Introduction
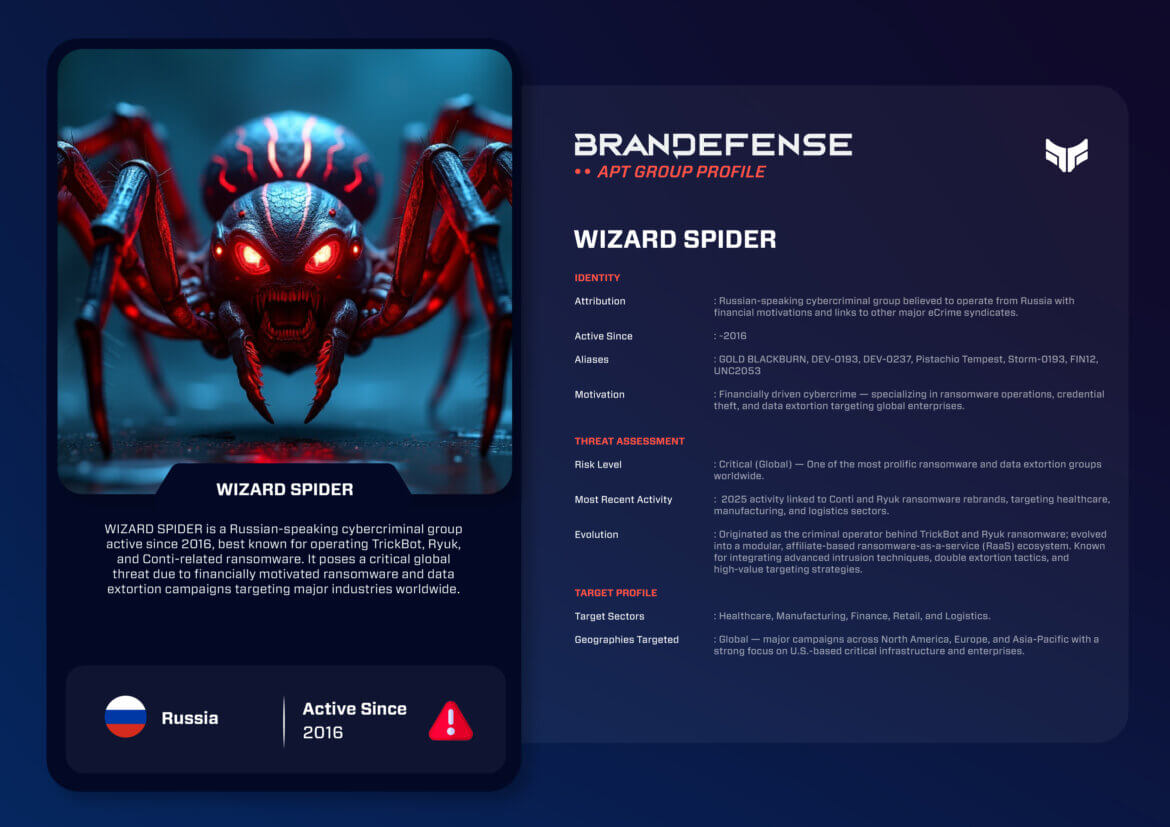
WIZARD SPIDER, also known by various aliases including FIN12, GOLD BLACKBURN and DEV-0193, is one of the most active cyber criminal groups operating to date. The group has been active since at least 2016 and has become synonymous with large scale ransomware attacks credential theft, and the industrialization of cyber extortion, among other nefarious cybercriminal activity. WIZARD SPIDER emerged from the shadows of TrickBot and Ryuk ransomware operations into a complex affiliate-based cybercrime network in the eCrime ecosystem. WIZARD SPIDER incorporated asymmetrical layers associated with organized crime and potentially state tolerated cyber activity, operating primarily from Russia and adjacent CIS countries.
WIZARD SPIDER’s hallmark is its ability to rapidly adapt to law enforcement pressure while evolving its toolsets, infrastructure, and business plan. The group unrolled TrickBot as a banking Trojan making its eventual way to deploying Ryuk, Conti and now Black Basta ransomware into a situation to which WIZARD SPIDER paved the way for modern ransomware as a service (RaaS). WIZARD SPIDER continues to pose serious financial and operational damage to organizations across the global critical infrastructure.
Identity and Motivation
The core motivation of WIZARD SPIDER is financial in nature. Unlike most nation-state threat actors, it does not directly pursue espionage or geopolitical objectives, but rather means it operates in a permissive environment of Russian cybercriminal safe havens, where prosecutions of attacks on foreign targets are rare at best.
Key motivations are:
1. Financial Gain: It focuses primarily on extorting its victims for financial gain through ransomware and data leaks.
2. Monetization of Access: It sells network access to affiliate actors and partners with other Ransomware as a Service (RaaS) groups to expand access.
3. Ecosystem Dominance: It establishes long-term, collaborative relationships with developers of loaders and infostealers, while also establishing initial access with other affiliates.
While profit is the ultimate principle this group operates under; the organizational structure and resilience of the group suggests an organized, business-like hierarchy on the same spectrum as multinational criminal enterprises.
Tactics, Techniques, and Procedures (TTPs)
WIZARD SPIDER has established a solid, repeatable operating model. It adopts a full attack chain, from exploitation to ransom negotiation, affording them the use of a number of specialized subgroups and affiliates.
1. Initial Access
WIZARD SPIDER obtains initial access through phishing, malvertising, and exploiting services exposed on the Internet such as VPNs and RDP. They will also collaborate with infostealer malware operators like IcedID and QakBot to steal compromised credentials. In some instances, the victim becomes infected through TrickBot or BazarLoader, which establishes persistence prior to deploying a ransomware payload.
2. Persistence and Privilege Escalation
After successfully compromising the victim, WIZARD SPIDER utilizes PowerShell, Cobalt Strike, and PsExec to employ lateral movement tactics. Persistence capabilities are established by creating domain accounts, modifying registry entries, and creating scheduled tasks. WIZARD SPIDER displays a high level of adaptability leveraging legitimate tools such as AnyDesk or Atera to gain and maintain a covert remote control over the victim’s environment.
3. Command and Control (C2)
The group employs encrypted HTTPS, TOR hidden services, and are layered behind a proxy in C2 communications. Infrastructure reuse is typical; however, domains and IPs are changed often to evade detection. In 2022, WIZARD SPIDER moved many of its operational capabilities to decentralized RaaS hosting and encrypted coordination via Telegram.
4. Malware and Toolset
WIZARD SPIDER deploys:
– TrickBot: Originally developed as a banking Trojan where its intended purpose transitioned to a modular loader.
– BazarLoader / BazarBackdoor: A loader and backdoor used to stealthily deploy Cobalt Strike and ransomware.
– Cobalt Strike: Used for reconnaissance and lateral movement this is a key tool used by WIZARD SPIDER.
– All versions of Ryuk, Conti, and Black Basta Ransomware: Successive generations of ransomware families that WIZARD SPIDER managed or exercised influence over.
– AnchorDNS / AnchorMail: More sophisticated C2 frameworks used for persistence and stealthy operation.
The group continuously improves its toolset, implementing obfuscation, signed binaries, and living-off-the-land tactics to minimize endpoint detection.
5. Data Exfiltration and Extortion
Prior to data encryption, WIZARD SPIDER routinely exfiltrates sensitive data via Rclone, Mega, or scripts written for FTP for data transfer. The group follows the data exfiltration with the threat of exposure through leaking the victim’s data through a publicly accessible leak sites as an example, Conti News blog, and subsequently through the recently rebranded portals from Black Basta and Quantum operations. This “double extortion” method of operation, encrypting the victims’ data and threatening public exposure of said data to maximize ransom payments.

Notable Operations
Over the last decade, WIZARD SPIDER has been responsible for multiple ransomware attacks and has been involved in infrastructure disruptions, all of which has displayed impressive resiliency.
- 2018– Ryuk Campaigns: The group began large scale Ryuk ransomware attacks targeting U.S. hospitals and city governments. Ryuk became infamous for demanding multi million dollar ransoms, and ceased to be able to render even emergency services inoperable.
- 2020 – Conti RaaS Model: WIZARD SPIDER released Conti ransomware under a RaaS agreement, that allowed the organization to recruit affiliates in order to increase their ransomware attacks. Conti led to hundreds of attacks in different countries, including the attack from the Irish Health Service Executive (HSE) in 2021.
- 2021– TrickBot and Emotet Collaboration: The group’s infrastructure was leveraged to deploy Emotet and IcedID loaders, bridging cooperation across attacks in the eCrime ecosystem.
- 2022 – Resilience Post-Takedown: As one of the only ransomware groups utilizing TrickBot was partially dismantled by law enforcement, WIZARD SPIDER simply redirected towards BazarLoader and AnchorMail, without any disruptions to operations.
- 2023 – Emergence of Black Basta: After Conti shut down operations, affiliates of WIZARD SPIDER took a clear interest in migrating future activities to Black Basta ransomware, continuing the targeting of very high value ransoms, as well as leaking data.
- 2025 – Healthcare and Manufacturing Attacks: The latest campaigns use phishing, supply chain vulnerabilities, and other exploits that utilize misconfigured cloud services to target healthcare facilities, logistics companies, and pharmaceutical companies.
Evolution and Structure
The WIZARD SPIDER network is not a singular cohesive entity, but instead it is a loose consortium of financially motivated operators. This works through a series of specialized channels with modules that include:
- Access Brokers: Responsible for the first compromise through phishing or exploitation.
- Intrusion Operators: Conduct lateral movement, privilege escalation, and data exfiltration.
- Negotiation Units: Manages ransom communications, and other negotiations in chat, usually through anonymized chat portals.
- Developers: Maintain the codebases for ransomware and the backend.
The modular structure allows for quick recovery when there is law enforcement intervention. When the Conti brand was exposed in 2022, the operators were quickly able to position themselves as Black Basta, Royal, and Quantum, and they all maintained similar playbooks.
WIZARD SPIDER’s collaborations with other cybercriminal groups, including TA505 (Clop), as well as EvilCorp, further extends its reach. These relationships allow for the shared resources, trading access, and overlapping targets of victims.
Strategic Impact and Defense
WIZARD SPIDER’s activity demonstrates the industrialization of ransomware. This group has shown that organized cybercrime can operate almost as efficiently as large corporations when using affiliates and black markets to increase the scale of attack.
Key Impacts:
- Economic Damage: Losses in the billions of dollars across the healthcare, logistics, and energy sectors.
- Operational Disruption: Ransomware encryption temporarily disables network operations and services in hospitals and city infrastructure.
- Cybercrime Ecosystem Expansion: The Ransomware as a Service (RaaS) model used by WIZARD SPIDER proliferated among actors, leading to today’s thriving ransomware ecosystem.
Defensive Recommendations:
- Multi-Layered Authentication: Multi-Factor Authentication (MFA) for VPN, RDP (Remote Desktop Protocol), and email accounts will limit credential-based compromises.
- Behavioral Monitoring: EDR (endpoint detection and response) and XDR (extended detection and response) solutions could help detect PowerShell abuse, usage of PsExec, or anomalous file encryption.
- Network Segmentation: Reduce the privileges of all administrators and isolate critical systems.
- Incident Response Preparedness: Establish offline backups and a tested recovery plan for ransomware.
- Threat Intelligence Sharing: Engage across ISACs (Industry Share Analysis Center) in your sector to track emerging variants with shared Indicators of Compromise (IOCs).
Conclusion
WIZARD SPIDER continues to be a cornerstone of the global ransomware ecosystem. Its ability to be resilient through many highs and lows, it’s organizational maturity, and its collaboration with other eCrime groups means it continues to live on after many users have been taken down and arrested. The organization continuously retains a presence in ransomware operations and maintains continuity, but also confusion in defenders by rebranding their operations. This has been done from Ryuk to Conti and Black Basta, but nevertheless WIZARD SPIDER is still the face of ransomware to this day.
As we enter 2025, WIZARD SPIDER is perfectly positioned as a symbol of professionalized cybercrime – a shadow industry with hierarchies, specialization, and a global reach. Combatting these groups takes more than simply the installation of technical defenses, but requires international cooperation, revoking and sanctioning their financial infrastructure, and stopping the economy behind the cybercriminal elements.intent and technical sophistication.
You can download and review the sheet for all the details!







