A newly identified vulnerability (CVE-2024-3596), dubbed “BlastRADIUS,” has been discovered in the RADIUS protocol, posing a critical risk to network security. Researchers from the University of California, San Diego, have published a practical exploit for this flaw, marking the first successful demonstration of an attack against the RADIUS protocol. The FreeRADIUS Server Project has promptly responded with guidance and updates to mitigate this significant threat.
Nature of the Attack
- The attack exploits a fundamental design flaw in the RADIUS protocol.
- All standards-compliant RADIUS clients and servers are likely vulnerable.
- Classified as a Man-in-the-Middle (MITM) attack, it requires the interception and modification of Access-Request packets.
Mitigation Measures
The FreeRADIUS Server Project has provided the following recommendations to secure systems:
Immediate Configuration Changes
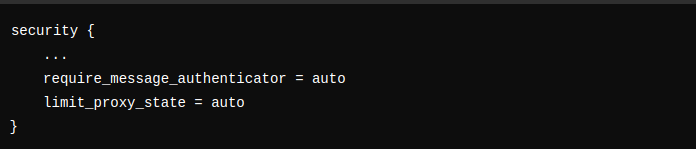
- Enable
require_message_authenticator = truein all client definitions. - This flag has been available since version 3 but was not enabled by default.
- Ensures systems using FreeRADIUS are not vulnerable to the BlastRADIUS attack.
Specific Measures for NAS and Proxy Clients
- For NAS clients (non-proxy devices): Update client definitions to include
limit_proxy_state = yes. - For proxy clients (other RADIUS servers): Ensure the
require_message_authenticatorattribute is present in all Access-Request packets and upgrade other RADIUS servers to prevent the attack.
Conclusion
The discovery of CVE-2024-6387 underscores the importance of diligent cybersecurity practices and the necessity of safeguarding and continuously monitoring systems. Organizations must act promptly to patch vulnerable systems and strengthen their security posture to mitigate the risks associated with this severe vulnerability.
Recommendations
While the BlastRADIUS vulnerability (CVE-2024-3596) requires a man-in-the-middle position, implying a network may already be compromised if exploited, immediate action is crucial. FreeRADIUS users are advised to implement the recommended configuration changes and stay updated with the latest security guidance to protect their networks.






