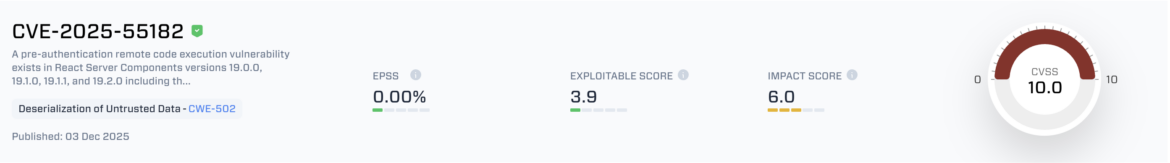
React2Shell (CVE-2025-55182 / CVE-2025-66478) is a critical deserialization vulnerability in React Server Components that enables remote code execution across Next.js deployments, quickly emerging as one of the most consequential security events in the modern web ecosystem. This article examines the five days following React2Shell’s public disclosure—how exploitation accelerated, how threat actors adapted their techniques, and why the risk expanded far beyond initial expectations. In a landscape where the transition from disclosure to active compromise happened almost instantly, React2Shell has become more than a single vulnerability; it is a systemic warning for the entire industry.
What CISOs Need to Know Now
Five days after the disclosure of React2Shell (CVE-2025-55182 / CVE-2025-66478), the situation has shifted from a theoretical supply-chain concern to a fully active, multi-actor exploitation wave. What began as a quietly patched deserialization flaw in React Server Components is now one of the most consequential security events the modern web ecosystem has faced since Log4Shell.
The uncomfortable truth: the window for silent, preventative patching is long gone.
We are now dealing with real intrusions, real credentials stolen, and real post-exploitation activity across the internet.
What Has Changed by Day 5?
Full transition from disclosure → weaponization → active compromise
The initial “responsible disclosure period” lasted barely hours. We now observe widespread exploitation across:
– Opportunistic botnets
– Financially motivated actors launching miners
– State-aligned APT groups treating React2Shell as a high-fidelity entry point
China-nexus groups such as Earth Lamia and Jackpot Panda were among the first to adopt the exploit, an indicator that this vulnerability is being treated as a strategic foothold opportunity.
Default Next.js deployments are vulnerable out of the box
React2Shell is a zero-config compromise. A default create-next-app build exposes the vulnerable RSC endpoint without the developer writing a single Server Action.
This dramatically expands the attack surface across SaaS vendors, media platforms, fintech environments, and startups relying on Next.js for rapid delivery.
WAFs are repeatedly bypassed
Day-2 managed rules from major cloud providers slowed down only the most basic scans.
Attackers are now using:
– Chunk reordering inside Flight protocol streams
– Unicode escaping
– JSON structure manipulation
– Keyword-free payload variants
…to walk past signature-based WAF controls with ease.
If a company is relying on WAF rules instead of patching, they are already compromised or will be.
Attack patterns have evolved beyond miners
Early exploitation focused on reconnaissance and cryptomining. Day 3–5 shows a clear escalation:
– Sliver C2 deployments
– MeshAgent installs disguised as legitimate remote management
– Environment variable dumping for cloud key harvesting
– Attempts at persistence on compromised containers
This is no longer “hit-and-run RCE.” It is long-term access preparation.
The biggest risk is not RCE itself — it’s stolen secrets
Once inside a Next.js server, attackers can access process.env, which often includes:
– AWS IAM keys
– Database credentials
– Stripe / Twilio / SendGrid API keys
– JWT signing secrets
– Session secrets
Patching the vulnerability does not invalidate secrets stolen on Day 1–4.
This is the core message for Day 5:
Rotate your secrets, or assume breach.
What Organizations Must Do Right Now
Patch, rebuild, redeploy
Upgrading dependencies is not enough — the patched RSC code must be rebuilt into the production artifact.
Rotate all secrets
Any organization patched after December 4 should treat secrets as compromised.
Hunt for indicators of compromise
Look for:
– Node.js processes spawning shells
– Outbound connections to known C2 IPs
– Modifications under /tmp
– Suspicious new .js files
Stop relying on WAF filtering
WAFs reduce noise, not risk.
Treat this as a supply-chain event, not a simple CVE
The industry is collectively relearning that frameworks can become single points of systemic failure.
Day 5 Takeaway
React2Shell is no longer a theoretical vulnerability — it is an active mass-compromise event. APTs, botnets, and ransomware affiliates are all converging on the same entry point, and the organizations that delay patching or secret rotation will carry the highest long-term exposure.
– Patch the code.
– Rotate the keys.
– Hunt the network.
The vulnerability may be in the framework, but the risk is now in the credentials.







