The holiday season is a peak period for e-commerce, as consumers flock online to take advantage of deals and convenient shopping options. However, this surge in activity also attracts cybercriminals, making robust e-commerce cybersecurity practices essential for businesses and consumers. Protecting sensitive customer data, securing payment transactions, and mitigating vulnerabilities should be top priorities to ensure safe and seamless operations during this critical time. Adopting a multi-layered approach to cybersecurity can safeguard businesses from the increasing threats posed by attackers. This includes implementing website vulnerability scans, enhancing payment gateway protections, and preparing comprehensive incident response plans for potential data breaches. By staying vigilant and proactive, e-commerce platforms can maintain customer trust and reduce the likelihood of financial and reputational damages during the holiday season.
E-Commerce Fraud Prevention: Securing Customer Transactions
Fraud prevention is fundamental to maintaining trust in e-commerce, especially as cybercriminals continue to devise sophisticated methods to exploit digital transactions. Businesses must implement measures that secure customer data and financial information against threats such as phishing schemes, unauthorized account access, and deceptive transactions. Advanced e-commerce fraud prevention systems have emerged as a powerful solution, leveraging artificial intelligence and machine learning to detect unusual patterns and identify potential risks in real-time. These tools analyze transaction behaviors, flag anomalies that may indicate fraudulent activity, and allow security teams to take immediate action.
Multi-factor authentication (MFA) is pivotal in enhancing protection by requiring customers to confirm their identities through multiple secure channels. Educating consumers on safe shopping habits, such as verifying website credibility and avoiding untrusted links, also protects against fraud. Encouraging users to use strong passwords and secure payment methods and regularly monitor their accounts further reinforces the protective framework. By integrating cutting-edge technology with proactive consumer education, businesses can create a robust environment that prioritizes the safety of every transaction.pply chain. A disgruntled employee, or one who unknowingly clicks on a malicious link, can introduce malware or grant unauthorized access to critical systems.
Protecting Payment Gateways from Cyber Threats
As the backbone of digital commerce, payment gateways are a prime target for cybercriminals aiming to intercept sensitive financial data. Securing these gateways requires a comprehensive strategy incorporating technological enhancements and consistent vigilance. End-to-end encryption ensures data is securely transmitted, rendering it inaccessible to unauthorized entities. Encrypted systems shield payment details from interception, providing an essential layer of protection for customers and businesses.
Keeping systems updated is equally critical for maintaining payment gateway security. Outdated software and unpatched vulnerabilities often serve as entry points for attackers. Fraud detection algorithms further enhance gateway defenses by identifying unusual transaction patterns and blocking suspicious activities before they escalate. Tokenization technology offers an additional safeguard by minimizing the impact of data theft. By adopting these measures, businesses protect payment channels and build trust among their customers, ensuring safe and seamless transaction experiences.
Conducting Website Vulnerability Scans Before Peak Seasons
The importance of website vulnerability scans must be balanced, particularly in preparation for high-traffic periods like holiday shopping. These scans are a proactive measure to uncover weaknesses that cyber adversaries could otherwise exploit. Tools designed for website vulnerability scans meticulously inspect a website’s infrastructure, identifying issues like outdated software, insecure configurations, and unprotected open ports that may serve as entry points for attackers.
Addressing identified vulnerabilities through timely patching and reconfiguration is vital in mitigating risks. This approach extends to continuous monitoring, ensuring that newly emerging threats are promptly addressed and that the website remains secure despite high traffic loads. Businesses prioritizing these scans reduce their exposure to cyber threats and enhance the user experience by providing individuals with a reliable shopping environment. This fosters greater customer trust and loyalty, contributing to sustained business success.
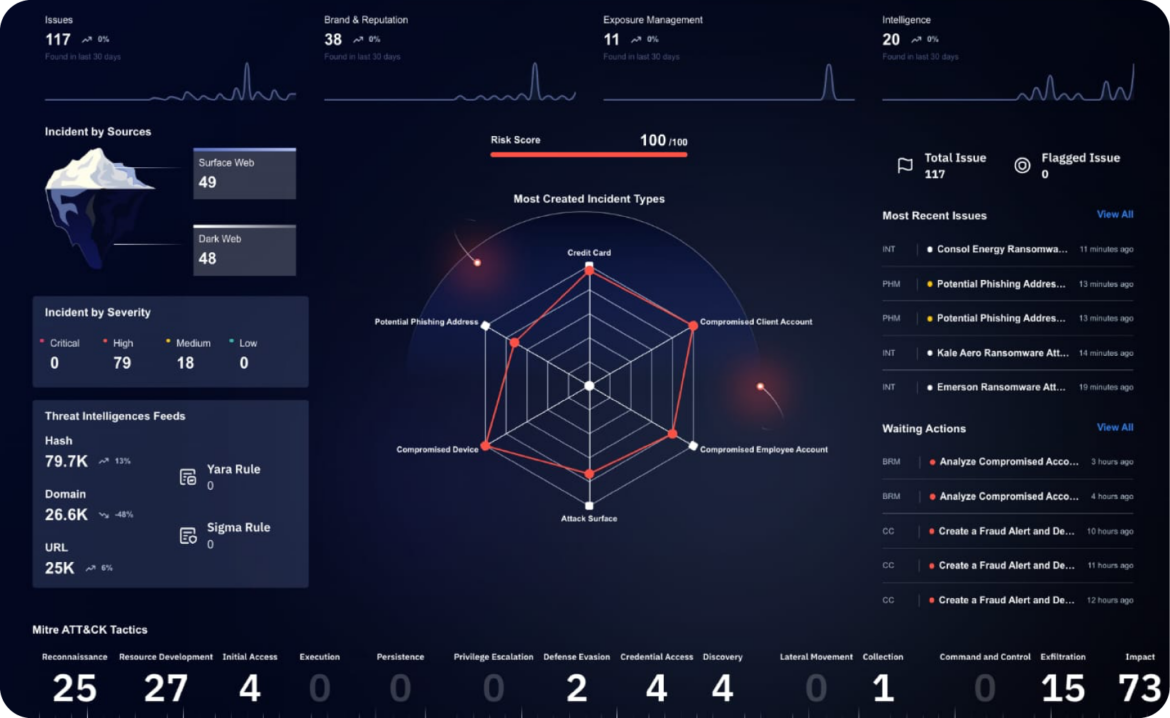
Digital Risk Intelligence for E-commerce Security
Staying ahead of cyber threats in the dynamic e-commerce landscape requires leveraging real-time digital risk intelligence. This intelligence empowers businesses with actionable insights into emerging risks, enabling them to address vulnerabilities and thwart potential attacks proactively. By monitoring a broad spectrum of digital spaces, including the deep and dark web, businesses can detect mentions of their brand, stolen credentials, and other indicators of impending threats.
Integrating digital risk intelligence into existing security operations streamlines threat identification and response. Automated systems provide prioritized intelligence, allowing security teams to focus on genuine threats. This intelligence-driven approach ensures businesses can adapt to the evolving threat landscape, safeguarding their assets and operations. By combining these tools with strategic planning, organizations can enhance their ability to defend against known and emerging cyber risks, ensuring a secure environment for e-commerce activities.
Incident Response Plans for E-Commerce Data Breaches
Data breaches represent the most significant threats to e-commerce, potentially compromising sensitive information and eroding customer trust. Establishing comprehensive incident response plans is essential for minimizing the impact of such events. These plans should clearly define protocols for identifying, containing, and resolving breaches, ensuring that every action is coordinated and efficient. This involves deploying robust monitoring systems capable of detecting unauthorized access and unusual activities as they occur.
A dedicated incident response team with clearly assigned roles and responsibilities ensures that businesses can act swiftly in the event of a breach. Tools leveraging threat detection automation expedite the identification of malicious activities, enabling quicker containment and mitigation. Testing and refining these plans regularly is critical for ensuring readiness. By preparing for potential breaches with well-structured incident response plans, businesses can protect their reputation, maintain compliance with regulatory standards, and foster customer confidence.






