety of organisations, including government agencies, defence contractors, research institutions, and technology companies. The information and communications obtained via cyber espionage aligns with many of China’s current geopolitical and military objectives.
This intelligence blog provides an overview of the group, including its definition, reasons for existence, techniques, tactics, and procedures, and information regarding how the group adapted and continues to pose a major and sustained threat in the international cyber environment.
Identity & Motivation
PlushDaemon translates as “Pillowy Monkey,” which captures the identity and motivations of this China-affiliated advanced persistent threat (APT) group. This group primarily conducts cyber espionage on behalf of the Chinese government and uses custom designed malware, frameworks and tools to compromise their targets. Their operations are less publicly documented than many other more well-known China APT groups, yet their tools, victimization patterns and modus operandi correlate strongly with either the Ministry of State Security (MSS) or other departments within the Chinese Intelligence Services.
This group has been linked to the Government of China by using an attribution type that is indicative of state-sponsored activity. These actors have been operating since late 2010 and as of 2022 are steadily gaining traction throughout 2022-2025.
Motivation: PlushDaemon is engaged in strategizing around cyber espionage encompassing political, military and/or technological collection activities borne of longer term access requirements to sensitive information networks within China aligning cycles based Europen protocols, country partnerships and national priorities for China. This includes alignment of defence co-operative plans and emerging technology developments with National Security Interests.
TTPs: Methods, Tools, and Access Strategies
The operations of PlushDaemon are characterised by stealth, persistence, and careful targeting, as opposed to the use of noisy exploits. Instead, the group prefers to rely on using trusted execution paths; abusing legitimate software; and the use of multi-staged malware frameworks.
Initial Access
PlushDaemon typically gains initial access through:
– Highly targeted spearphishing emails that are tailored towards specific organisations or individuals.
– Lures that have been themed to match government policy, defence cooperation, or technical documentation.
– Malicious attachments/archives that rely on exploiting the user trust as opposed to attempting to exploit large numbers of vulnerabilities.
– The occasional use of compromised websites to host payloads that are used for watering-hole-style delivery.
The phishing content produced by PlushDaemon is usually contextual, well-written, and localised which indicates that the group has conducted a thorough reconnaissance against the target.
Execution and Tooling
Once access is gained, PlushDaemon creates custom malware components with the goal of reducing the chance of detection. Examples of these components include:
– Lightweight loaders used to decrypt the malware payload in memory
– Custom built backdoors that allow the attacker to execute commands, manipulate files, and gather system information
– Modular implants which allow the attacker to turn on or off individual capabilities depending on the attacker’s needs
In order to reduce the number of alerts triggered by their activities, attackers often use legitimate system processes to execute their code.
Persistence
PlushDaemon maintains long-term access through the use of a variety of mechanisms, including:
– Registry auto-run entries
– Scheduled tasks (with innocent-looking names)
– DLL side-loading (placing malicious DLLs next to legitimate executables)
– Multiple ways to maintain their presence; if one method is blocked or removed, there will always be at least one other way to gain access again.
This layered persistence approach allows the group to maintain their presence inside the victim’s network for an extended period of time.
Command and Control (C2)
The group’s Command & Control (C2) infrastructure is set up in a way to be as conservative as possible:
– Communication is encrypted over HTTPS
– Compromised servers/rented infrastructure is used for masking their origin.
– The group rotates their domains and IP addresses frequently.
– They send out low-frequency beacons to blend in with normal network traffic.
The C2 traffic is often indistinguishable from normal web traffic which makes it difficult to detect on the network.
Defense Evasion
The operational security of PlushDaemon is demonstrably robust due to several factors:
– The use of obfuscation and encryption to conceal the payload.
– The use of living-off-the-land techniques that do not leave significant artifacts of their use.
– The deliberate timing of actions to prevent triggering anomaly-based monitoring.
These tactics indicate a sophisticated operator who places a greater value on long-term success than rapidity of success.
Data Collection and Exfiltration
PlushDaemon targets several types of data for collection:
– Policy documents and internal operational guidelines.
– Research data and design documents.
– Email conversations between high-level personnel.
– Network configurations and access credentials.
PlushDaemon exfiltrates data in a slow, methodical manner by transferring compressed, encrypted data in small increments in order to elude data loss prevention software.

Notable Operations
Publicly, PlushDaemon chooses not to promote the operations it conducts but rather displays characteristics seen from other activities carried out by them.
Government and Defense Targeting
When conducting government and defense targeting, the attacks have been identified with intrusion occurrences within various ministries of government and military-related entities across Asia, these targeting incidents appear to be timed with regional security developments or the establishment of defense cooperation agreements. Therefore it is believed the group is conducting these operations based upon intelligence needs for future policy-making and military planning.
Technology and Research Espionage
The group has targeted technology companies, research establishments & institutes working with technology, advanced manufacturing, and Dual-Use Technology. Having access to the information helps facilitate the advancement of domestic technology and to provide strategic guidance.
Long-Term Network Surveillance
While most groups will immediately extract large amounts of data, PlushDaemon prefers to gain access quietly and maintain persistent monitoring over time, allowing the collection of richer intelligence with less chance of detection.
Recent Developments (2023–2025)
Recent findings have shown that the development of PlushDaemon continues to be improved through its tradecraft.
Better Modularity: As the malware components grow increasingly modular, operators can customize performance capabilities to match each individual target’s need.
Better OPSEC: The infrastructure rotation process is now being performed in a much more disciplined manner, with lesser levels of indicator reuse from previous campaigns.
Cloud Aware: Though attempts to degrade cloud service usage are not heavily enhanced, the shopper is aware of hybrid environments that target endpoints that easily bridge the on-premise/cloud divide.
Targeted Effectiveness: Campaigns are small in size compared to the number of campaigns targeting the same individual; however, the targeted nature of the campaign allows the shopper to receive quality intelligence rather than quantity.
Strategic Impact
PlushDaemon helps serve the Chinese government’s wider intelligence efforts in a multitude of ways.
Political Insight: The ability to access the communications of governments gives one insight into their policy discussions, negotiations strategies and alliance-building/dynamics.
Military Advantage: Espionage that targets organizations that are closely related to the military can support military capability developments and strategic planning.
Technological Edge: Theft of technical and research information shortens the timeline to develop and helps business/industry become more competitive in key global sectors.
Regional Influence: By continuously monitoring the activities of the states that surround China, one can monitor the status and awareness of developments and perform influence operations.
PlushDaemon may not have garnered the type of headlines that attract attention but through their consistent and reliable actions they provide a quality resource to support the Chinese Government’s intelligence collection and use of cyber-espionage capabilities.
Conclusion
PlushDaemon is an example of a disciplined and low profile Advanced Persistent Threat (APT) that operates primarily in China, and has high priority on stealth, persistence and intelligence collection of a targeted nature. The group’s focus on government, defense and technology organizations indicates its role in supporting China’s state level strategic objectives, and not necessarily short-term gain.
As more organizations increase their perimeter defence capabilities, actors such as PlushDaemon illustrate that the vast majority of risk originates from low-key, highly tailored intrusions that evade detection for extended periods of time (months to years). Effective defence against those types of advanced persistent threats (APTs) will require an organisation to have strong identity security, a comprehensive set of continuous threat intelligence, up-to-date knowledge of adversary tradecraft, and ongoing behavioural monitoring. Consequently, it is highly likely that PlushDaemon will remain a relevant and dynamic threat to organisations for the foreseeable future.
You can download and review the sheet for all the details!







