WPBakery Page Builder Plugin’s Vulnerability Affects 1.6 Million WordPress Sites
The WordPress plugin, which allows editing and customizing WordPress pages without writing any code, is vulnerable to a vulnerability that could allow file uploads without authentication. Threat actors are hacking campaigns targeting approximately 1.6 million WordPress sites through this vulnerable plugin.
The critical vulnerability, tracked as CVE-2021-24284, allows an unauthenticated threat actor to inject malicious Javascript code into sites using any version of the plugin, resulting in a complete site takeover. Additionally, a trojan malware called NDSW is deployed that will redirect visitors to phishing and harmful advertising pages by injecting malicious code into legitimate Javascript files.
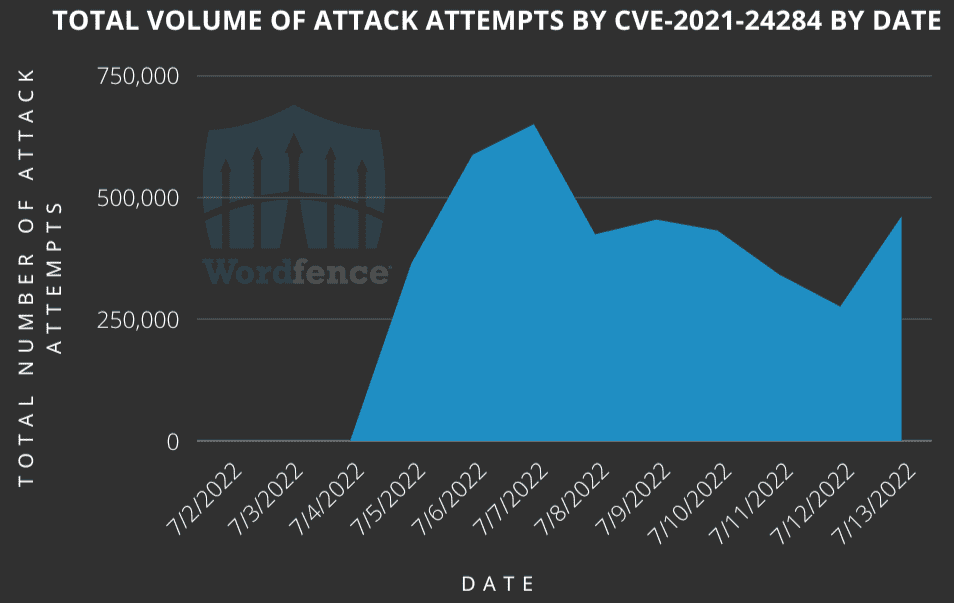
In addition, even if the plugin is not used, it is recommended that the IP addresses detected in the attack campaign be blocked from the security devices in use.
Premint Security Breach Caused 314 NFTs Hijacking
It has been detected that the Premint platform, which NFT artists and collectors widely use, was compromised by threat actors on July 17, 2022, and 314 NFTs were hijacked.
According to the statement made by blockchain security firm CertiK, the breach was committed by threat actors by injecting malicious JavaScript code into the Premint web application (premint.xyz). This malicious Javascript code enables visitors and collectors to approve the “setApprovalForAll” function in connecting their crypto wallets (MetaMask, Coinbase, WalletConnect) to the compromised website. The “setApprovalForAll” function requests the ability to access and modify user funds by showing the token’s contract address. If the user approves, threat actors can access the crypto assets of the targets.
Six accounts were directly affected by the said attack, and 275 ETH cryptocurrencies worth approximately $375,000 were seized. Here are some security steps to consider in order not to be affected by similar security breaches;
- The login information used in crypto wallets should be created using unique and strong policies.
- Direct NFT trading should not be performed with wallets containing crypto assets. In this process, assets should be distributed using different wallets.
- Cryptocurrency wallets should not be connected to platforms unsure of their reliability.
- Finally, care should be taken not to have any other browser add-ons in browsers with crypto wallets used as browser add-ons, such as Metamask.
MageCart E-Skimmer Attacks Targeted 311 Restaurants in the USA
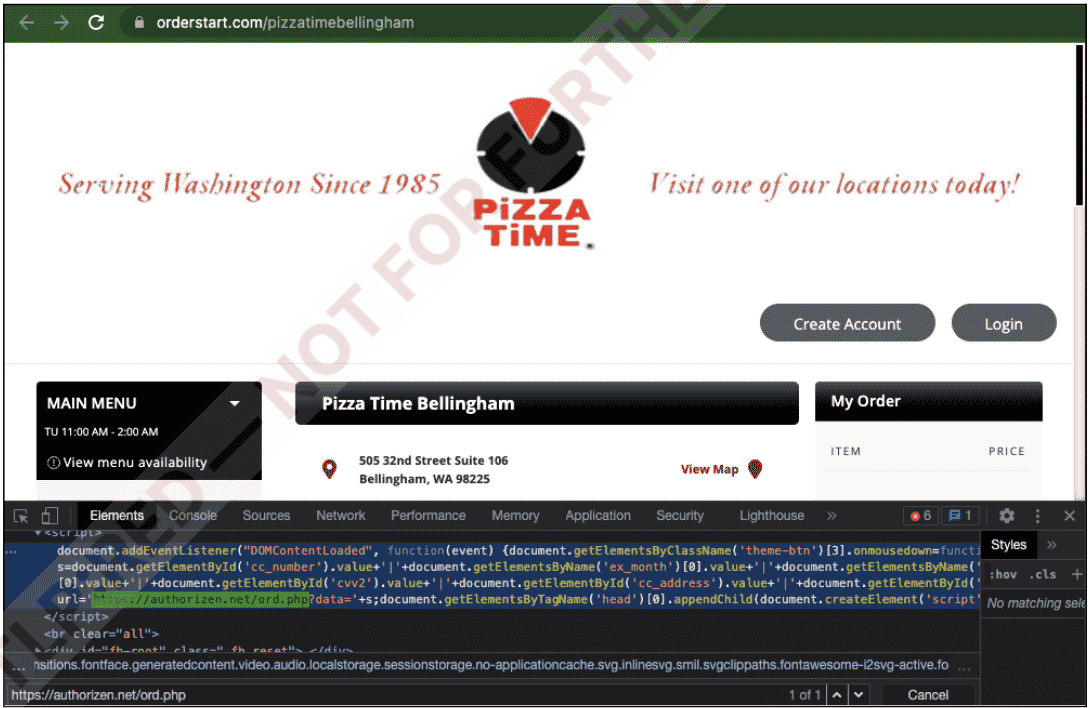
With the MageCart e-skimmer campaigns targeting three online ordering platforms, MenuDrive, Harbortouch, and InTouchPOS, bank card information of 50,000 customers of 311 restaurants serving in the USA was seized. Online ordering platforms for restaurants allow customers to order food online and outsource the burden for restaurants to develop an ordering system. Due to its widespread use, online ordering platforms have become a high-value target for threat actors carrying out Magecart e-skimmer attacks. Magecart malware is JavaScript code that collects credit card data and other identifying information when online shoppers enter the payment page.
The campaign started on January 18, 2022, targeting 80 restaurants using MenuDrive and 74 restaurants using the Harbortouch platform. InTouchPOS, on the other hand, was targeted by another MageCart campaign on November 12, 2021, which resulted in e-skimmer infections in 157 restaurants using the platform. It was observed that 50,000 bank card information seized in the campaign, which affected 311 restaurants in total, was put up for sale on Dark Web platforms.
Advanced digital security technologies must be used to prevent Magecart attacks. Data Breach Monitoring services are a preferable solution to protect e-commerce sites against potential breaches. Additionally, for e-commerce providers, It is recommended to ensure that the software, hardware, and tools being used are up-to-date, request third-party service providers to have their code checked, and apply HTTP Content-Security-Policy principles which provide an additional layer of protection against potential attacks. The precautions that customers using e-commerce services should take in order not to be affected by similar security breaches are as follows;
- Personal information should not be entered on unreliable/suspicious websites,
- Virtual cards created for e-commerce transactions should be used,
- Make sure that the visited page is not a fake domain with a similar name created by threat actors,
IOC findings such as IP addresses and domains known to be used by threat actors in these campaigns should be blocked from security solutions in use.






