Introduction
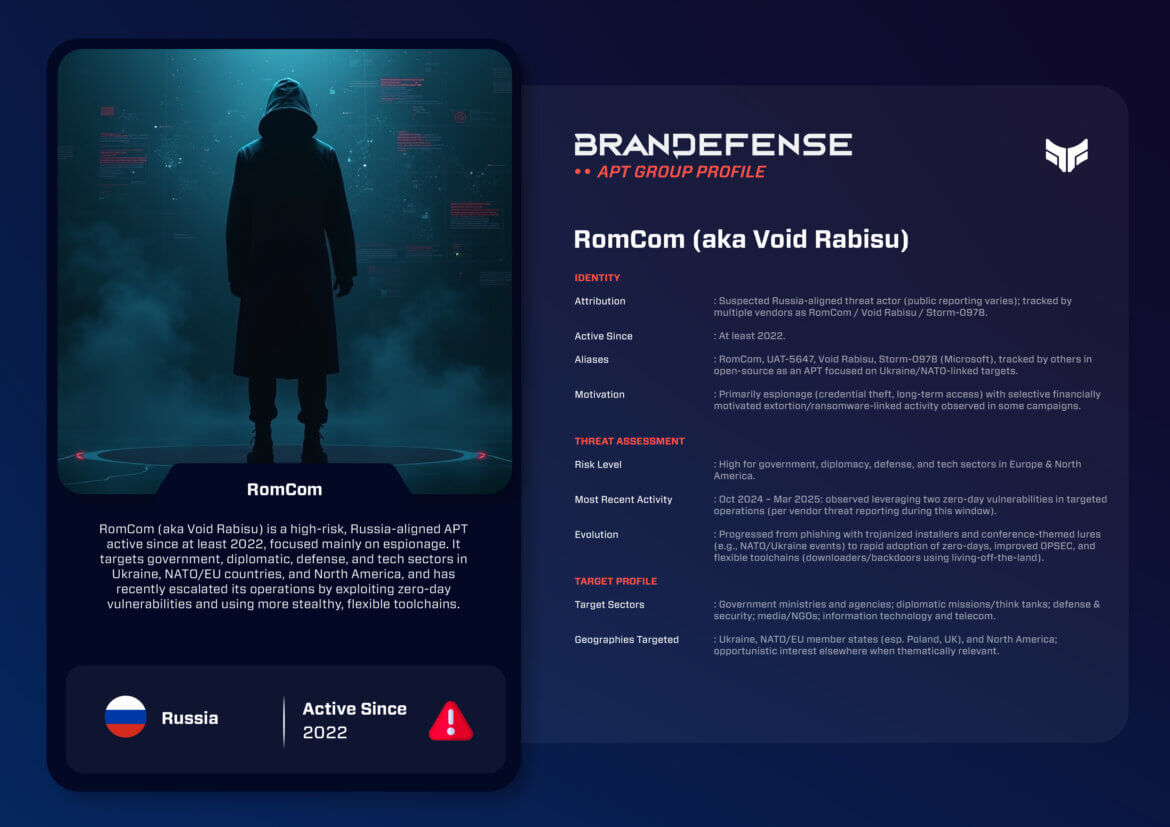
RomCom, also known as Void Rabisu, Storm-0978, and UAT-5647, has quickly become one of the most notorious advanced persistent threat (APT) groups in the last couple of years. Established in 2022, the group has garnered a reputation around targeted espionage operations against NATO-affiliated states, specifically states that support Ukraine. RomCom’s campaigns epitomize a dangerous cocktail of political motivation, technical sophistication, and opportunistic financial gain.
Similarly to older APTs that built reputations over the course of a decade, RomCom accelerated its reputation through the rapid adoption of zero-day vulnerability exploitations, large-scale phishing campaigns, and a quick-switch capability of infrastructure and tooling. This agility informs RomCom’s status as a significant strategic threat for governments and enterprises alike.
Identity & Motivation
RomCom is considered to have Russia affiliations, but whether it directly ties to the Russian state is still unclear. Vendors differ on how they attribute the groups, as Microsoft calls the group Storm-0978, CrowdStrike calls them Void Rabisu, and others refer to them as UAT-5647. The group seems to exhibit a dual-track motivation of:
– Espionage: harvesting sensitive political, military and diplomatic intelligence against Ukraine, NATO, and allied nations.
– Financial gain: several operations have been associated with ransomware-style extortion, either as a sitting cover for espionage or to potentially gain more sources of income.
The hybrid nature of RomCom also complicates attribution and adds uncertainty around predicting RomCom’s campaign, as political as well as financial incentives may impact operational decisions.
TTPs
RomCom’s approaches in tactics, techniques, and procedures (TTPs) exhibit a high degree of adaptability and rapid change:
– Initial Access:
– Spearphishing with Trojanized installers for legitimate tools (KeePass, Advanced IP Scanner)
– Fake event portals around NATO and Ukraine-related conferences
– Exploitation of Microsoft Office and WinRAR zero-day exploits in 2024-2025
– Persistence:
– Registry edits and scheduled tasks.
– Lightweight custom backdoors designed to blend into normal traffic.
– Living-off-the-land binaries abuse.
– C2 Infrastructure:
– Encrypted, HTTPS-based channels.
– Domain fronting and rotating disposable infrastructure.
– Hosting on commercial cloud services for plausible deniability.
– Malware & Tools:
– RomCom RAT, the signature remote access trojan.
– Custom droppers and downloaders.
– Commodity tools (Mimikatz and Rclone).
– Techniques:
– Credential harvesting of Outlook, browsers, and Windows authentication.
– Privilege escalation via multiple exploit chains.
– Data exfiltration to cloud storage
– Flexible use of open-source and custom tools to evade detection.

Notable Operations
RomCom’s campaigns demonstrate a noticeable path of increasingly sophisticated efforts and ambition:
- 2022: The first observed campaigns utilized trojanized installers to deliver RomCom RAT to multiple Ukrainian government and military officials.
- 2023: Campaigns that utilized NATO-summit-themed lures as well as lures based around political events in Europe followed, and included spoofed conference sites.
- 2024: These campaigns culminated in a well-publicized operation using decoy sites based around the Ukraine Recovery Conference, where RomCom’s target set included North America.
- 2025: Rehabult used two zero-day exploits in early campaigns, and RomCom had attacks on several Ministries and Defense targets throughout Europe, which indicates that RomCom possesses access to advanced exploit capabilities.
These operations are not only indicative of strategic targeting in Europe that aligns with Russian geopolitical interests, but they are also opportunistic operations against more general Western networks.
Recent Developments
In late 2024 and early 2025, RomCom was reported to use two different zero-day vulnerabilities, pointing to their propensity to gain or create advanced exploit research. That represents a significant progression, moving the group from mid-tier phishing-dependent activities to advanced persistent threat (APT)-type sophistication.
Recent campaigns also show:
- More believable phishing infrastructure, with cloned conference websites, which closely resemble legitimate websites.
- A switch to faster operational cycles and rotating infrastructure, to avoid takedown.
- Some operations included financially motivated payloads, suggesting hybrid goals.
Conclusion
RomCom is a strategic cyber threat to NATO states and partners. The ability to marry espionage and opportunistic financial operations makes RomCom unpredictable. RomCom’s rapid adoption of zero-days vulnerabilities and increasing operational sophistication indicate they may be in it for the long haul and likely expand targeting opportunities given the current geopolitical climate.
Defensive Takeaways:
- Patch Management: Organizations must act quickly to prioritize patching, especially for Office and compression software like WinRAR.
- Threat Hunting: Look out for unusual installer downloads, especially if they are conference-themed and unusually downloaded.
- Infrastructure Monitoring: Look for unusual HTTPS traffic that involves frequent domain change and suspicious use of cloud hosting.
- Awareness Training: Employees in government, defense and NGOs should get training to recognize phishing campaigns connected to current geopolitical events.
RomCom is a classic example of how rapidly maturing APTs can impact and shift the threat landscape in a matter of years. Security teams should treat this as an advanced threat actor that has both strategic intent and technical sophistication.
You can download and review the sheet for all the details!







