Overview
Ransomware attacks increase every year, causing significant financial and reputational damage to companies, the multi-extortion trend adopted and frequently used by threat actors is seen in almost every attack attempt.
While a few high-profile bands that made their mark in 2021 disappeared, it didn’t take long for new ones to arrive. Groups such as Sodinokibi/REvil, Darkside, Blackmatter, and Avaddon have not observed operations since 2021. Unfortunately, these groups’ stopping the attacks did not cause a decrease in ransomware attacks. On the contrary, it resulted in the emergence of new ransomware groups, and they succeeded in carrying out effective attacks on giant companies operating in various sectors.
Some of the groups that are new to the ransomware scene and pretty active are called Lockbit, Lapsus, and Stormous. In addition to these groups, there have been ransomware groups in existence and activity for a long time. Some of the most active groups were determined as Conti and Cl0p.
Ransomware groups are observed to use various toolkits such as malware, legitimate software, and operating system functionalities to carry out their attacks and maintain their persistence. We have shown the incidence of these toolkits in the table below.
| TTP | % |
| PsExec | 34% |
| Cobalt Strike | 18% |
| Mimikatz | 11% |
| VssAdmin | 10% |
| NetScan | 7% |
| BITSAdmin | 4% |
| PowerShell | 5% |
Table 1: Toolsets Most Used by Ransomware Groups
Ransomware Groups
Conti
The ransomware gang called Conti started its activities in 2020 and continues its operations at an incredible pace today, and it is connected to central Russia. Although the primary team of Conti has a total of 62 members, it has been determined that the group is led by the pseudonyms Stern and Demon. In addition, we have thought that the number of people connected to the group has increased to about 100.
The malware used by the group can infect all versions of the Windows operating system, and the known methods for the group to distribute their malware and gain initial access are listed below:
- Phishing emails with malicious file attachments and malicious links
- Weak or stolen Remote Desktop Protocol (RDP) credentials
- Fake software delivered through search engine optimization
- Common security vulnerabilities
- Collaboration with other malware distribution networks (e.g., Zloader)
Conti frequently uses the DarkWeb network and discloses information about the organizations they target on the website served over the Tor network.
Lockbit
Lockbit is one of the most active ransomware groups that started its activities in 2019 and continues its operations today. Lockbit, which began its activities as ABCD ransomware, serves with the Ransomware-as-a-Service (RaaS) model. In other words, threat actors get the right to use Lockbit ransomware by paying a rental fee. In addition, the income obtained is shared between the attacker and the developers at specific rates.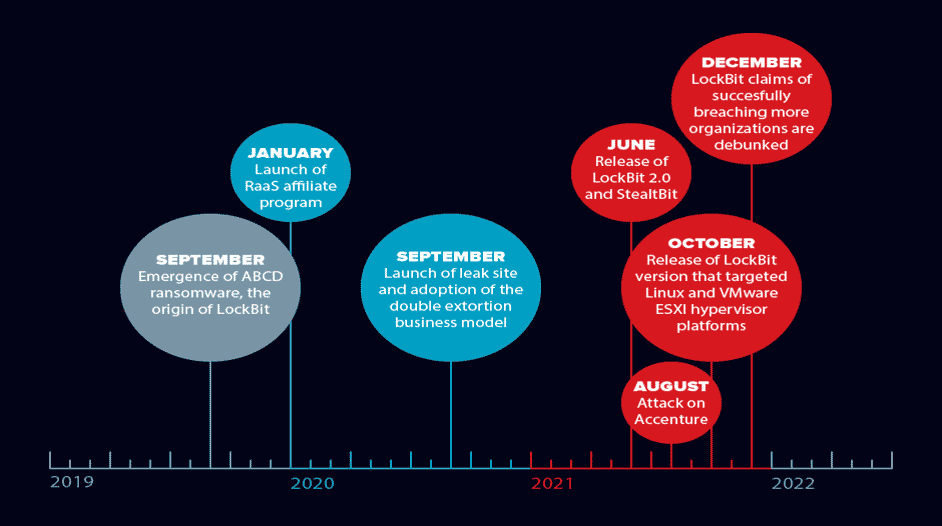
The Lockbit gang also uses a Tor-served website to make announcements about infected organizations.
Cl0p
Cl0p is a ransomware group first detected by MalwareHunterTeam in 2019, and its activities continue intensely today. Cl0p ransomware can run on all Windows operating system versions. Cl0p is part of the CryptoMix ransomware family, and they targeted English-speaking targets. Although it is not officially affiliated with Russia, such indicators suggest that it is a Russia-based group. The Cl0p has targeted more organizations rather than individual users. In addition, the final payload of the Cl0p ransomware was also used by an APT group called TA505.
Like others, Cl0p uses its website, which is served over Tor, to announce the organizations they operate and to share information.
Stormous
The Stormous ransomware group first emerged at the beginning of the tension between Russia and Ukraine and started its activities by stating it was with Russia. Then, announcing that it cooperates with Conti, it carries out attacks with the Conti, which attacks targets against Russia.
Many ransomware groups are heavily operated via Telegram instead of using an announcement site served over the Tor network, but they also have a website on the Tor network. However, the website in question is inactive, and when it is active, no sharing is made yet.
Notable organizations that the Stormous group has managed to include in its target list include Epic Games and the Ministry of Foreign Affairs of Ukraine.
Lapsus$
Lapsus$ was first spotted in the ransomware arena in December 2021. With the start of its operations, Microsoft, Samsung, NVIDIA, Okta, and the Brazilian Ministry of Health. They have targeted industry giants and government institutions and use the double-extortion tactic, which they threaten to release if the requested ransom amount is not paid by leaking sensitive data from the target organization. Although its targets so far are the United Kingdom and South American countries, its operations are expanding even more in a short time.
However, as an exception, they do not perform the operations performed by traditional ransomware groups, such as file encryption and blocking of access to the system.
Lapsus$ does not have the website served on the Tor network as many other ransomware groups do. Instead, an announcement is made through the Telegram channel, which is another most preferred alternative.
That is not the only feature that distinguishes Lapsus$ from other ransomware groups. Many characteristic traits of ransomware groups are not available in the Lapsus$ ransomware group.
Ransomware Monitoring
We listed the processes below associated with ransomware can be combined under the term “Monitoring”:
- Monitoring the movements of ransomware groups (influenced organizations and shared information, etc.)
- Identifying the ransomware type that infected the system
- Detecting existing decryption/recovery directives
No More Ransom Project
It is a project created in collaboration with the Dutch police’s National High-Tech Crime Unit, Europol’s European Center for Cybercrime, Kaspersky, and McAfee to ensure that affected users can recover files against ransomware threats without paying a ransom. Additionally, it aims to educate about how ransomware works and the precautions that can be taken to prevent the system from getting infected.
The No More Ransom Project provides a service to assist you in identifying which ransomware you have been infected. It accomplishes this service by using samples of files created or encrypted by the ransomware. With this useful functionality, you can inquire about the detected ransomware by using the “Decryption Tools” page to query whether a decryption tool is included in the relevant group.
ID Ransomware
Another service created by various security researchers known as MalwareHunterTeam, which tries to detect the type of ransomware that infects the system, is the ID Ransomware project.
You can query using the ransomware note, encrypted file samples, or any contact addresses included in the ransom note. If you come across decryptable ransomware, it will direct you to a link with follow-up instructions for decryption.
Monitoring Announcement Sites
One of the common characteristics of many ransomware is to have an announcement site where they publish various information about the organizations they target and about them. These sites are served on the Tor network and cannot be accessed using traditional browsers. Therefore, a fundamental approach to tracking the movements of a ransomware group is to visit these announcement sites to check for new organization entries. This approach is known as Web Scraping. It relies on visiting announcement sites using a Tor proxy, parsing the pages’ HTML tags, and extracting the needed fields.
There are some projects using this method, and Telegram channels are offering it as a service. Some of these are listed below:
- https://github.com/captainGeech42/ransomwatch
- https://github.com/thetanz/ransomwatch
- https://t.me/ransomwatcher
who’s been ransomware’d
Another monitoring service is the website, where you can check if any ransomware group has hacked an organization. ransom.wiki helps you identify both the organizations affected by querying the ransomware group name and determining which group was attacked by querying the organization name.
Conclusion
Ransomware is an ever-increasing threat, from individual users to industry giants and government agencies. By using the services mentioned here, you can get the chance to recover your files without meeting the ransom payment demands of the attackers. At the same time, you can educate yourself about ransomware and follow the movements of these groups to make inferences about the motivation of the attackers, the countries they target, and the sectors.






