Introduction
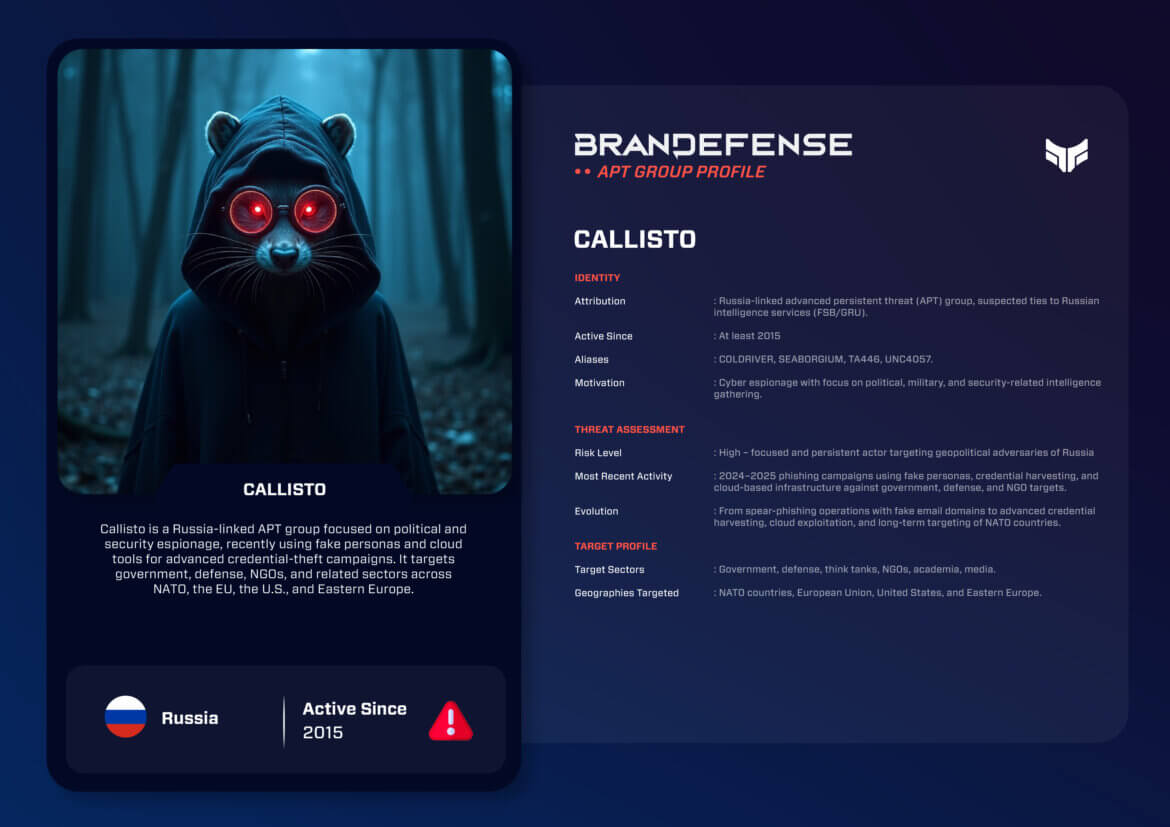
The Callisto Advanced Persistent Threat (APT) group, also called COLDRIVER, SEABORGIUM, TA446, and UNC4057, is one of the most established espionage-focused actors attributed to Russia. Since at least 2015, Callisto has consistently targeted governments, defense institutions, think tanks, NGOs, and academia, particularly those linked to NATO and European security policy.
Unlike ransomware crews or financially motivated adversaries, Callisto’s purpose is intelligence collection over the long term in support of Russian strategic goals. Callisto’s typical techniques focus on credential harvesting, spear-phishing with impeccable lures, and abusing cloud technology to maintain persistence.
This blog considers Callisto’s identity, tactics, notable operations, and the wider ramifications of its campaigns against international security.
Identifying & Motivating Factors
• Attribution: Russia-based with suspected links to Russian intelligence services FSB / GRU.
• Active Since: 2015 and earlier.
• Aliases: COLDRIVER, SEABORGIUM, TA446, UNC4057.
• Motivation: Espionage and long-term collection of intelligence against those political actors deemed geopolitical adversaries to Russia.
Callisto is not driven by financial benefits. Its purpose is to obtain sensitive information and data, primarily diplomatic communications, military plans, discussions related to sanctions, and conversations about policy. Information gained from this intelligence can help improve Russia’s negotiating position and situational awareness in world affairs.
TTPs: Techniques, Tools, and Persistence
Initial Access
• Spear-phishing: Highly tailored phishing campaigns that appear legitimate. The emails may impersonate members of the press, academicians, or political analysts.
• Credential-harvesting sites: Fake log-in portals that steal email and collaboration credentials.
• Watering-hole compromises: Infrequently compromising a policy-relevant independent website to direct the target to confirmation malware.
Persistence
• Web shells on compromised servers for long-term control.
• Service accounts and scheduled tasks for a stealthy presence.
• Abuse of legitimate remote management tools and backup software to camouflage to normal operations.
Command & Control (C2)
• Encrypted HTTPS traffic for exfiltration of the data.
• Domain fronting and Cloud-Hosted redirector pages to camouflage C2 communications.
• Exploited infrastructure used as staging locations.
Malware & Tools
• Light-weight custom backdoors for foothold operations.
• Credential-harvesting kits used during phishing operations.
• PowerShell loaders and others with abuse of Living-off-the-land-binaries (LOLBins).
• Utilities for mailbox exports, as well as targeted data gathering.
Techniques
– Person-based social engineering: Callisto places considerable resources into crafting believable personas, which remain active for several years.
– Short-lived infrastructure: Callisto frequently rotates domains and servers to limit detection.
– Targeted exfiltration: Rather than a random act of data theft, Callisto instead focuses on specific high-value datasets.
Target Profile
– Sectors: Government ministries, foreign affairs departments, defense contractors, diplomatic missions, NGOs involved in security and sanctions, think tanks, and academic research institutions.
– Geographies: NATO member states, European Union countries, the United States and Eastern Europe. The Middle East and Central Asia may also be targeted occasionally based on geopolitical relevance.
The continuing fixation on NATO and EU institutions indicates Callisto’s alignment with Russian state interests.

Notable Operations
2015-2017: Initial credential-harvesting operations targeting Eastern European diplomats and policy researchers. Developed long-term personas to lend credibility to spear-phishing attacks.
2018-2019: Extending to NATO-affiliated networks. Web shells were employed, and phishing operations evolved to compromise access to governmental portals and email accounts.
2020-2021: COVID-19-themed lures were used to capitalize on discussions regarding health policies and international travel. Targets were expanded to include NGOs and other policy researchers.
2022-2023: Use of OAuth consent-based phishing resulted in compromised access visiting cloud accounts as well as the acquisition of long-lived tokens. This access resulted in Callisto being able to access compromised mailboxes and collaboration software.
2024-2025: Returns focus to NATO-affiliated organizations and diplomats. Infrastructure characterized by quick churn, cloud-based redirectors, and ongoing credentials theft.
Recent Developments (2024–2025)
Callisto has evolved to fit contemporary security contexts:
- Cloud-Focused Operations: We are seeing increased reliance on compromising cloud accounts, especially through phishing for OAuth consent.
2. Infrastructure Rotation: Domains and C2 servers turn over within days, meaning it is more difficult to detect and take down.
3. Frequent Credential Theft: Phishing and fake portals continue to be used to gain access to credentials, which shows that even the most defended organization can be subject to successful cyber intrusion.
4. Policy-Driven Targeting: Callisto campaigns track international crises, such as NATO coordination efforts and sanctions regimes.
Strategic Impact
– Geopolitical Intelligence: Callisto provides insights into Western diplomacy, sanctions, and defense policy to Russia.
– Influence on Policy: Stolen information can inform adversaries for preemptive, counter, or manipulative effect.
– Security Risk: Compromise of email and collaboration tools can provide opportunities for disinformation operations and long-term surveillance.
– Operational Persistence: Callisto maintains long-term visibility into adversary decision-making through covert persistence.
Defensive Takeaways
Organizations can help address the threats originating from Callisto by:
– Implementing phishing-resistant MFA (e.g., FIDO2 tokens).
– Monitoring OAuth grants, and permissions on cloud accounts.
– Actively hunting for web shells and anomalous service account behavior.
– Leveraging EDR/XDR to identify the misuse of LOLbins and PowerShell commands.
– Implementing segmentation and least-privilege access controls on email/document repositories.
– Sharing information and intelligence among governments, CERTs, and private sector organizations in order to disrupt ongoing campaigns and adapt to changing tactics.
Conclusion
As of 2025, Callisto is still one of the most persistent Russian espionage groups. Its desire for credential theft, exploitation of cloud services, and long-term, persistent, and pervasive infiltration of NATO-aligned targets will continue to make it a reputational threat for many organizations and an international security threat. Callisto has demonstrated an amazing amount of adaptability and patience, investing years in long-term personas and infrastructure to accomplish its objectives despite years of exposure.
In 2025, Callisto is a perfect example of the challenge presented by modern espionage: a low-profile, persistent, and focused adversary operating at the intersections of technology and geopolitics. Defending against Callisto requires not just appropriate technical controls and mitigations but an understanding of Callisto’s strategic objectives and tradecraft as it continues to evolve and improve.
You can download and review the sheet for all the details!

Want to identify and disrupt APT-driven credential theft before it escalates?
👉 Discover how Brandefense delivers actionable threat intelligence across surface, deep, and dark web.






